Counter Threat Unit™ (CTU) researchers are frequently asked about ransomware groups posing a threat to organizations in specific verticals or geographic locations. These questions usually follow the publication of third-party reports that highlight how a particular ransomware group is “targeting” a specific sector. CTU™ researchers understand the concerns but maintain that focusing on defending against specific groups is not the best way to avoid becoming a victim of ransomware. As the majority of ransomware attacks are opportunistic, organizations should instead consider how they can best prepare for any ransomware or data theft attack, regardless of the perpetrators.
How threat actors choose their victims and deploy ransomware depends on their motivations. Cybercriminals want to make money, so all organizations are potential victims of these groups. In contrast, state-sponsored actors use ransomware for destructive purposes, to obscure espionage activity, to generate revenue, or to achieve a combination of these outcomes. Each of these groups therefore has a separate threat profile, and the organizations at risk can vary greatly.
Cybercrime
Financially motivated attacks are by far the most prevalent ransomware operations. As threat actors victimize any organization that they can access, organizations in all verticals and locations are at risk.
Although some groups might choose to exploit available access at higher-revenue companies in the belief it will secure a larger payout, Sophos customer telemetry reveals that most attempts to deploy ransomware occur at small organizations. These companies are likely more susceptible to compromise due to limited cybersecurity budgets and lack of dedicated in-house cybersecurity resources.
Opportunistic access for financial gain
Financially motivated ransomware operations are almost entirely opportunistic and based on available access. This access may have been obtained via malware delivered in phishing campaigns, credentials captured by infostealers, or the exploitation of vulnerabilities in internet-facing services. Whatever the method, the approach is random and untargeted. CTU researchers therefore try to avoid using the word “targeting” when talking about attacks, instead using “victimization” to describe the victim selection process.
Any triage likely involves an assessment of which potential victims not to attack rather than which ones to attack. For example, most Russian and Eastern European ransomware groups deliberately avoid compromising organizations in Russia or other Commonwealth of Independent States (CIS) member nations, and increasingly members of the BRICS economic bloc, to avoid Russian or Russia-aligned law enforcement scrutiny. Some groups may also endeavor to avoid attacking organizations in the healthcare or critical infrastructure sectors, likely to avoid international pressure on local law enforcement to take action, although groups often make such claims on grandiose and spurious ethical or moral grounds.
The banking sector is a good example of the opportunistic nature of cybercriminal ransomware attacks. Banks are high-revenue organizations, and a disruption to their operations caused by ransomware would be a powerful motivation for them to pay ransoms. Theoretically, these factors would make them prime targets for such attacks. However, CTU researchers see very few banks targeted by ransomware. This is likely because it is a heavily regulated sector with mandatory cybersecurity standards that eliminate competitive penalties. As a result, investments are made, control frameworks are specified, perimeters are well-defended, and networks are designed to limit opportunities for compromise. Organizations operating in unregulated sectors are more susceptible to opportunistic attacks because employing robust cybersecurity practices is not incentivized in the same way. For example, enhancing security measures in the manufacturing sector increases a company’s cost base and makes a competitor’s products comparatively cheaper.
When organizations in a particular sector are victimized by a specific group, it is likely a result of that group exploiting a vulnerability in a service that is widely adopted across that sector. Organizations in the same sector tend to have similar security frameworks. There are exceptions, however. Some groups may victimize organizations in sectors that they think would be more likely to pay a ransom. For example, Conti affiliates deliberately attacked hospitals during the COVID-19 pandemic in the belief that it would increase the chance of a payout. GOLD VICTOR, which launched the Vice Society and Rhysida ransomware operations, has a clear predilection for victimizing healthcare and education organizations, likely for the same reason (see Figure 1). However, in the six months prior to December 31, 2025, Rhysida accounted for less than 1% of the total number of victims listed on all leak sites. Ransomware victimization continues to remain overwhelmingly randomized.
