![NextGen FireWall - Banner [Center-aligned Media] - BG Image NextGen FireWall - Banner [Center-aligned Media] - BG Image](https://images.contentstack.io/v3/assets/blt38f1f401b66100ad/blt9ed5b4df9c5a70e7/68c8ec55d6e5001ff3e1c95c/c393a35269dffcf0f567807c29ac2ce5b6fbd817.webp?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Sophos Firewall
Much more than a firewall.

Consolidate your network protection with our integrated and extensible platform to secure your hybrid networked world.
What you get:

Automatic response to active threats

Powerful protection and performance

Work from anywhere, safely and securely

Managed through a single console
How people work has changed. Has your firewall?
Consolidate your cybersecurity
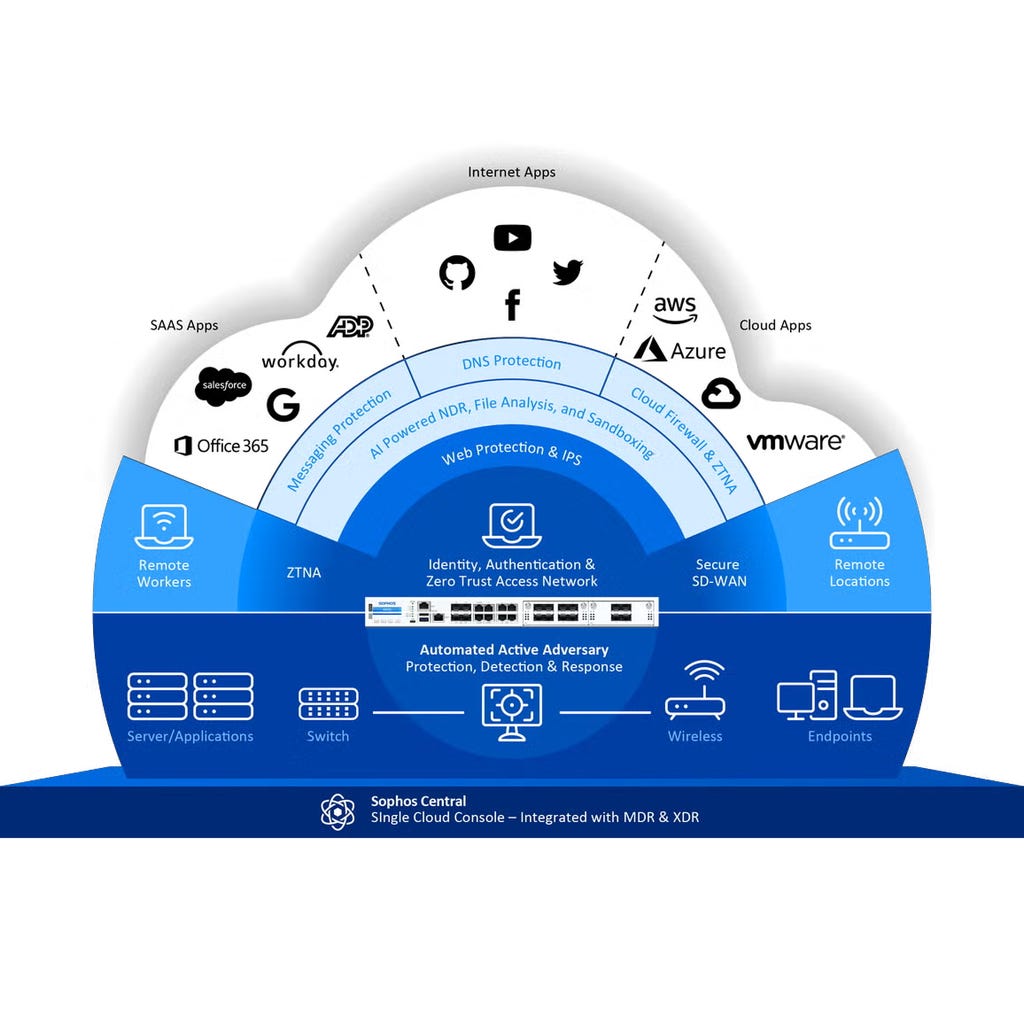
Sophos Firewall is much more than a firewall — it's the heart of the world's best network security platform. Consolidate and simplify your cybersecurity with a single vendor, cloud management console, and agent.
.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Sophos Firewall includes more than any other firewall:
- Full next-gen firewall optimized for the modern encrypted internet, offering industry-leading price per protected Mbps and the best value.
- Unique detection and response capabilities that make it ideal for MDR or XDR service integration.
Active Threat Response and Synchronized Security stop threats before they cause a serious problem.
- Comprehensive built-in SD-WAN and ZTNA capabilities that easily support a remote workforce or distributed locations.
- Full integration with our cloud-delivered network security platform including Zero-Trust Network Access (ZTNA), DNS Protection, Zero-Day Threat Protection, Network Detection and Response (NDR), and more – all for no extra charge.
- Cloud management and reporting from Sophos Central for managing operations across all your Sophos products including firewalls, wireless networks, switches, ZTNA, endpoints, mobile devices, servers, email protection, and more.

