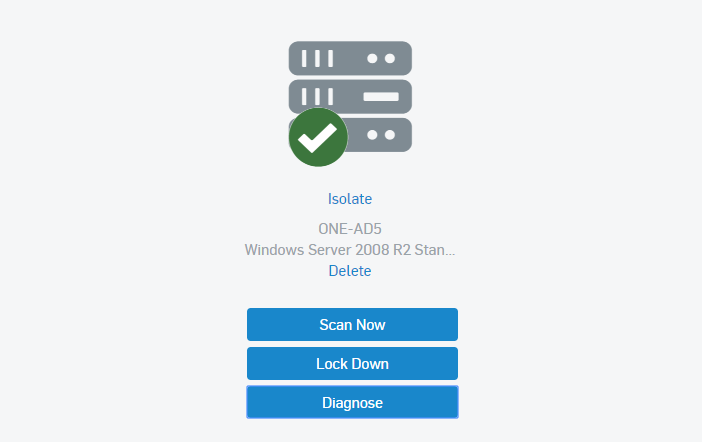
Server Workload Protection
High-impact protection with low impact on performance for on-premise, data center, and cloud workloads.


Server Workload Protection Features
Minimize Time to Detect and Respond
Sophos Cloud Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
- Extended detection and response (XDR) provides complete visibility of hosts, containers, endpoints, the network, and even cloud provider native services
- Cloud-native behavioral and exploit runtime detections identify threats including container escapes, kernel exploits, and privilege escalation attempts
- Streamlined threat investigation workflows prioritize high-risk incident detections and consolidate connected events to increase efficiency
- Integrated Live Response establishes a secure command line terminal to hosts for remediation
Integrate with Security, IT, and DevOps
Flexible, lightweight server host and container protection is optimized for performance. Available as an agent or via API for Linux to integrate with your security operations, IT, and DevOps processes.
Single Host Agent
Secure the host and container with an agent managed from the Sophos Central management console. Easily investigate and respond to behavioral, exploit, and malware threats in one place while increasing IT hygiene with automated detections, intuitive querying, and remote response capabilities.
Integrated Threat Intelligence
Fine-tuned for maximum performance, seamlessly enrich your security operations workflows with an ultra-lightweight Linux sensor providing API integration of host and container behavioral and exploit runtime detections into your existing automation, orchestration, log management, and incident response tooling.
Flexible Protection From Server to Container

Linux Security

Windows Security

Hybrid and Multi-Cloud
Block Unknown Threats
Sophos Workload Protection uses deep learning, an advanced form of machine learning that detects both known and unknown malware without relying on signatures.
Deep learning makes Sophos Workload Protection smarter, more scalable, and more effective against never-seen-before threats, outperforming security solutions that use traditional machine learning or signature-based detection alone.

Stop Ransomware in Its Tracks
Using advanced mathematical analysis of file contents, CryptoGuard detects malicious encryption wherever it takes place. Any maliciously encrypted files are automatically rolled back to their unencrypted state, irrespective of size or file type, minimizing the business impact.
Extended Detection and Response (XDR)
Sophos Intercept X Advanced for Server with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
- Cross reference indicators of comprise from multiple data sources to quickly identify, pinpoint and neutralize a threat
- Use ATP and IPS events from the firewall to investigate suspect hosts and identify unprotected devices across your estate
- Understand office network issues and which application is causing them
- Identify unmanaged, guest and IoT devices across your organization’s environment
Straightforward Licensing and Deployment
Whether you have cloud, on-premises, virtual servers, or a mix of them all, the license policy and agent deployed is the same.

.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)









 Sophos Intercept X Advanced for Server with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.
Sophos Intercept X Advanced for Server with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and IT admins.


