Microsoft on Tuesday released 113 patches affecting 11 product families. Eight of the addressed issues are considered by Microsoft to be of Critical severity, including five from the Office-365 product family. Eight have a CVSS base score of 8.0 or higher. One is known to be under active exploit in the wild, and one other is publicly disclosed.
At patch time, eight CVEs are judged more likely to be exploited in the next 30 days by the company’s estimation, in addition to the one already detected to be so. Various of this month’s issues are amenable to direct detection by Sophos protections, and we include information on those in a table below.
The release also includes advisory information on one Edge patch released last week, as well as two MITRE-issued CVEs affecting software modems from two companies whose drivers are present in Windows. (We are not including those patches in the tallies for Windows this month, but we do indicate which platforms are affected in Appendix E, along with information on which server versions are affected by each of the 88 Windows CVEs addressed this month.) There is also an update to the Servicing Stack this month.
We are as always including at the end of this post appendices listing all Microsoft’s patches sorted by severity (Appendix A), by predicted exploitability timeline and CVSS Base score (Appendix B), and by product family (Appendix C). Appendix E provides a breakout of the patches affecting the various Windows Server platforms.
By the numbers
- Total CVEs: 113
- Publicly disclosed: 1
- Exploit detected: 1
- Severity
- Critical: 8
- Important: 105
- Impact:
- Denial of Service: 2
- Elevation of Privilege: 56
- Information Disclosure: 22
- Remote Code Execution: 22
- Security Feature Bypass: 3
- Spoofing: 5
- Tampering: 3
- CVSS base score 9.0 or greater: 0
- CVSS base score 8.0 or greater: 8
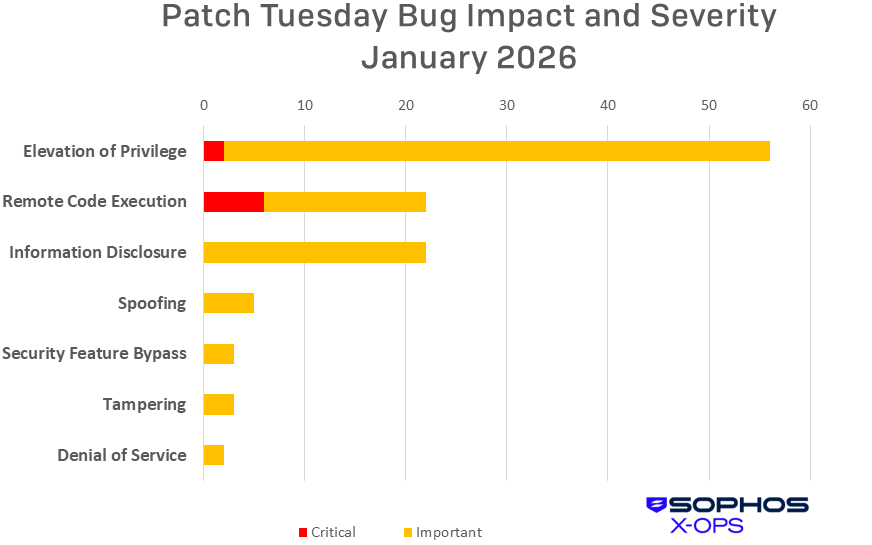
Figure 1: Not only are all seven impact categories represented in the very first Patch Tuesday of 2026, Elevation of Privilege issues continue to considerably outpace Remote Control Execution – a change we saw taking place last year and one that increasingly seems to be the new normal
Products
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect. We note, by the way, that CVE names don’t always reflect affected product families closely. In particular, some CVEs names in the Office family may mention products that don’t appear in the list of products affected by the CVE, and vice versa.