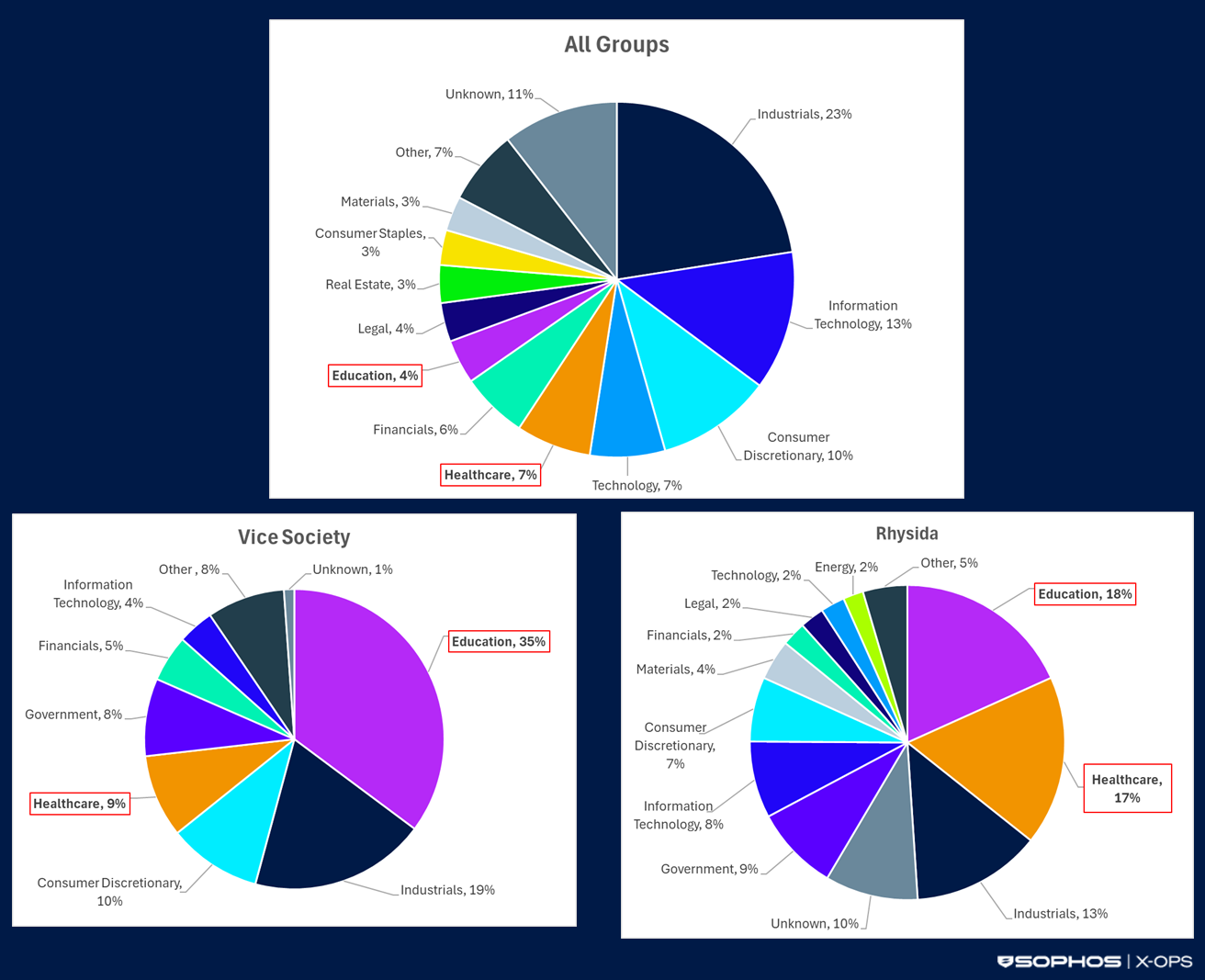
Figure 1: Sectors victimized across all ransomware groups from May 1, 2021 through December 31, 2025, compared to the breakdown for Vice Society and Rhysida
Victim triage likely varies greatly among groups, based on maturity, expertise, and appetite for risk. The affiliate model in ransomware-as-a-service (RaaS) schemes has certainly made this process much less predictable. While affiliates of a particular scheme might share a playbook, they also move between schemes to secure the best deal, making attribution and anticipating intrusion activity challenging.
