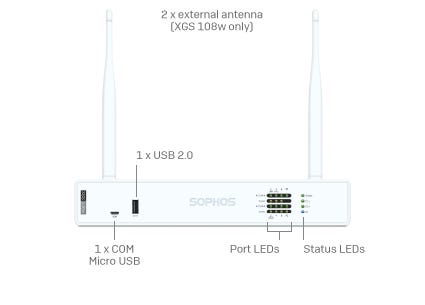
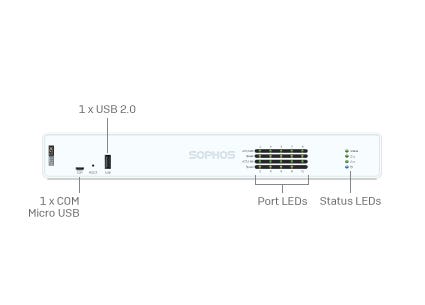
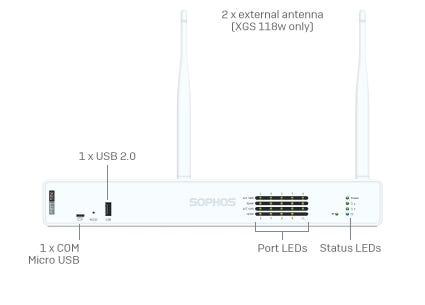
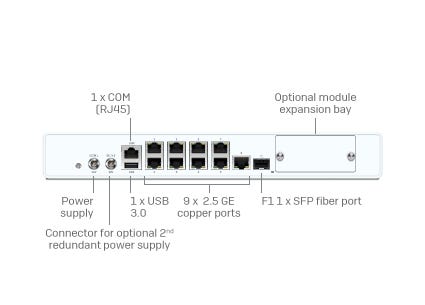
Modernste Cybersicherheit
Die perfekte Kombination aus erstklassiger Technologie und menschlicher Expertise – optimal abgestimmt auf Ihre Bedürfnisse. So gewinnen Sie auf ganzer Linie.
Starker Schutz und eine adaptive, KI-native Plattform zur frühzeitigen Abwehr von Angriffen
DR-Experten, die Bedrohungen schnell und zuverlässig finden und beseitigen
Einzigartige Abwehrmaßnahmen für die gesamte Angriffsfläche – Endpoint, Firewall, E-Mail und Cloud

Adaptive, KI-native Cybersecurity-Plattform
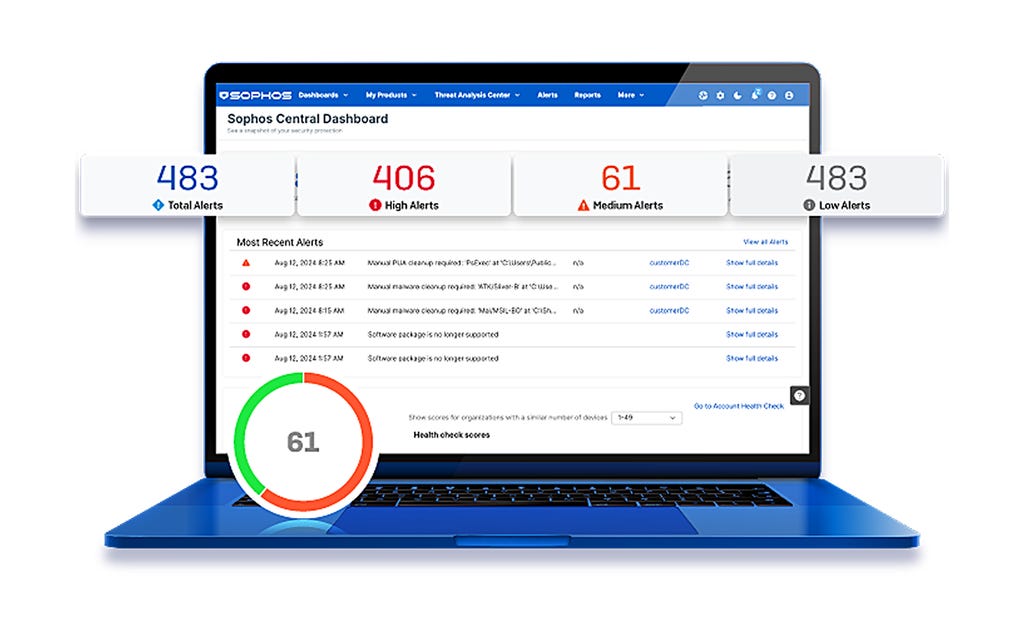
Sophos Central bietet Kunden erstklassigen Schutz und sorgt für mehr Effizienz bei der Abwehr. Dynamische Abwehrmaßnahmen, modernste KI und ein offenes Ökosystem mit vielen Integrationen – all das bietet die branchenweit führende KI-Cybersecurity-Plattform.

Adaptive AI-native cybersecurity platform
Sophos Central delivers unrivalled protection for customers and enhances the power of defenders. Dynamic defenses, battle-proven AI, and an open, integration rich ecosystem come together in the largest AI-native platform in the industry.

