Sophos Email
Protect your organization’s email infrastructure and users with the only MDR-optimized email security solution.
Sophos Email is a comprehensive email security solution that defends against phishing and BEC attacks, enhances existing email investments, and provides unmatched visibility and control to Sophos MDR and Sophos XDR.


Overview
Sophos Email provides comprehensive email security in a single, streamlined solution designed to defend against today's most sophisticated phishing and BEC attacks. Its multi-layered defense architecture incorporates over 20 AI/ML models, including natural language processing (NLP) models, to identify threats and secure inboxes.
The unique integration of Sophos Email with the Sophos MDR service and Sophos XDR platform delivers deep visibility, response capabilities, and centralized control that is unmatched by other solutions. This empowers security teams to see and actively manage email threats alongside other security vectors from a unified console.
All in one protection
Sophos Email is an all-in-one email security solution that stops threats faster and keeps email flowing to your users with high performance advanced threat detection and response. Capabilities include email filtering, protection against advanced threats, email continuity, information protection and advanced integrations.
See the Tech Specs.
Prevent phishing and imposters
Sophos Email keeps phishing imposters out, automatically identifying your high-profile targets for protection against malware-free impersonation and BEC attacks. Leveraging natural language processing (NLP) analysis of message content, sender authentication (SPF, DKIM and DMARC), URL protection, and cloud sandboxing, the solution blocks attacks before they enter a user’s inbox.
Enhance your existing investments
Organizations can easily enhance their existing Microsoft 365 and Google Workspace investments (including Outlook and Gmail) without disruption, bolstering their security posture with minimal implementation effort.
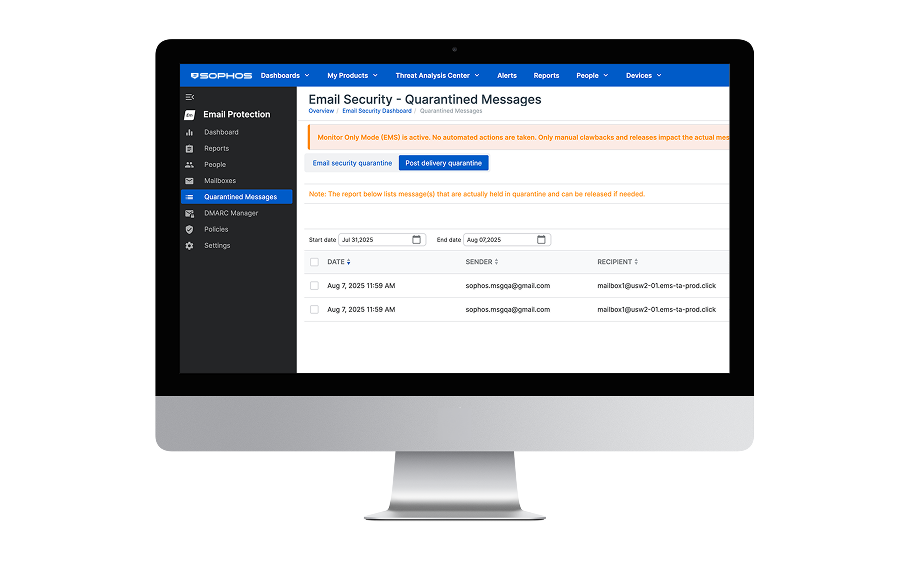
Email Monitoring System
The Sophos Email Monitoring System (EMS) is a powerful security sensor that easily complements existing email security infrastructure to detect missed threats. EMS also enables seamless integration with Sophos’ MDR service and XDR platform, incorporating critical email security data into comprehensive threat detection and response strategies.
The system leverages more than 20 advanced AI/ML models, including natural language processing (NLP) to identify and flag sophisticated threats that bypass other solutions. This additional detection layer enables organizations to identify elusive phishing attempts, BEC attacks, and other advanced threats, significantly enhancing overall email security posture without requiring replacement of existing investments.