When advertising for affiliates, some groups stipulate conditions such as prohibitions on attacking certain sectors and geographies, and requirements that victims’ revenue must be over a certain amount to ensure that time spent on the attack results in a profitable payout. However, it is almost certainly the case that some inexperienced affiliates do not engage in a triage process at all and are likely not fully aware of whom they have victimized until after they have stolen data and deployed ransomware. If an attacker does not properly assess the potential impact, then ransomware deployment can be devastating by accident. For example, it is highly unlikely that the Qilin affiliate that deployed ransomware at Synnovis in June 2024 knew it would result in such significant damage to National Health Service (NHS) operations in London.
Supply chain compromise
Some threat actors focus on compromising the supply chain, which can make ransomware or data theft operations appear targeted when they are not. For example, the GOLD TAHOE threat group that operates Clop ransomware deliberately creates exploits for zero-day vulnerabilities in managed file transfer (MFT) services to steal data and hold it for ransom. The group is not deliberately targeting and extorting any particular organization; the victims just happen to use the exploited service and get caught up in the attack. Given that the exploitation and data theft occur at scale and through automation, any triage that occurs takes place after the group has collected the data and identified victims. It is possible that GOLD TAHOE prioritizes extortion against certain companies, possibly based on revenue or sector, but the ransom demands appear generic and unfocused. Nevertheless, this technically adept activity is atypical for a cybercriminal group.
Acclaim
Another motivation in cybercriminal ransomware operations that can change the dynamic of victim selection is kudos from peers. For example, it is not clear how Scattered Spider, a disparate collective of young individuals that CTU researchers track as GOLD HARVEST, chooses which organizations to victimize. However, the group members’ core motivation for their attacks is not necessarily financial gain. Like previous groups such as GOLD RAINFOREST (also known as Lapsus$) and Lulzsec, attacks appear to be undertaken for bragging rights and praise rather than moneymaking, so they regularly impact high-profile organizations. GOLD HARVEST has demonstrated significant aptitude in their operations. In compromising credentials for the Okta identity service solution, for example, the threat actors were able to subsequently target companies that relied on Okta for authentication.
Some of the group’s tradecraft involves target selection that does not rely on opportunistic access like other cybercriminal or ransomware groups. Members of the collective, who are predominantly native English-speakers, attempt to gain access to chosen organizations via social engineering: calling help desk staff to reset passwords or enroll multi-factor authentication (MFA) devices. They might not always succeed, but it nevertheless represents a different threat from conventional cybercriminal or ransomware groups.
That said, it is possible that the group does also use available access opportunities to exploit victims. Although CTU researchers have no special insight into the attacks, it has been rumored that third-party IT supplier Tata Consulting Services (TCS) had a role in both the Marks & Spencer (M&S) and Co-op attacks in 2025. TCS has denied its systems or users were compromised.
Brand building
RaaS operators might be motivated to build their brand to attract affiliates. The operators might encourage affiliates to target any organization, regardless of the likelihood of a payout, to boost victim numbers and make the scheme appear more impactful. This approach creates a dilemma for RaaS operators – how can they have enough impact to make a scheme attractive to affiliates but not cause so much damage that it brings unwanted attention from law enforcement? Most groups simply want to make money, so targeting organizations that represent a risk to their operations is ill-advised. Their triage process therefore likely involves avoiding victimizing high-profile organizations (e.g., hospitals, charities). In addition, the number of low-skilled threat actors engaging in ransomware attacks means that the landscape is dominated by high-volume, low-“quality” intrusions that have a lower impact on compromised organizations. The lower impact might explain why the rate of organizations paying ransoms continues to drop.
State-sponsored ransomware
State-sponsored ransomware operations are generally not opportunistic but deliberately target specific organizations. The targeting is highly influenced by motivation and the threat actors’ operational objectives. State-sponsored operations form a very small proportion of the overall volume of ransomware attacks.
CTU researchers have observed three primary motivations in state-sponsored or government-aligned ransomware attacks.