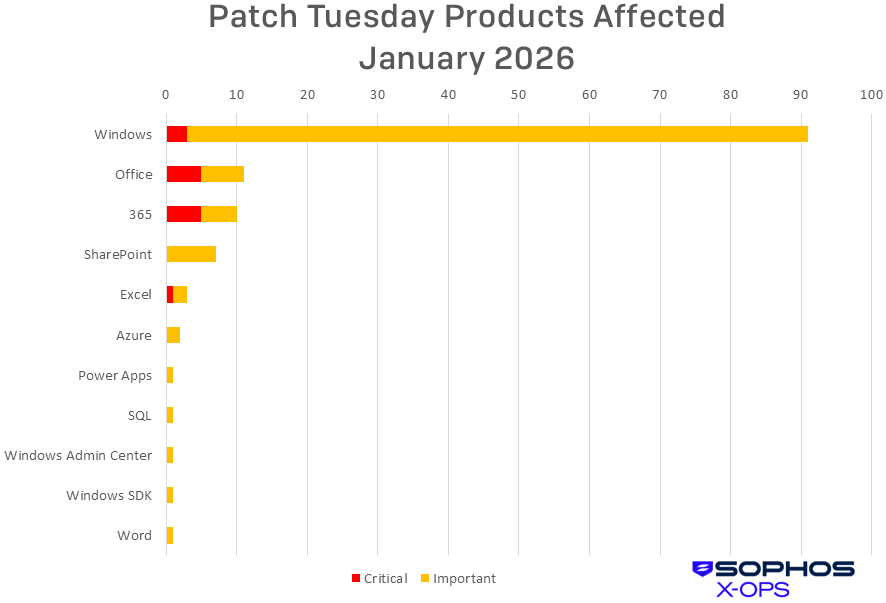
Figure 2: Windows accounts for over four-fifths of all January patches, though Office has a higher percentage of Critical-severity bugs this month. Of the rest, Windows Admin Center is counted here as neither Windows not Azure, but administrators of either should look into the Important-severity issue associated with that web tool
Notable January updates
In addition to the issues discussed above, several specific items merit attention.
CVE-2026-20944 -- Microsoft Word Remote Code Execution Vulnerability
CVE-2026-20952 – Microsoft Office Remote Code Execution Vulnerability
CVE-2026-20953 -- Microsoft Office Remote Code Execution Vulnerability
Office accounts for a disproportionate share of Critical-severity bugs this month, and the two Office issues above may be the worst of the lot. Microsoft’s own worst-case scenario for those two CVEs is troubling; an attacker could potentially gain remote code execution on the targeted user’s machine simply by sending them a link in an email – and the targeted user need not open, read, or click on the link. The Word CVE, meanwhile, has Preview Pane as a vector.
CVE-2023-31096 -- MITRE: CVE-2023-31096 Windows Agere Soft Modem Driver Elevation of Privilege Vulnerability
CVE-2024-55414 -- Windows Motorola Soft Modem Driver Elevation of Privilege Vulnerability
CVE-2026-0386 -- Windows Deployment Services Remote Code Execution Vulnerability
CVE-2026-21265 -- Secure Boot Certificate Expiration Security Feature Bypass Vulnerability
The new year is a good time for tidying up, and two advisories and two CVEs in this month’s set indicate that housekeeping may be afoot in Redmond. The two MITRE-issued CVEs cover third-party modem drivers. Microsoft is issuing an advisory simply to say that they’re both been removed from the cumulative update as of this month. Likewise, the functionality touched by CVE-2026-0386 is nearing its end of life; this concerns the Windows Deployment Services (WDS) hands-free deployment feature. Microsoft will be withdrawing that functionality in the near future – it's already legacy technology, superceded by the likes of Windows Autopilot, Microsoft InTune, and various cloud-based provisioning workflows that leverage Azure. At this point, administrators still using WDS are advised to be aware of their usage and lock it down as per instructions. Finally, the issue covered in CVE-2026-21265 involves certain upcoming certificate expirations affecting Secure Boot, and the firmware that protects updates to those certificates. Based on the provided information the vulnerability would be fairly hard to hit, but Microsoft’s attempting to get out ahead of this – and if they’re talking in January about a problem that won’t land until June (at the earliest), one is well-advised to pay attention and do the reading.
CVE-2026-20949 -- Microsoft Excel Security Feature Bypass Vulnerability
On March 25, 1992, Microsoft released Excel 4.0. Thirty-three years and ten months later, Microsoft is releasing a patch for a bug that allows local bypass of the security setting that disables XL4 (Excel 4.0) macros. Backward compatibility is widely understood to be a blessing and a curse for Microsoft, but some of this specific code is very likely older than many of the defenders who worked to patch it, if not the (anonymous) finder who dug it out. Wild.
