Cybersecurity as a Service for Educational Institutions
Always-on cyber protection for students, faculty, staff, and data — both on and off campus.
Keeping Schools and Universities Secure 24/7/365
From endpoint and network protection to managed detection and response, our blend of tech solutions and human-led threat hunting elevates your cyber defenses, frees up IT capacity, and adds expertise without adding headcount.
OPTIMIZE SECURITY BUDGETS
Tight budgets make it tough to secure every endpoint, upgrade or replace outdated technologies, or hire qualified personnel to tackle today's cyber threats.
With a user-friendly platform and round-the-clock Managed Detection and Response (MDR) services, Sophos provides superior cybersecurity protection — and peace of mind — without breaking the bank.
STOP PHISHING ATTEMPTS
Phishing scams are often the first way attackers sneak into an institution's network. Every time your faculty, staff, and students open an email, you're at risk!
Sophos helps you stop attacks by locking down your endpoints plus we give you the support you need to educate faculty, students, and staff on recognizing and responding to cyber threats.
PROTECT REMOTE SERVICES
In these days of hybrid learning, remote services are a vulnerable — and lucrative — entry point for cybercriminals looking to access your institution's network.
With Sophos, you have the power to control access to valuable information across your network. And you can count on us to monitor and defend your remote services 24/7.
PREVENT DATA LOSS
Cyber attackers set their sights on the education sector for its vast attack surface and valuable research assets.
Our cutting-edge AI-led technology, paired with real-time threat intelligence, works tirelessly to prevent, detect, and resolve threats across networks of any size.
GAIN CYBERSECURITY EXPERTISE
Improving your IT team's cyber expertise or asking them to do more with less is challenging when you lack staff or available talent.
Whether working alongside you — or independently — Sophos detects, monitors, and protects your network 24/7, so you can boost IT capacity without adding cybersecurity headcount.
OUR EXPERIENCE. YOUR PEACE OF MIND
With constant threats, limited control, and a jumble of single-use tools, managing cybersecurity in EDU is a colossal undertaking. You need to focus and simplify.
Sophos' cybersecurity solutions are purpose-built for education. Go turnkey or get more value from your existing investment by integrating your tools with ours for enhanced network visibility.
Sophos can help you meet CISA Cybersecurity Guidelines for K-12.
Special Education Pricing Plus E-Rate Eligibility
Sophos offers schools special discounted pricing to ensure you can deliver uncompromised cybersecurity and support uninterrupted learning while meeting the unique budget requirements of educational institutions.
Further, Sophos network protection solutions qualify for E-rate funding, further stretching budgets for U.S. schools and libraries, while protecting your network from unauthorized access to information, software, and systems.
Sophos Solutions for Education
Block Ransomware in Education
Sophos blocks ransomware, keeping your students safe and your institution up and running without fear of attack. With unique threat prevention capabilities, Sophos recognizes and stops ransomware before it takes hold. With a comprehensive suite of solutions, including Sophos Endpoint Protection, Sophos Extended Detection and Response, Sophos Managed Detection and Response, and Sophos Emergency Incident Response that all integrate and synchronize via our Adaptive Cybersecurity Ecosystem, Sophos delivers unparalleled protection and advanced threat detection, prevention, and response.
The State of Ransomware in Education 2024
Key survey findings:
- 63% of lower education and 66% of higher education hit by ransomware
- 85% of attacks on lower education and 77% of attacks on higher education resulted in data encryption
- Education reported the second-highest rate (71%) of successful backup compromise across sectors
- Exploited vulnerabilities were the most common root cause of attacks in educational organizations
- 62% in lower and 67% in higher education paid the ransom to recover data; 75% and 78% used backups for data recovery, respectively
- Average recovery cost: $3.76M in lower education and $4.02M in higher education
Block Ransomware in Education
Sophos blocks ransomware, keeping your students safe and your institution up and running without fear of attack. With unique threat prevention capabilities, Sophos recognizes and stops ransomware before it takes hold. With a comprehensive suite of solutions including Sophos Endpoint Protection, Sophos Extended Detection and Response, Sophos Managed Detection and Response, and Sophos Emergency Incident Response that all integrate and synchronize via our Adaptive Cybersecurity Ecosystem, Sophos delivers unparalleled protection and advanced threat detection, prevention, and response.
