As we enter 2026, the threat of ransomware remains one of the most pressing security challenges facing enterprise organizations, making this a critical time to reassess exposure, preparedness, and resilience.
Sophos’ inaugural report draws on the real-world experiences of 1,733 enterprises that were hit by ransomware in 2025, providing a clear view of the current threat landscape.
The report explores how the causes and consequences of ransomware attacks have evolved, highlights the operational weaknesses that left enterprises exposed, and brings into focus the human impact of incidents, including the sustained pressure placed on IT and cybersecurity teams.
Download the report to explore the full findings.
Root cause of attacks: Exploited vulnerabilities and critical operational gaps drive ransomware incidents
Enterprises identified exploited vulnerabilities as the most common technical root cause of attacks, used in 29% of incidents. Phishing and compromised credentials followed behind, each cited in 21% of incidents.
Multiple operational factors contribute to enterprises falling victim to ransomware, with no single issue standing out as the dominant cause. An unknown security gap was cited by 40% of victims, closely followed by a lack of people/capacity and a lack of expertise, both contributing to 39% of attacks.
Interestingly, SMBs (sub 250 employee organizations) also identified a lack of people/capacity as a common factor, with 42% citing it as a key reason for falling victim to an attack, highlighting that resource constraints remain a widespread challenge regardless of organization size.
Operational root cause of attacks in enterprises
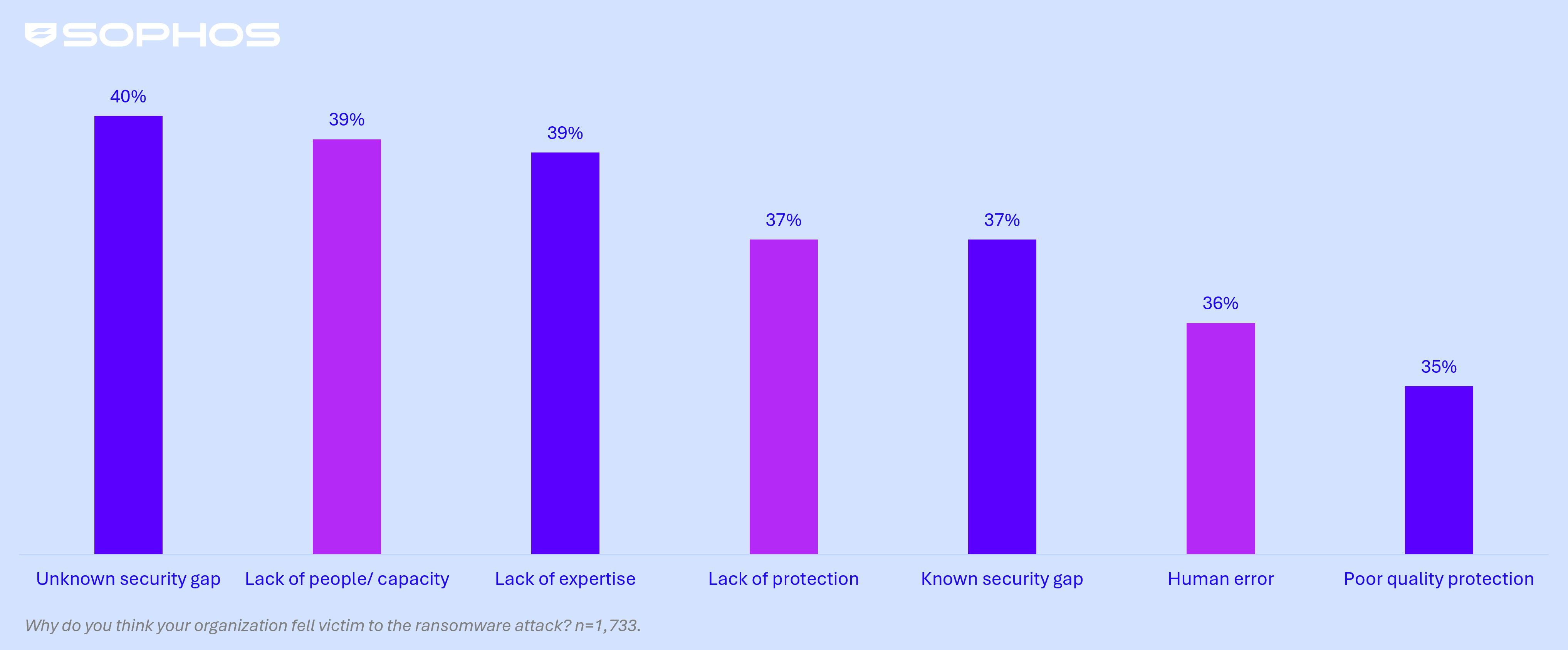
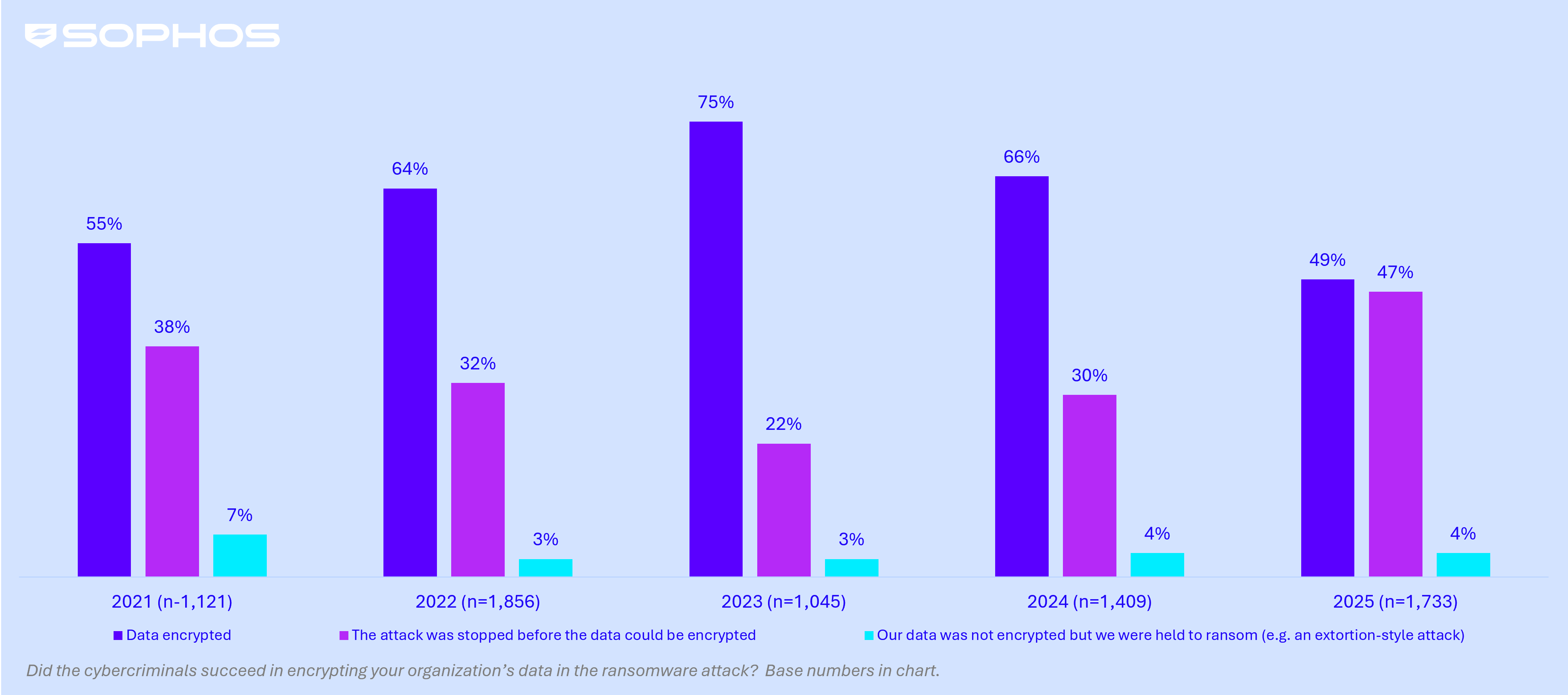
Data encryption: Rates drop to all-time low while blocked encryption attempts soar
Data encryption in enterprise organizations is at its lowest reported rate in the five years of our survey, with under half (49%) of attacks resulting in data being encrypted down significantly from the 66% reported in 2024. In line with this trend, the percentage of attacks stopped before encryption has more than doubled over the past two years, climbing from 22% in 2023 to 47% in 2025. This suggests that enterprise organizations are becoming far more effective at detecting and stopping attacks before they cause serious damage.