.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Need more than a firewall?
Consolidate your network security with our Network-in-a-Box solution bundles.
Active threat response
Stop active threats dead in their tracks
Sophos Firewall with Active Threat Response will not only identify and block threats on your network but also coordinate an automated response. Sophos Active Threat Response uses threat intelligence from SophosLabs, Sophos MDR analysts, or third-party sources to identify any active threat operating on your network and block it instantly.
Your firewall will then use Sophos Synchronized Security™ to coordinate with other Sophos products, such as Sophos Endpoint/Intercept X and Sophos ZTNA, and further isolate the threat to prevent lateral movement. You’ll reduce your response time from hours or minutes to seconds, stopping threats before they can spread.
- Automatically identify and block active threats.
- Prevent the lateral movement of attacks.
- Deliver immediate insights into compromised devices, users, and applications.
Unrivaled performance
The XGS Series of next-gen firewall appliances delivers Sophos Xstream-accelerated performance at every price point to power the protection you need for today’s diverse, distributed, and encrypted networks.
Powered by Xstream
The Sophos Xstream architecture accelerates and offloads your important SaaS, SD-WAN, VPN, and cloud traffic at the hardware or software level from our deep packet inspection (DPI) engine. On some models, it performs Transport Layer Security (TLS) and DPI using integrated Sophos Xstream Flow processors.
High-speed connectivity
Customize your firewall’s already versatile networking options with an extensive range of add-on modules for high-speed copper, fiber, Power over Ethernet (PoE), 5G, and Wi-Fi connectivity.
Performance by design
From the smallest entry-level device to our enterprise and campus edge models, every Sophos Firewall is custom-built to handle the most demanding workloads. Striking the perfect balance between performance, value, and efficiency, our hardware appliances unlock the high-speed connectivity you need to prevent bottlenecks and reap the full potential of your network.