Revenue generation
State-sponsored groups focused on generating revenue are likely to be less targeted in their ransomware deployments than groups that are motivated by other goals. Multiple North Korean threat groups have experimented with ransomware attacks for revenue generation, ranging from targeted use of ransomware like Maui to the indiscriminate WCry (also known as WannaCry) ransomware worm. Known victims are often in the healthcare sector, which could indicate a deliberate choice from a government that is unconcerned with the potential risk to life or law enforcement consequences and has determined that healthcare organizations may be most likely to pay a ransom.
Similarly, ransomware attacks by the Iranian COBALT MIRAGE threat group demonstrated the unusual combination of links to state-sponsored operations with targeting that had no apparent strategic alignment with government interests. Subsequent investigation identified private sector entities in Iran that were engaged in operations for the Iranian Revolutionary Guard Corp (IRGC) but also used similar tradecraft to conduct ransomware attacks for their own gain.
Smokescreens to obscure other activity
Certain state-sponsored actors, such as the China-based BRONZE STARLIGHT threat group, deploy ransomware as a cover for espionage. Encrypting systems obscures forensic traces of the full intrusion, while the ransomware narrative diverts investigators’ attention away from the attackers’ true objectives and the actual impact. Therefore, in smokescreen activities, ransomware deployment is targeted at specific organizations and undertaken like any state-sponsored activity (i.e., focused and determined).
Disruption, harassment, and influence
Ransomware is a powerful disruptive tool, so it is useful for threat actors wishing to damage operations at organizations in countries deemed hostile. This can make attribution and establishing motivation challenging. For example, CTU researchers initially attributed a DarkBit ransomware deployment at a Middle Eastern organization to a financially motivated group (GOLD AZTEC) but subsequently realigned the group’s motives as further evidence came to light of its targeting history and tradecraft. Analysis indicated that it was actually an Iranian state-sponsored group engaged in destructive attacks, so CTU researchers renamed it COBALT AZTEC. Other Iranian threat groups such as COBALT SAPLING, COBALT MYSTIQUE, and COBALT SHADOW hide behind fake hacktivist personas to target specific organizations in Israel and Albania with disruptive ransomware and data theft attacks.
Similarly, Russia unleashed multiple waves of ransomware attacks against the Ukrainian financial sector prior to 2022, the highest profile being NotPetya. While some impacted organizations attempted to recover their systems by paying a ransom, the threat actors behind these attacks did not provide decryption tools as they were not engaging for financial gain or seeking to build a reputation for their brand.
Although the primary motivation in these attacks is not financial, it is both plausible and likely that some state-sponsored groups engage in ransom negotiations with victims to extort payment. However, evidence suggests it would be a profitable side business rather than a motivating factor in deciding whom to target. Iranian groups in particular have leaked details of negotiations to amplify the visibility of the attack, cause additional political damage to the victim, and undermine the government of Israel. Such activity obviously adds an additional layer of complexity to attribution.
Conclusion
Most ransomware attacks are opportunistic and conducted by cybercriminals to make money. The threat actors exploit the access they have rather than try to gain access to priority targets. Any victim triage, if it occurs at all, happens after access has been obtained. As such, organizations are victimized rather than targeted. While some ransomware groups and their affiliates are skilled and others are not so adept, an attack by any group can have a significant impact on a victim. Therefore, network defenders should think about the tools and the tactics, techniques, and procedures (TTPs) that all ransomware groups and their affiliates use in the context of the technology stacks in their organizations’ environments.
CTU researchers repeat their recommendations about defending against ransomware because in nearly every single intrusion they observe or analyze, victims have not followed the guidance. This is not to say that implementing the recommendations is easy – environments are frequently complex and challenging to manage – but they should certainly feature at the top of any organization’s list of priorities.
- Patching internet-facing services prevents them from being found in the routine vulnerability scans run against networks every day.
- Robustly applying MFA, preferably the phishing-resistant variety, on all user accounts means that stolen or harvested credentials cannot be easily replayed for access.
- Using an endpoint detection and response (EDR) solution greatly increases the opportunities for detection and remediation.
- Having immutable backups in place makes for a speedier recovery from a ransomware incident, allowing organizations to return to normal business operations as soon as possible.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


