Sophos Exploit Prevention
Sophos Endpoint prevents the exploits hackers rely on
While there have been countless types of cyberattacks and more are created every minute, hackers rely on key security software vulnerabilities to spread malware, ransomware, and more.
The abuse of a software vulnerability by an attacker is called an exploit. While there are millions of pieces of malware in existence, and thousands of software vulnerabilities waiting to be exploited, there are only handful of exploit techniques attackers rely on as part of the attack chain – and by taking away the key tools hackers love to use, Sophos Endpoint stops exploits and zero-day attacks before they can get started.
Block zero-day attacks by blocking exploits
Attackers want to distribute and install their malware, steal your data, and evade detection. Using a relatively short list of highly effective exploit techniques enables them to do just this.
With Sophos Endpoint, evasive hackers and zero-day attacks can’t get through – because rather than focusing solely on stopping malware, Sophos Endpoint tracks the behavior that indicates an attack is underway and stops it dead in its tracks.
Vulnerabilities occur in software at an alarming rate, often requiring patches from the vendor – and before those patches, those vulnerabilities remain. While installing the latest patches as quickly as possible is always a recommended best practice, Sophos Endpoint offers a layer of protection against unpatched devices. By intercepting the techniques attackers use to take advantage of these and other vulnerabilities, Sophos is able to stop attackers from abusing a computer to do something it should not be doing.
Sophos Endpoint includes:
Ransomware Protection
CryptoGuard uses behavioral analysis to stop previously unseen ransomware and boot record attacks. Never pay a ransom again.
Active Adversary Mitigations
Sophos Endpoint utilizes a range of techniques, including credential theft prevention, code cave utilization detection, and APC protection used to gain a presence and remain undetected on victim networks.
Deep Learning
Sophos Endpoint uses a deep learning neural network, an advanced form of machine learning, to detect known and unknown malware without signatures.
Vulnerabilities vs. Exploits vs. Exploit Techniques
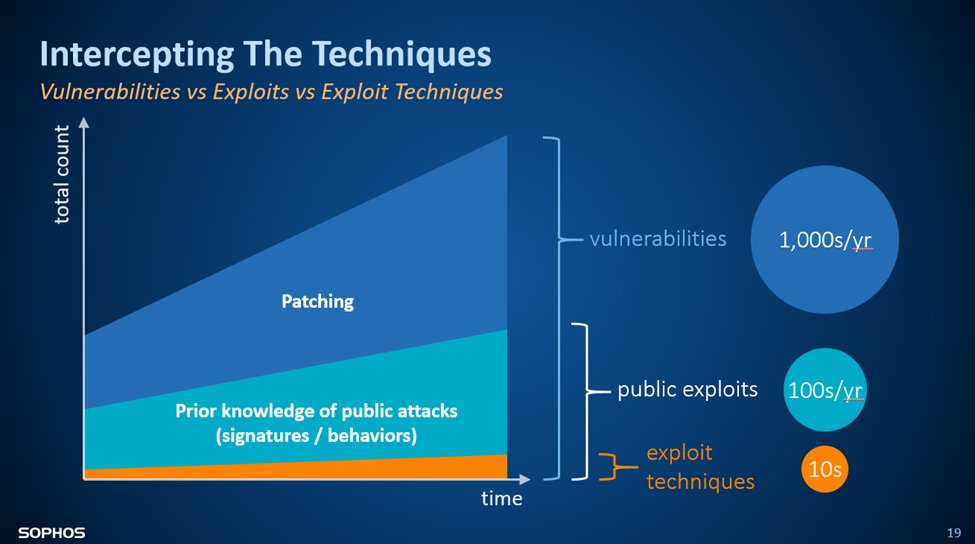
Vulnerability
A weakness in the design or implementation of a piece of hardware/software.
Exploit
A specific successful and reliable use of one or more exploit techniques against one of thousands of potential target vulnerabilities.
Exploit Technique
The underlying way in which an attacker can abuse a vulnerability to make a computer do something it shouldn’t
Prevent Exploits in Your Organization with Sophos Endpoint
Sophos Endpoint Advanced | Sophos Endpoint Advanced with XDR | Sophos MDR Standard | Sophos MDR Advanced | |
| Foundational techniques | ||||
| Deep learning | ||||
| Anti-exploit | ||||
| CryptoGuard anti-ransomware | ||||
| Extended detection and response (XDR) | ||||
| 24/7 Monitoring and Response | ||||
| Lead-driven threat hunting | ||||
| Advanced lead-less threat hunting |