Recognized as the #1 Overall firewall solution by G2 users
Xstream protection and acceleration
The Sophos Firewall Xstream architecture protects your network from the latest threats and accelerates your important SaaS, SD-WAN, VPN, and cloud application traffic.
TLS 1.3 decryption
Remove an enormous blind spot with intelligent TLS inspection that’s fast and effective. Sophos Firewalls support the latest standards with extensive exceptions customizability and point-and-click policy tools that make your job easy.
Deep packet inspection
Stop the latest ransomware attacks and data breaches using high-performance DPI with next-gen intrusion prevention (IPS), web protection, and application control capabilities. Deep learning and sandboxing powered by SophosLabs Intelix threat intelligence provide zero-day protection and threat classification.
Application boost
Accelerate your SaaS, SD-WAN, VPN, and trusted cloud traffic such as VoIP and video automatically or using your own policies, putting them on the Xstream FastPath to optimize overall performance.
Xstream SD-WAN
The latest SD-WAN capabilities in Sophos Firewall optimize network performance, flexibility, and resiliency.
Xstream FastPath acceleration
Accelerate SD-WAN IPsec VPN tunnel flows to take full advantage of the hardware crypto capabilities of our powerful XGS Series firewall appliances.
Performance-based routing
Automatically optimize traffic routing and rerouting based on real-time WAN link latency, jitter, and packet loss metrics.
Point-and-click orchestration
Easily set up complex hub-and-spoke or full mesh SD-WAN overlay networks with full tunnel redundancy in just a few clicks.
Extending network protection and performance via the cloud
Sophos Firewall leverages the Sophos Cloud to ensure that your organization is protected from the latest threats and further maximize performance.
Sophos Firewall leverages the Sophos Cloud to ensure that your organization is protected from the latest threats and further maximize performance. Multiple AI-powered deep learning models from Sophos X-Ops secure against known and never-before-seen attacks and malicious URLs. Using a common cloud, any new threat attacking a single Sophos customer is instantly shared across all our customers, blocking it everywhere. In addition, by offloading this analysis from your firewall to the cloud, your performance is boosted even further.
What you get:
Cloud-based Network Detection and Response (NDR) using AI to identify high risk domains and encrypted payloads
Instant high-speed blocking of the latest risky URLs with DNS Protection
- Protection from any new zero-day file-based threat, thanks to AI capabilities and cloud-based sandboxing, which detonate it in a safe environment.
- Secure application access to make your apps invisible to hackers while providing secure access for your remote workers with built-in ZTNA.
- Easy cloud-hosted SD-WAN tools for securely interconnecting your remote locations and public cloud infrastructure.
- A single cloud management console to manage your cybersecurity, share data and telemetry, and enable automated threat response.
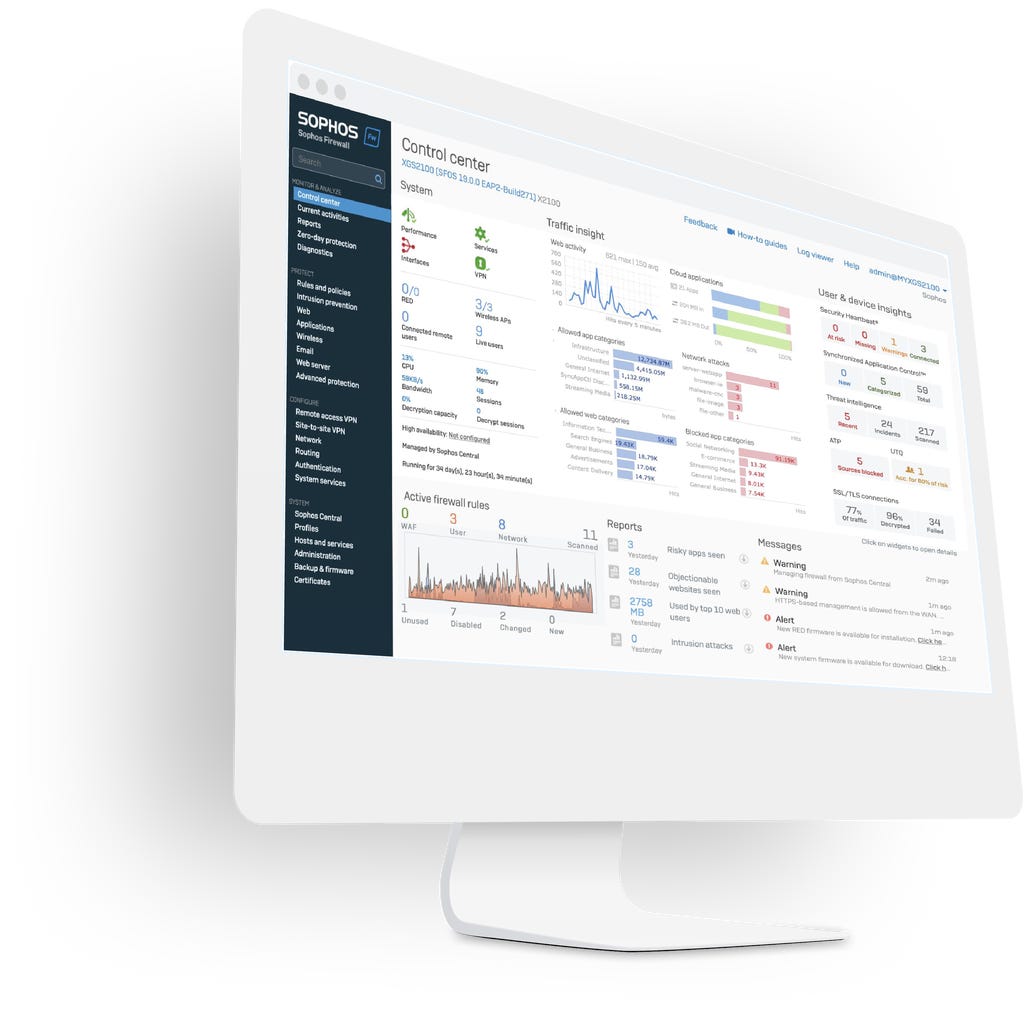
Central cloud management
Sophos Central: The ultimate cybersecurity cloud management platform.
One console to manage it all
Sophos Central provides a single cloud management console for all of your Sophos products and includes group firewall management.
Reporting in the cloud
Sophos Central maintains your firewall log data in the cloud and provides flexible reporting tools that enable you to analyze and visualize your network over time.
Zero-touch deployment
Sophos Central enables you to easily deploy new Sophos Firewalls without having to physically touch them.
Secure by Design
Your security is our top priority.
Sophos Firewall is the most secure and hardened firewall on the market that has unique features to keep your firewall and network protected against attacks.
- Sophos Firewall Health Check identifies configuration risks and recommended best practices.
- Automated over-the-air hotfix capability for security patches between regular firmware updates without downtime.
- Hardened kernel for enhanced security, performance, and scalability with tight process isolation and attack mitigation.
- Remote integrity monitoring by Sophos to detect unauthorized configuration, malicious code execution, file tampering, and more.
- Next-gen Xstream Architecture with enhanced control plane and containerization of trust boundaries.
- Encrypted and secure central management via Sophos Central, eliminating any need for remote admin access.
- Multi-factor authentication across all systems protects against credential theft and brute-force attacks.

Solutions that fit your network
Sophos Firewall adapts to your network, so you don’t need to adapt your network to your firewall. You get all the features,
versatility, and options that you need to fit your unique environment.
Don’t take our word for it
Sophos Firewall is highly rated by organizations across review sites, including Gartner Peer Insights and G2.

Recognized as the #1 Overall firewall solution by G2 users

Frost & Sullivan Competitive Strategy Leadership Award

Gartner® Peer Insights™ Customers' Choice for Network Firewalls 2024
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)









