
Sophos Cloud Security Posture Management
Easily identify cloud resource vulnerabilities, ensure compliance, and respond to threats faster.
.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
Security and Cost Optimization Features







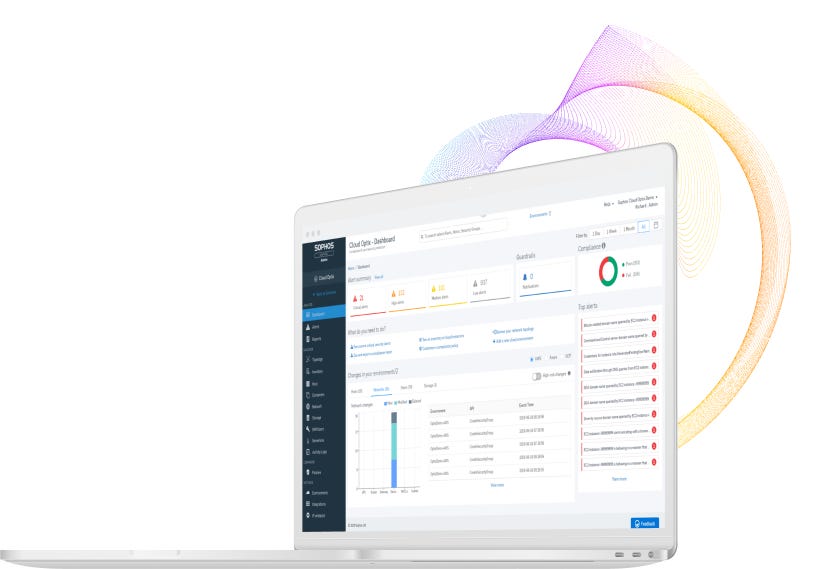
Instant Access Demo
View a fully-populated Cloud Optix demo. All features and alerts – no setup, no commitment.
Multi-Cloud Visibility
Respond to Cloud Security Threats Faster
Focus on and fix your most critical security vulnerabilities before they are identified and exploited in cyberattacks. By identifying and risk-profiling security, compliance, and cloud spend risks, Cloud Optix ensures teams respond faster, providing contextual alerts that group affected resources with detailed remediation steps.
Manage Identities Before They’re Exploited
Security at The Pace of DevOps
- Container Image Scanning Scan container images pre-deployment to prevent threats from operating system vulnerabilities and identify available fixes.
- Infrastructure-as-Code Scanning Automatically detect misconfigurations, embedded secrets, passwords, and keys in Infrastructure-as-Code templates.
Optimize Costs and Improve Security
- Track cloud costs for multiple services side by side on a single screen to improve visibility and reduce wasted spend.
- Identify unusual activity indicative of abuse, highlighting top services contributing to spend with customizable alerts.
- Receive independent recommendations to optimize AWS spend, integrate with AWS Trusted Advisor, and Azure Advisor.
Extend Your Data Sources With XDR
Sophos Intercept X with XDR is enhanced with Cloud Optix data to place security teams closer to the occurrence of a security event, with cross-platform detection capabilities that can provide deeper insight and context to issues.
- Sophos Extended Detection and Response (XDR) goes beyond the endpoint, pulling in rich network, SaaS email, cloud workload, AWS, Google Cloud Platform and Microsoft Azure cloud environment data sources.
- Investigate AWS cloud environment API, CLI, and management console activities with seamless integration to AWS CloudTrail.
- Use queries associated with attacker tactics to detect initial access, persistence, and privilege escalation.
How Shutterfly reduced alert noise to focus teams on delivering value to the business.."
Aaron Peck
Vice President and CISO, Shutterfly Inc.

The World's Most Trusted Cloud Security Platform
Discover Sophos Central, a single intuitive security management platform to enable your digital transformation, trusted by over 150,000 customers world-wide and secured by Cloud Optix.
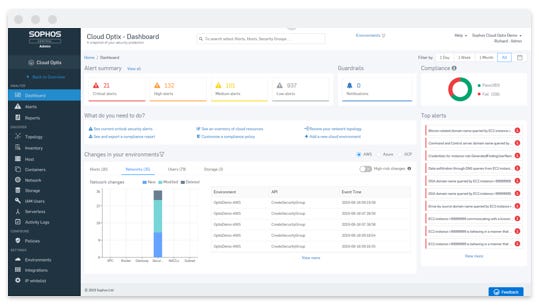
Cloud Optix continually monitors cloud configurations, detecting suspicious activity, insecure deployment, and over-privileged IAM roles, while helping optimize cloud costs.

Cloud Security Posture
Management ROI Calculator
See how much your teams could save in time and energy costs by managing security, compliance, and spend optimization across AWS, Azure, Google Cloud, and Kubernetes.
Number of cloud assets
Number of regulatory and industry compliance standards to meet
The results presented here are an estimate, not a guarantee, and actual savings may vary.
See Your Savings
Reduced labor to identify, assess, and remediate security risks
Reduced labor to comply with regulatory and industry standard audits
Total three-year saving
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)