Sophos protections
CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
|---|---|---|
| CVE-2023-31096 | Exp/2331096-A | Exp/2331096-A |
| CVE-2026-20805 | Exp/2620805-A | Exp/2620805-A |
| CVE-2026-20816 | Exp/2620816-A | Exp/2620816-A |
| CVE-2026-20817 | Exp/2620817-A | Exp/2620817-A |
| CVE-2026-20820 | Exp/2620820-A | Exp/2620820-A |
| CVE-2026-20843 | Exp/2620843-A | Exp/2620843-A |
| CVE-2026-20860 | Exp/2620860-A | Exp/2620860-A |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of January patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (56 CVEs)
| Critical severity | |
| CVE-2026-20822 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2026-20876 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2026-20803 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| CVE-2026-20808 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2026-20809 | Windows Kernel Memory Elevation of Priviledge Vulnerability |
| CVE-2026-20810 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20811 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20814 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2026-20815 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-20816 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2026-20817 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2026-20820 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2026-20826 | Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability |
| CVE-2026-20830 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-20831 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20832 | Windows Remote Procedure Call Interface Definition Language (IDL) Elevation of Privilege Vulnerability |
| CVE-2026-20836 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2026-20842 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2026-20843 | Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability |
| CVE-2026-20844 | Windows Clipboard Server Elevation of Privilege Vulnerability |
| CVE-2026-20848 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20849 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2026-20853 | Windows WalletService Elevation of Privilege Vulnerability |
| CVE-2026-20857 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2026-20858 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20859 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2026-20860 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20861 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20863 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20864 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability |
| CVE-2026-20865 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20866 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20867 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20869 | Windows Local Session Manager (LSM) Elevation of Privilege Vulnerability |
| CVE-2026-20870 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2026-20871 | Desktop Windows Manager Elevation of Privilege Vulnerability |
| CVE-2026-20873 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20874 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20877 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20918 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20919 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20920 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20921 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20923 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20924 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20926 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20929 | Windows HTTP.sys Elevation of Privilege Vulnerability |
| CVE-2026-20931 | Windows Telephony Service Elevation of Privilege Vulnerability |
| CVE-2026-20934 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20938 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2026-20940 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2026-20941 | Host Process for Windows Tasks Elevation of Privilege Vulnerability |
| CVE-2026-20943 | Microsoft Office Click-To-Run Elevation of Privilege Vulnerability |
| CVE-2026-20965 | Windows Admin Center Elevation of Privilege Vulnerability |
| CVE-2026-21221 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-21224 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
Information Disclosure (22 CVEs)
| Important severity | |
| CVE-2026-20805 | Desktop Windows Manager Information Disclosure Vulnerability |
| CVE-2026-20818 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2026-20819 | Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability |
| CVE-2026-20821 | Remote Procedure Call Information Disclosure Vulnerability |
| CVE-2026-20823 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20825 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2026-20827 | Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability |
| CVE-2026-20828 | Windows rndismp6.sys Information Disclosure Vulnerability |
| CVE-2026-20829 | TPM Trustlet Information Disclosure Vulnerability |
| CVE-2026-20833 | Windows Kerberos Information Disclosure Vulnerability |
| CVE-2026-20835 | Capability Access Management Service (camsvc) Information Disclosure Vulnerability |
| CVE-2026-20838 | Windows Kernel-Mode Driver Information Disclosure Vulnerability |
| CVE-2026-20839 | Windows Client-Side Caching (CSC) Service Information Disclosure Vulnerability |
| CVE-2026-20851 | Capability Access Management Service (camsvc) Information Disclosure Vulnerability |
| CVE-2026-20862 | Windows Management Services Information Disclosure Vulnerability |
| CVE-2026-20932 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20935 | Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability |
| CVE-2026-20936 | Windows NDIS Information Disclosure Vulnerability |
| CVE-2026-20937 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20939 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20958 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2026-20962 | Dynamic Root of Trust for Measurement (DRTM) Information Disclosure Vulnerability |
Remote Code Execution (22 CVEs)
| Critical severity | |
| CVE-2026-20854 | Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability |
| CVE-2026-20944 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20952 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20953 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20955 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20957 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2026-0386 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2026-20837 | Windows Media Remote Code Execution Vulnerability |
| CVE-2026-20840 | Windows NTFS Remote Code Execution Vulnerability |
| CVE-2026-20856 | Windows Server Update Service (WSUS) Remote Code Execution Vulnerability |
| CVE-2026-20868 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2026-20922 | Windows NTFS Remote Code Execution Vulnerability |
| CVE-2026-20946 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20947 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2026-20948 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20950 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20951 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2026-20956 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20960 | Microsoft Power Apps Remote Code Execution Vulnerability |
| CVE-2026-20963 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2026-21219 | Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability |
| CVE-2026-21226 | Azure Core shared client library for Python Remote Code Execution Vulnerability |
Security Feature Bypass (3 CVEs)
| Important severity | |
| CVE-2026-20824 | Windows Remote Assistance Security Feature Bypass Vulnerability |
| CVE-2026-20949 | Microsoft Excel Security Feature Bypass Vulnerability |
| CVE-2026-21265 | Secure Boot Certificate Expiration Security Feature Bypass Vulnerability |
Spoofing (5 CVEs)
| Important severity | |
| CVE-2026-20834 | Windows Spoofing Vulnerability |
| CVE-2026-20847 | Microsoft Windows File Explorer Spoofing Vulnerability |
| CVE-2026-20872 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2026-20925 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2026-20959 | Microsoft SharePoint Server Spoofing Vulnerability |
Tampering (3 CVEs)
| Important severity | |
| CVE-2026-20804 | Windows Hello Tampering Vulnerability |
| CVE-2026-20812 | LDAP Tampering Vulnerability |
| CVE-2026-20852 | Windows Hello Tampering Vulnerability |
Denial of Service (2 CVEs)
| Important severity | |
| CVE-2026-20875 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability |
| CVE-2026-20927 | Windows SMB Server Denial of Service Vulnerability |
Appendix B: Exploitability and CVSS
This is a list of the eight January CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release, along with the single CVE already known to be under attack. The list is arranged by CVE.