Data encryption in enterprise | 2021 - 2025
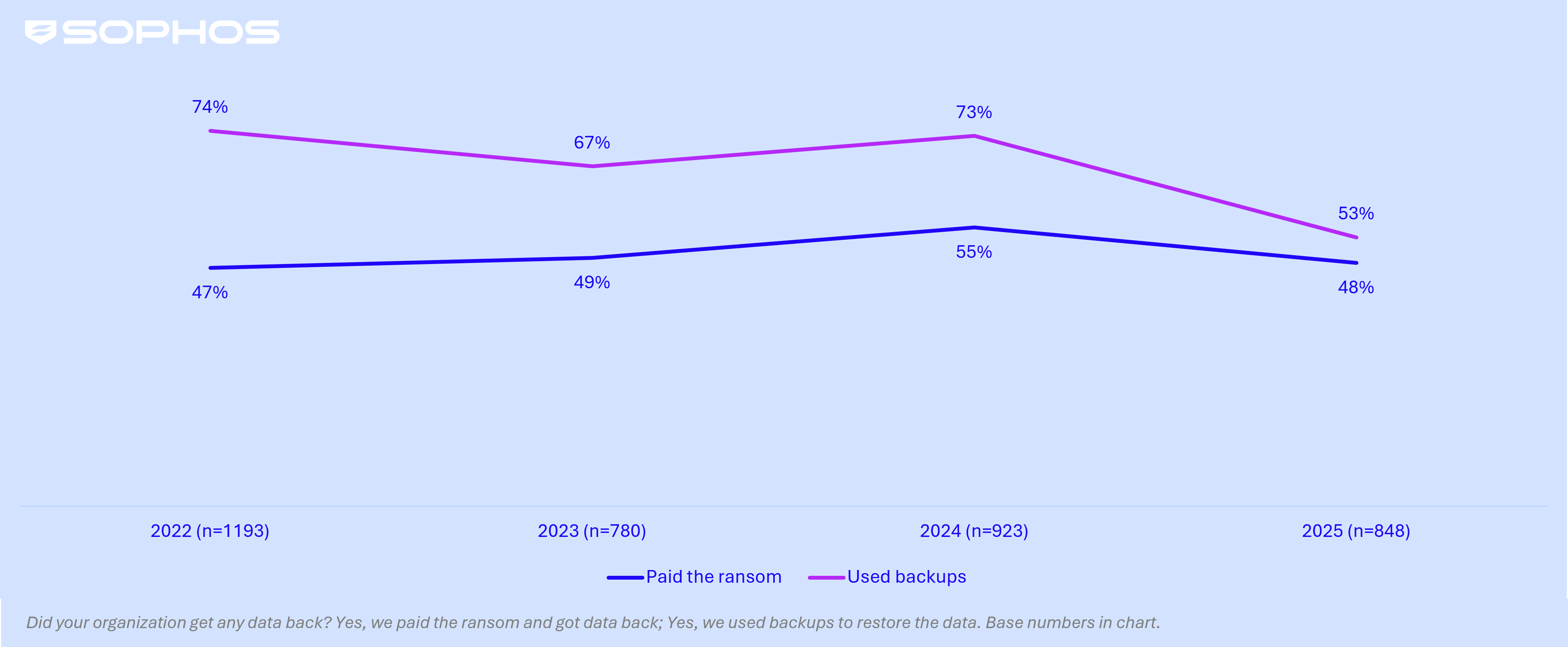
Data recovery: Ransom payment rates remain consistent while backup use plummets to a four-year low
In 2025, close to half (48%) of enterprise organizations paid the ransom to recover data, broadly in line with levels seen over the past four years, indicating little overall change in payment behavior. Meanwhile, the use of backups dropped to a four-year low of 53%, down from 73% the previous year. Collectively, these findings point to stronger resistance to demands alongside underlying weaknesses and reduced confidence in backup recovery capabilities.
Recovery of encrypted data enterprise organizations | 2021 - 2025
Ransom economics: Demands, payments, and attack recovery costs fall
In 2025, ransomware economics across enterprise organizations shifted markedly. Median ransom demands fell by 56% year-over-year, dropping to $1.20 million in 2025 from $2.75 million in 2024. Median ransom payments followed a similar downward trend, declining to $1 million compared with $1.26 million the previous year. Recovery costs also eased significantly, with the mean cost of remediation, excluding any ransom paid, falling to a three-year low of $1.84 million, down from $3.12 million in 2024, indicating a broader reduction in the financial impact of attacks.