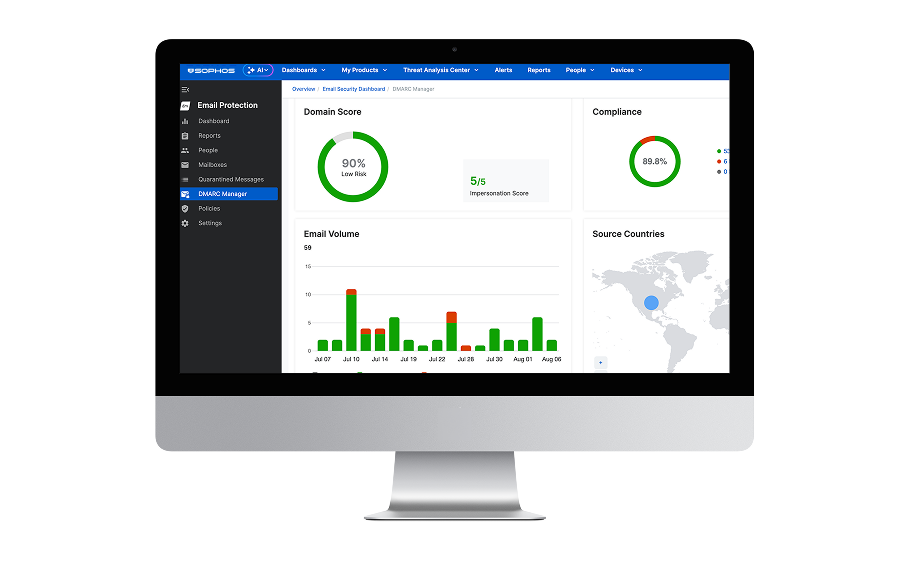
DMARC Manager
Sophos DMARC Manager helps Sophos Email and EMS customers ensure the deliverability of their messages, enhance protection against increasingly sophisticated email spoofing and domain impersonation attacks, and improve their brand’s reputation. This is all done by implementing and managing DMARC authentication protocols, creating a robust system that ensures DMARC conformance and validates sender legitimacy. Through intuitive dashboards, automated monitoring, and comprehensive reporting, the solution simplifies complex DMARC policy management, enabling organizations to achieve and maintain compliance with minimal effort.
Security awareness and training
Cybersecurity awareness training is an integral part of any defense-in-depth strategy. Sophos Email connects with Sophos Phish Threat to identify at-risk users and increase security awareness through phishing simulations, cybersecurity training modules, and actionable reporting metrics.
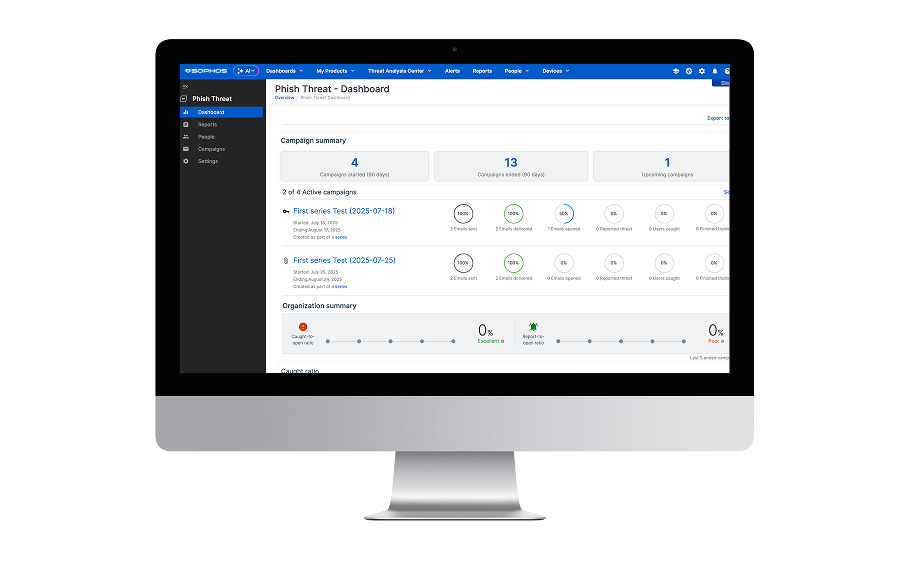

The more you see, the faster you act
Sophos Email is part of a broader Sophos ecosystem of protection, and is the only MDR-optimized email security solution.
Integrated with Sophos MDR
Free up your staff with a 24/7 managed service. With Sophos MDR, our team of expert threat hunters and analysts provides an instant security operations center (SOC), staffed with world-class security experts who monitor, prevent, detect, and respond to threats on your behalf around the clock.
Sophos Email uniquely provides Sophos’ MDR with the controls needed to execute a decisive response to an attack in real-time. Whether manually clawing back malicious messages, blocking malicious senders/domains/IPs, or modifying policies and other configurations, Sophos Email enables Sophos MDR to ensure superior cybersecurity outcomes.
Integrated with Sophos XDR
Sophos’ open, AI-native XDR platform enables you to detect, investigate, and respond to multi-stage threats across all key attack vectors in the shortest time. Sophos XDR ingests email security events from Sophos Email, including account compromise attempts, data control violations, post-delivery protection events, and more. This information is enriched with threat intelligence from Sophos X-Ops and grouped with related detections across Sophos and third-party solutions to highlight an attack.
