Cloud Workload Protection
Protect infrastructure and data now and as it evolves.

Optimize Workload Protection
Secure Cloud Growth
Protect your infrastructure with runtime threat detection and prioritized investigations across your cloud environments, data centers, hosts, and containers.
Reduce Your Attack Surface
Detect workload security and compliance configuration risk, anomalous activity, and overprivileged IAM access with visibility from development to production.
Get Performance and Uptime
Flexible, lightweight host and container protection is optimized for performance. Available via agent or API to integrate with your security operations, IT, and DevOps processes.

Minimize Time to Detect and Respond
Sophos Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
- Extended detection and response (XDR) provides complete visibility across your hosts, containers, endpoints, networks, and cloud services.
- Cloud-native behavioral and exploit runtime detections identify threats, including container escapes, kernel exploits and privilege-escalation attempts.
- Streamlined threat investigation workflows prioritize high-risk incident detections and consolidate connected events to increase efficiency.
- Integrated Live Response establishes a secure command line terminal to hosts for remediation.
Integrate with Security, IT, and DevOps
Combat threats with actionable host and container runtime visibility and threat detections delivered through the deployment model that works best for your environment.

Lightweight Linux and Windows Host Agent
Secure your hosts and containers with a single agent managed through the Sophos Central management console. Easily investigate and respond to behavioral, exploit, and malware threats in one place and increase IT hygiene with automated detections, intuitive queries, and remote response.
Integrated Linux Threat Intelligence
Fine-tuned for maximum performance, seamlessly enrich your security operations workflows. Includes an ultra-lightweight Linux sensor that can be integrated into host and behavioral and exploit runtime detections via API and complements your existing automation, orchestration, log management, and incident response tools.
Get Performance Without Friction
Uptime is your top priority. We provide lightweight security tools that can be integrated into your DevSecOps workflows to minimize risk and improve application performance.
Optimized for Linux
Identify sophisticated Linux security incidents as they happen without deploying a kernel module.
Eliminate Disruptions
Use a single agent optimized for resource limits (including CPU, memory, and data collection limits) to avoid costly downtime, overloaded hosts, and stability issues caused by traditional security tools.
Integrate with CI/CD Pipelines
Seamlessly integrate security configuration and compliance checks at any stage of the CI/CD pipeline, scan container images for operating system vulnerabilities, and automatically detect misconfigurations, embedded secrets, passwords, and key in Infrastructure as Code (IaC) templates.
Automate Your Cloud Security Checklist
Design your cloud environment in alignment with cloud security best practices and get the visibility and tools required to maintain them, with cloud security posture management across your multi-cloud environments.
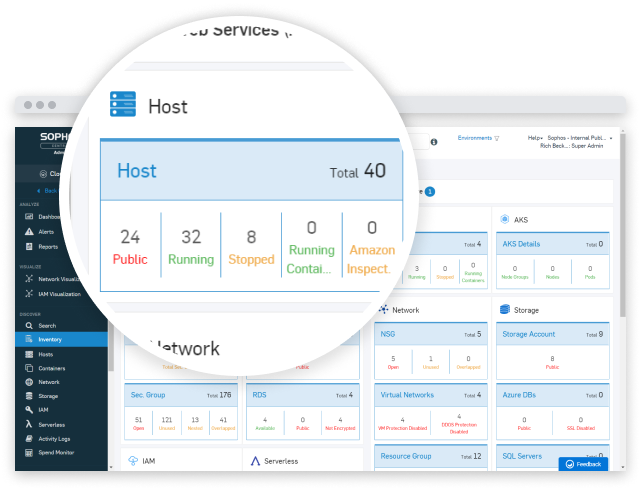
- Proactively identify unsanctioned activity, vulnerabilities, and misconfigurations across AWS, Azure, and GCP.
- Continuously discover cloud resources with detailed inventory and visualization of networks, Sophos host protection and Sophos Firewall deployments.
- Automatically overlay security best practices and compliance standards to detect gaps in your security posture and identify quick wins and critical security issues.
- Detect over-privileged access and high-risk anomalies in user behavior to prevent breaches.
Get Flexible Host and Container Protection
Protect your host and container workloads across Linux, Windows, hybrid, and multi-cloud environments.

Linux Security
Detection and resilience for Linux systems across container runtimes such as Docker, containerd, CRI-O, and other environments. Our detection is crafted with the threat models of cloud-native systems top of mind.