Human impact: Attacks intensify pressure from senior leaders on IT teams
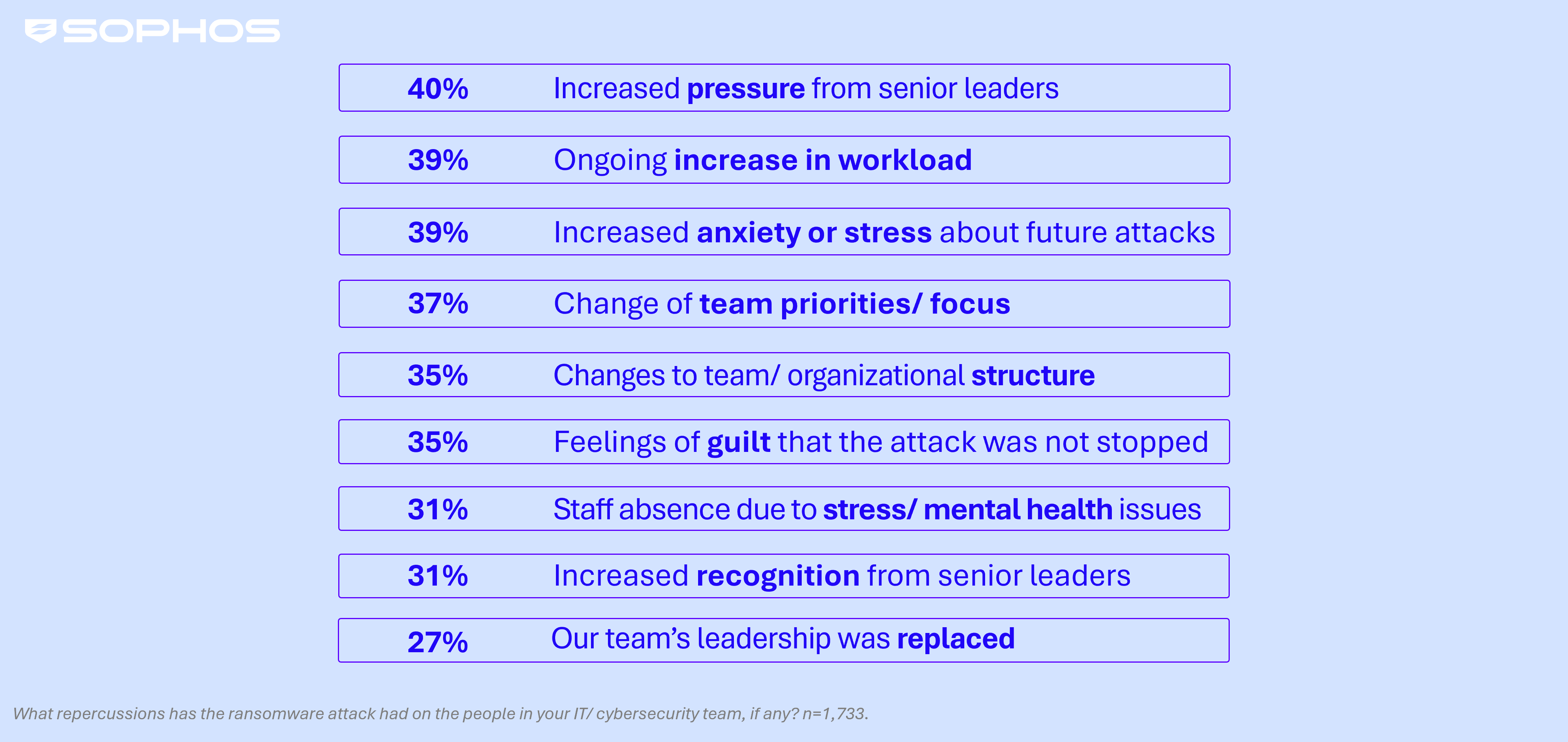
The survey makes clear that having data encrypted in a ransomware attack has significant repercussions for IT/cybersecurity teams, with increased pressure from senior leaders cited by 40% of enterprise respondents. Other repercussions include (but are not limited to):
- Ongoing increase in workload— cited by 39%.
- Change of team priorities/focus — cited by 37%.
- Feelings of guilt that the attack wasn’t stopped — cited by 35%.
Download the full report for more insights into the human and financial impacts of ransomware on enterprise organizations.
About the survey
The report is based on the findings of an independent, vendor-agnostic survey commissioned by Sophos of 3,400 IT/cybersecurity leaders across 17 countries in the Americas, EMEA, and Asia Pacific, including 1,733 from within enterprise (1,000+ employee) organizations. Overall, all participating respondents represent organizations with between 100 and 5,000 employees. The survey was conducted by research specialist Vanson Bourne between January and March 2025, and participants were asked to respond based on their experiences over the previous year.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