The State of Ransomware in Education 2025
Key survey findings:
- Phishing the most common technical root cause of attacks on lower education, exploited vulnerabilities most common for higher education
- A lack of expertise was the most common operational root cause of attacks on lower education, unknown security gaps most common for higher education
- 29% of attacks on lower education and 58% of attacks on higher education resulted in data encryption
- 50% in lower and 54% in higher education paid the ransom to recover data; 59% and 47% used backups for data recovery, respectively
- Average recovery cost: $2.2M in lower education (highest recorded of all industries surveyed) and $0.9M in higher education
- Increased pressure from senior leadership the most cited repercussion of ransomware attacks on IT/cybersecurity teams within the sector

Cybersecurity as a Service
IT security staff shortages, budget cuts, and a challenging recruiting climate make fighting the targeted attacks schools face difficult. With Sophos MDR, your organization is backed by an elite team of 24x7 threat hunters and response experts who take targeted actions on your behalf to neutralize even the most sophisticated threats. Should you find yourself in the middle of an incident, our Emergency Incident Response will quickly find, remove, and mitigate the attacks.
Network Security Purpose-Built for Education
Sophos Firewall and a suite of our network security solutions include features purpose-built for higher education, K-12, and primary or secondary education institutions. With built-in features and policy settings for compliance with local regulations, such as pre-defined activities like “Not Suitable for Schools” and features like SafeSearch, YouTube restrictions, and keyword filtering, Sophos helps ensure student safety online without restricting learning.
Read More:
Advanced Protection to Tackle Shadow IT
Your users may deploy unapproved apps to make their jobs easier. This leaves your network and data at high risk. Eliminate risky apps and keep everything moving without getting in the way of your day-to-day operations.
Intercept X with XDR
Intercept X with XDR gives you oversight of which apps are installed on your users’ devices. Any unsanctioned apps in use can be addressed directly – and even remotely uninstalled where necessary.
Sophos Firewall
Sophos Firewall can give priority to trusted network traffic, ensuring critical processes can continue without disruption. Plus, it gives you visibility and control of shadow IT, enabling you to identify and stop activity that may put your organization at risk.
Adaptive Cybersecurity Ecosystem (ACE)
Sophos’ adaptive cybersecurity ecosystem ensures Intercept X and Sophos Firewall work together to identify all network traffic and automatically clean up threats.
Sophos Solutions to Secure Students, Faculty, and Data
Sophos offers the industry’s broadest suite of advanced cybersecurity products and services, all integrated via our Adaptive Cybersecurity Ecosystem, and available to be managed by you or by our team of 24x7 elite threat analysts. Each standalone product is made more powerful and effective by the data shared across the platform. You choose the level of support you need to ensure you have complete protection across your entire network, right down to individual devices.
See How We Help Our Customers
Suggested Resources
Take the Next Step
Tell us what you are looking for! Let our experts at Sophos help to build the right solution for your needs.
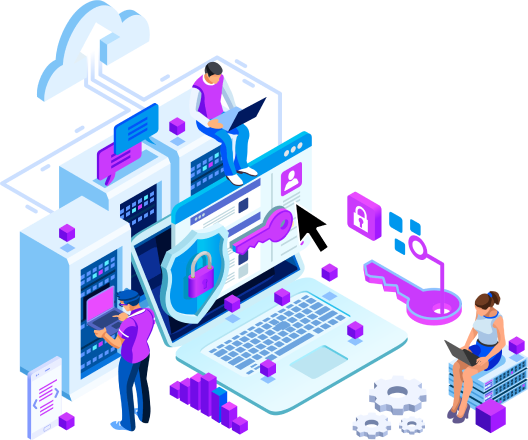
Sophos Protected Classroom
The first comprehensive cybersecurity solution designed for modern, multi-device K-12 schools

YOUR CHALLENGES
Keeping schools and universities secure, 24/7/365
From endpoint and network protection to managed detection and response, our blend of tech solutions and human-led threat hunting elevates your cyber defenses, frees up IT capacity, and adds expertise without adding headcount.