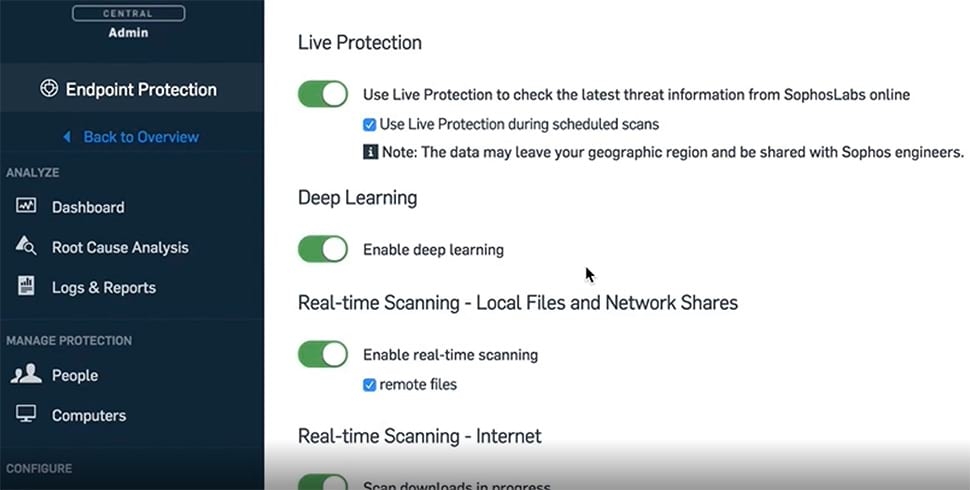

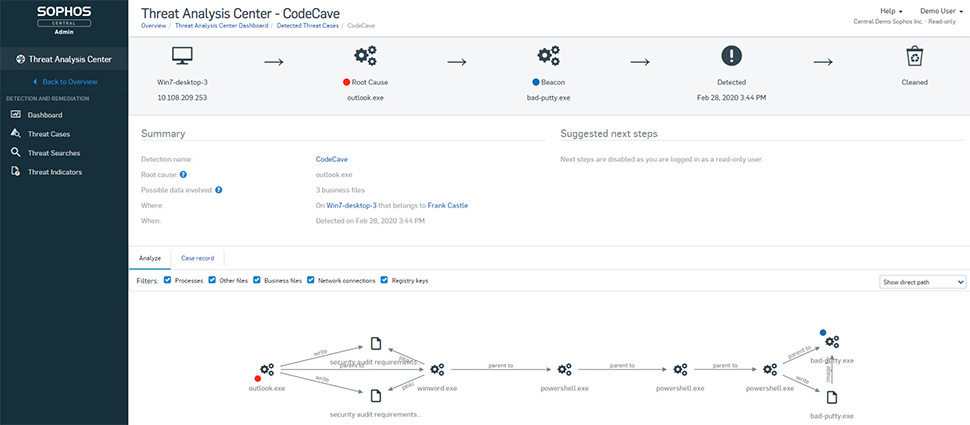

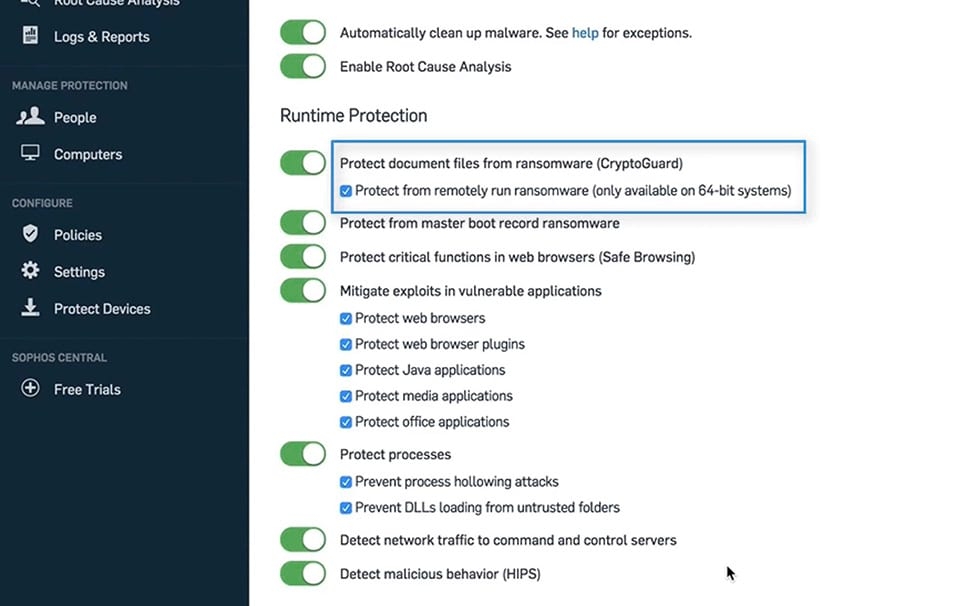 Today’s ransomware attacks often combine multiple advanced techniques with real-time hacking. To minimize your risk of falling victim you need advanced protection that monitors and secures the whole attack chain. Sophos Intercept X for Server gives you advanced protection capabilities that disrupt the whole attack chain including deep learning that predictively prevents attacks and CryptoGuard which rolls back the unauthorized encryption of files in seconds.
Today’s ransomware attacks often combine multiple advanced techniques with real-time hacking. To minimize your risk of falling victim you need advanced protection that monitors and secures the whole attack chain. Sophos Intercept X for Server gives you advanced protection capabilities that disrupt the whole attack chain including deep learning that predictively prevents attacks and CryptoGuard which rolls back the unauthorized encryption of files in seconds.