Windows Security
Secure your Windows hosts and remote workers against ransomware, exploits, and never-before-seen threats, manage applications, lock down configurations, and monitor changes to critical system files.

Hybrid and Multi-Cloud
Safeguard applications and data across your hybrid cloud environments from a single console. Our flexible agent runs on premises, in data centers, and across AWS, Azure, GCP, Oracle Cloud, and other hybrid and multi-cloud environments.
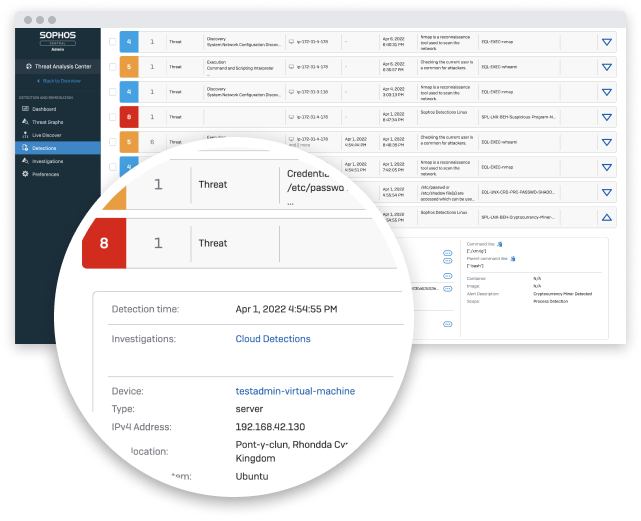
Resolve Security Incidents Faster
Our intuitive detection dashboard increases incident response efficiency. Host and container threats are automatically identified and investigated, and an AI-prioritized risk score is provided for each detection. Scores are then color-coded and mapped against the MITRE ATT@CK framework, enabling security analysts to quickly prioritize, respond to, and remediate high-risk detections.
Detections include: Malware Targeting Linux, Memory Corruption, New File Behavior, Unusual Application Behavior, Suspicious Interactive Shell, Container Escapes, Kernel and Userland Backdoors, Privileged File Operations, Network Discovery, Lateral Movement, Process Injection, System Discovery, Scheduled Task Changes, Compiler Usage, Privileged Command Usage and Risky Developer Activity.

Hunt for Threats and Strengthen Your IT Operations
Get information that matters to you — right away. Choose from a library of pre-written templates for threat hunting and IT operations scenarios, customize them, or write your own. Access live data from up to 90 days on disk and 30 days of data stored in the Sophos Data Lake to ensure you're covered for every scenario.
Popular customer use cases:
- Why is a workload running slowly? Is it pending a reboot?
- Which workloads have known vulnerabilities or unknown services?
- Are there programs running on the machine that should be removed?
- See unmanaged and unprotected devices such as laptops, mobiles, and IoT devices.
- Are processes trying to make a network connection on non-standard ports?
- Have any processes had files or registry keys modified recently?
- Which programs are causing office network issues?
- Analyze cloud security groups to identify resources exposed to the public internet.
Take the Weight of Cloud Security Off Your Shoulders
Our flexible approach to cybersecurity deployment and management means optimizing security, keeping data secure and private, while blocking active threats are goals you can easily achieve.
- Deploy and manage Sophos protection from a single unified console.
- Sophos can connect you with an experienced Sophos Managed Security Partner.
- Sophos' Professional Services Team can help with initial deployment.

Respond to Security Incidents at 3 a.m.
The Sophos Managed Detection and Response (MDR) service can work with your team and Sophos MSP to monitor your environment 24/7/365 and proactively hunt for and remediate threats.
- Threat Hunting: The elite team of threat analysts will proactively hunt for threats and help you determine their potential impact and context to your business.
- Response: Remotely disrupts, contains, and neutralizes even the most sophisticated threats.
- Continuous Improvement: Get actionable advice for addressing the root cause of recurring incidents to stop them from occurring again.
Delivering Complete Multi-Cloud Security Coverage Across Environments, Workloads, and Identities
Sophos Cloud Native Security is a single integrated platform that unifies visibility, governance, and compliance tools with cloud workload protection and entitlements management.
Visibility, Governance, and Compliance
Maintain visibility across your multi-cloud environments to reduce your attack surface, detect and remediate security risks, and maintain compliance.
Cloud Workload Protection
Flexible host and container workload security for Windows and Linux protects your infrastructure and data.
Entitlements Management
Implement least privilege across your multi-cloud environments and manage your identities before they're exploited.