Open ecosystem
Works with Sophos products, other vendors’ products, or any combination of the two.
.webp?width=980&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
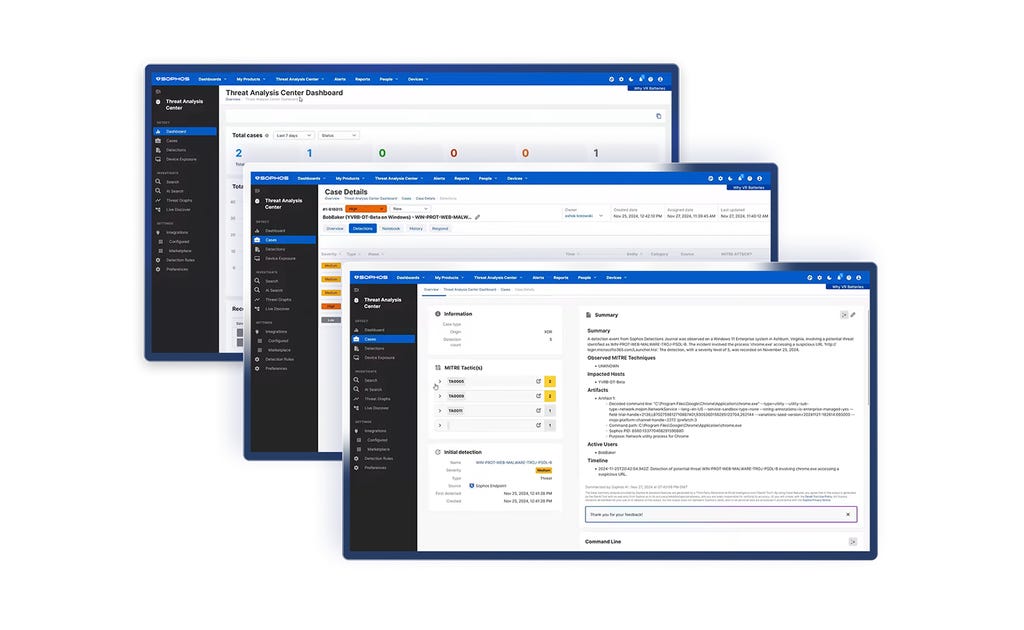
Sophos X-Ops
Bietet kollektives Expertenwissen über die gesamte Angriffsumgebung zur effektiven Abwehr hochkomplexer Angreifer.
Wie Unternehmen mit
Sophos sicher bleiben
Customer success
Already a customer?
Find additional information to inspire, grow your knowledge, troubleshoot, and get help.

Robust generative AI development process
The benefits of GenAI for cybersecurity are matched by their potential danger. Sophos deploys rigorous processes for all GenAI tools, from concept to full deployment. Detailed performance analysis and user feedback at each stage informs the next step in the development process.

Frequently asked questions
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
- Sophos Central offers
centralized security
management, real-time threat protection
- It integrates seamlessly
automated responses, multi-factor aut
comprehensive and scalable solution for man
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs. Sophos Central offers centralized security section, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.
Sophos Central offers centralized security management, real-time threat protection, automated responses, multi-factor authentication, secure data encryption, and custom dashboards. It integrates seamlessly with all Sophos products, providing a comprehensive and scalable solution for managing your cybersecurity needs.

The Cybersecurity Playbook for Partners in Asia Pacific and Japan
Sophos and Tech Research Asia (TRA) present the latest Cybersecurity Playbook for Partners in Asia Pacific and Japan.
Based on research with 900 companies, the playbook explores trends in cybersecurity investment, challenges, and areas of growth for MSPs, building on insights from our previous report.
Key Insights:
- Alignment of business goals with cybersecurity investments
- Budget visibility and top growth areas for partners
- Demand for AI-augmented cybersecurity solutions
- Country-specific data snapshots for tailored partner strategies
Unlock Growth Potential
With 83% of companies increasing cybersecurity budgets and more than 50% expanding MSP use, the opportunity for growth is immense. Use this playbook to enhance client engagement, offer strategic support, and strengthen their cybersecurity resilience.
Download the full report to discover how you can drive growth in the APJ region.
EYEBROW
The Cybersecurity Playbook for Partners in Asia Pacific and Japan
Sophos and Tech Research Asia (TRA) present the latest Cybersecurity Playbook for Partners in Asia Pacific and Japan.
Based on research with 900 companies, the playbook explores trends in cybersecurity investment, challenges, and areas of growth for MSPs, building on insights from our previous report.
- Alignment of business goals with cybersecurity investments
- Budget visibility and top growth areas for partners
- Demand for AI-augmented cybersecurity solutions
- Country-specific data snapshots for tailored partner strategies
Based on research with 900 companies, the playbook explores trends in cybersecurity investment, challenges, and areas of growth for MSPs, building on insights from our previous report.
Our people make Sophos special.
Join our team today. Check out our current openings.
Sed et Lorem consectetur sit
Aliqua. ipsum et incididunt consectetur . amet Lorem aliqua. Lorem dolore incididunt adipiscing amet . tempor dolore tempor adipiscing tempor amet ut . amet consectetur magna elit amet do tempor consectetur . elit consectetur labore elit ut .

SD WAN Savings Calculator
See how much you can save by switching from MPLS to Sophos SD-WAN
Reduce reliance on expensive MPLS links by switching to SD-WAN. Maintain or increase application performance and availability.
The results provided by this tool are an estimate based on the information you provide. Your actual savings may vary.
See Your Savings
Current Monthly Cost
Projected Monthly Costs
Monthly Cost Reduction
Three-year Savings
Sophos can help you decrease costs by offloading some or all of your MPLS connections to less expensive local internet services like 3G/4G, DSL, and cable. We'll work with you to build a secure, highly available, and higher performance WAN at a significant savings.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)

.png?width=1024&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)









.png&w=1920&q=75)

.png&w=1920&q=75)

.png&w=1920&q=75)