Stop ransomware in its tracks
Stop ransomware before it can compromise data and disrupt school operations.
Overcome resource gaps and budget constraints
Extend your IT department with a 24/7 team of threat response experts.
Detect attacks targeting Chromebooks
Stop attacks involving Chromebooks, security cameras, and other IoT devices.
Easily meet compliance requirements
Address compliance requirements for CIRCIA, CIPA, COPPA, FERPA, and HIPAA.
Secure student, faculty, and staff data on and off campus
With Sophos Protected Classroom, you’ll have access to a fully managed 24/7 service delivered by experts who detect and respond to cyberattacks targeting your computers, servers, networks, cloud workloads, email accounts, and more.
- Reduce the risks and costs associated with security incidents and data breaches.
- Maximize ROI and visibility across your environment by leveraging the tools and technologies you already use.
- Boost your cyber insurance eligibility and unlock discounts on qualifying solutions
- Choose the level of support you need to ensure complete protection across your entire network, right down to individual devices.
Special education pricing, plus E-rate eligibility
Sophos offers schools special discounted pricing to ensure you can deliver uncompromised cybersecurity and support uninterrupted learning while meeting the unique budget requirements of educational institutions.
With the FCC Cybersecurity Pilot Program, Sophos’ full solution portfolio is now E-rate eligible. Schools and libraries can maximize their budgets and defend against today’s evolving cyber threats.
When comparing eligible cybersecurity options, it's crucial to consider features that offer the most value and protection. Sophos solutions include unlimited incident response (IR) and remote ransomware remediation capabilities.
Sophos solutions to secure students, faculty, and data
Sophos offers the industry’s broadest suite of advanced cybersecurity products and services, all integrated via our Adaptive Cybersecurity Ecosystem, and available to be managed by you or by our team of 24x7 elite threat analysts. Each standalone product is made more powerful and effective by the data shared across the platform. You choose the level of support you need to ensure you have complete protection across your entire network, right down to individual devices.

Sophos Managed Detection and Response (MDR)
- Scalable, open cybersecurity for education IT teams
- Integrates easily with tools your institution already uses, like Microsoft Defender and Google Workspace
- Works alongside existing endpoint protection and firewall solutions to strengthen your security posture.
- Provides unlimited incident response and proactive response actions — reducing the burden on your campus IT staff.
See how we help our customers
Ransomware defense for educational institutions
For the best ransomware defense, including remote ransomware, deploy Sophos Endpoint on all your institutions devices and use Sophos MDR or Sophos XDR to detect and respond to advanced, human-led attacks. Further extend your protection with Sophos Email, Sophos Firewall, and Sophos NDR.
70% of successful ransomware attacks utilize the remote ransomware tactic according to Microsoft 2024 Digital Defense report.
The State of Ransomware in Education 2025
Key survey findings:
- Phishing the most common technical root cause of attacks on lower education, exploited vulnerabilities most common for higher education
- A lack of expertise was the most common operational root cause of attacks on lower education, unknown security gaps most common for higher education
- 29% of attacks on lower education and 58% of attacks on higher education resulted in data encryption
- 50% in lower and 54% in higher education paid the ransom to recover data; 59% and 47% used backups for data recovery, respectively
- Average recovery cost: $2.2M in lower education (highest recorded of all industries surveyed) and $0.9M in higher education
- Increased pressure from senior leadership the most cited repercussion of ransomware attacks on IT/cybersecurity teams within the sector
Sophos can help you navigate CISA cybersecurity guidelines for K-12
Learn moreSee why customers choose Sophos
Chat with our team
Learn more about how Sophos delivers comprehensive cybersecurity and easy management for K-12 environments of any size.