Your security analysts can use Sophos XDR to take email-related actions such as manually clawing back malicious emails, blocking senders/domains/IPs, tweaking policies, and modifying other configurations as required.
Integrated with Sophos Endpoint
Sophos Email and Sophos Endpoint work together to stop threats that originate from compromised devices. If a device starts sending spam or phishing emails, Sophos Email detects the behavior and blocks malicious messages before they reach users—protecting your brand and inboxes.
This integration enables real-time sharing of threat data between platforms, allowing security teams to isolate affected devices, quarantine suspicious emails, and adjust policies quickly. With coordinated detection and response, organizations gain stronger protection across two critical attack surfaces—all managed through a unified
security ecosystem.
Simplify cybersecurity management
Email remains one of the primary malware delivery methods and retains a prominent role in multi-stage attacks. Visibility into email-related security threats and the ability to act upon them with speed is essential.
Sophos Central is a powerful, cloud-based cybersecurity management platform that unifies all Sophos next-gen security solutions. It offers centralized control, advanced threat protection, and seamless scalability, enabling organizations to efficiently manage and secure their IT infrastructure with industry-leading AI and real-time data insights, all through a single intuitive interface.
Get peace of mind from data security
Secure sensitive data and make compliance easy. Sophos Email automatically scans messages and attachments for sensitive data, with encryption that integrates seamlessly.
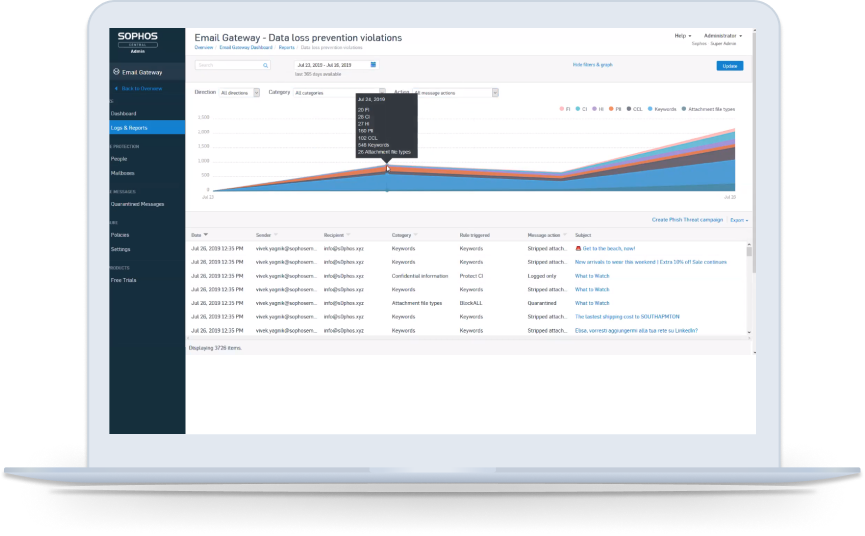
Prevent data loss
Create multi-rule DLP policies for groups and individual users to ensure protection of sensitive information with discovery of financials, confidential contents, health information, and PII in all emails and attachments.
Encrypt and authentication
Encrypt messages and add a digital signature to verify sender identity with S/MIME, or select from customizable encryption options including TLS encryption, attachment and message encryption (PDF and Office), or add-on full web portal encryption.
Join a security partner trusted by thousands
Sophos is proud to support over 26,000 organizations with advanced email threat protection and data security. Compatible with all email services, including Google Workspace's Gmail, where you control the domain and DNS records, or through direct API integration with Microsoft 365 for even faster protection.
RELATED PRODUCTS AND SERVICES
Cybersecurity for all your needs
Sophos Managed Detection and Response (MDR)
Free up IT and security staff to focus on business enablement and leverage superior security outcomes delivered as a service.
- Instant security operations center (SOC).
- 24/7 threat detection and response.
- Expert-led threat hunting.
- Full-scale incident response capabilities.
- Keep the cybersecurity software you already have.
- On-demand, weekly and monthly cybersecurity health reports.
- The most robust MDR service for Microsoft environments.
- Breach protection warranty.
Sophos Extended Detection and Response (XDR)
Included with Sophos MDR and available separately: Empower your security team to defend against active adversaries with extended detection and response (XDR) tools.
- Gain insights into evasive threats.
- Optimize your investigations with streamlined workflows.
- AI-powered tools accelerate security operations.
- Accelerate and automate response.
- Leverage a fully integrated portfolio of Sophos products.
- Integrate with your existing cybersecurity tools.
- Includes endpoint protection and EDR features as standard.
