In July 2016, SecureWorks® Counter Threat Unit™ (CTU) researchers observed a threat actor creating and attempting to use a virtual machine (VM) in a compromised environment, likely to avoid detection.
CTU™ researchers were engaged to use Red Cloak™ to monitor and report on process creation activity for a client that had experienced a targeted breach. The adversary had achieved a level of access that allowed them to interact with the Windows Explorer shell via the Terminal Services Client. Figure 1 shows the threat actor using the Microsoft Management Console (MMC) to launch the Hyper-V Manager, which is used to manage Microsoft's virtual machine (VM) infrastructure.
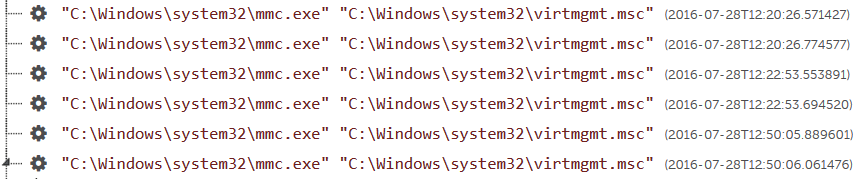
Figure 1. Adversary's use of the MMC (mmc.exe). (Source: SecureWorks)
Expanding the last process listed in Figure 1 reveals additional insight into the adversary's activity. As shown in Figure 2, the threat actor used vmconnect.exe to attempt to connect to their newly created VM, named "New Virtual Machine."
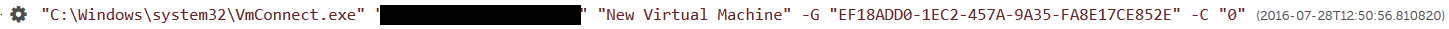
Figure 2. Adversary's use of vmconnect.exe. (Source: SecureWorks)
click to enlarge
CTU researchers immediately reported this activity to the client and requested the system's Windows Event Log files for analysis. The client extracted the files with wevtutil.exe, a native command-line Windows utility used to manage Windows Event Logs. Table 1 lists the observed events from July 28, 2016.
| Time (UTC) | Event Source/ID | Description |
| 12:50:06 | Microsoft-Windows-Sysmon/1 | Process started (mmc.exe virtmgmt.msc) |
| 12:50:44 | Microsoft-Windows-Hyper-V-VMMS/13002 | New VM created |
| Microsoft-Windows-Security-Auditing/4648 | New logon attempt using explicit credentials | |
| Microsoft-Windows-Sysmon/6 | Drivers loaded (vhdmp.sys, fsdepends.sys) | |
| 12:50:45 | Microsoft-Windows-Hyper-V-VMMS/27311 | New VM created |
| 12:50:56 | Microsoft-Windows-Sysmon/1 | Process started (vmconnect.exe) |
| 12:51:01 | Microsoft-Windows-Hyper-V-VMMS/20144 | VM failed to start |
| Microsoft-Windows-Hyper-V-VMMS/15130 | VM failed to start | |
| 12:51:08 | Microsoft-Windows-Sysmon/5 | Process terminated (vmconnect.exe) |
| 12:51:14 | Microsoft-Windows-Hyper-V-VMMS/13003 | VM deleted |
| 12:51:57 | Microsoft-Windows-Sysmon/5 | Process terminated (mmc.exe) |
Table 1. Event Log activity for July 28, 2016.
The events show the adversary using the MMC to create and attempt to launch a new VM. When the new VM did not start, the threat actor deleted it. The system that the adversary had compromised was itself a VM and therefore could not launch a new one.
These actions illustrate the lengths a threat actor will go to mask their activities and avoid detection. The client's infrastructure was instrumented with both Red Cloak and Microsoft's Sysmon utility; however, the newly created VM had neither technology installed. If the adversary had successfully launched the VM, they could have used it to conduct their activity. Deleting the VM after they were done would have removed all indicators of their actions.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)