| Exploitation detected | |
| CVE-2026-20805 | Desktop Windows Manager Information Disclosure Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2026-20816 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2026-20817 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2026-20820 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2026-20840 | Windows NTFS Remote Code Execution Vulnerability |
| CVE-2026-20843 | Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability |
| CVE-2026-20860 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20871 | Desktop Windows Manager Elevation of Privilege Vulnerability |
| CVE-2026-20922 | Windows NTFS Remote Code Execution Vulnerability |
These are the January CVEs with a Microsoft-assessed CVSS Base score of 8.0 or higher. They are arranged by score and further sorted by CVE. For more information on how CVSS works, please see our series on patch prioritization schema.
| CVSS Base | CVSS Temporal | CVE | Title |
|---|---|---|---|
| 8.8 | 7.7 | CVE-2026-20868 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2026-20947 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2026-20963 | Microsoft SharePoint Remote Code Execution Vulnerability |
| 8.4 | 7.3 | CVE-2026-20952 | Microsoft Office Remote Code Execution Vulnerability |
| 8.4 | 7.3 | CVE-2026-20953 | Microsoft Office Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2026-20856 | Windows Server Update Service (WSUS) Remote Code Execution Vulnerability |
| 8.0 | 7.0 | CVE-2026-20931 | Windows Telephony Service Elevation of Privilege Vulnerability |
| 8.0 | 7.0 | CVE-2026-20960 | Microsoft Power Apps Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of January’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Certain issues for which advisories have been issued are covered in Appendix D, and issues affecting Windows Server are further sorted in Appendix E. All CVE titles are accurate as made available by Microsoft; for further information on why certain products may appear in titles and not product families (or vice versa), please consult Microsoft.
Windows (91 CVEs)
| Critical severity | |
| CVE-2026-20822 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2026-20854 | Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability |
| CVE-2026-20876 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2026-0386 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2026-20804 | Windows Hello Tampering Vulnerability |
| CVE-2026-20805 | Desktop Windows Manager Information Disclosure Vulnerability |
| CVE-2026-20808 | Windows File Explorer Elevation of Privilege Vulnerability |
| CVE-2026-20809 | Windows Kernel Memory Elevation of Priviledge Vulnerability |
| CVE-2026-20810 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20811 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20812 | LDAP Tampering Vulnerability |
| CVE-2026-20814 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2026-20815 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-20816 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2026-20817 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2026-20818 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2026-20819 | Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability |
| CVE-2026-20820 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2026-20821 | Remote Procedure Call Information Disclosure Vulnerability |
| CVE-2026-20823 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20824 | Windows Remote Assistance Security Feature Bypass Vulnerability |
| CVE-2026-20825 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2026-20826 | Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability |
| CVE-2026-20827 | Tablet Windows User Interface (TWINUI) Subsystem Information Disclosure Vulnerability |
| CVE-2026-20828 | Windows rndismp6.sys Information Disclosure Vulnerability |
| CVE-2026-20829 | TPM Trustlet Information Disclosure Vulnerability |
| CVE-2026-20830 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-20831 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20832 | Windows Remote Procedure Call Interface Definition Language (IDL) Elevation of Privilege Vulnerability |
| CVE-2026-20833 | Windows Kerberos Information Disclosure Vulnerability |
| CVE-2026-20834 | Windows Spoofing Vulnerability |
| CVE-2026-20835 | Capability Access Management Service (camsvc) Information Disclosure Vulnerability |
| CVE-2026-20836 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2026-20837 | Windows Media Remote Code Execution Vulnerability |
| CVE-2026-20838 | Windows Kernel-Mode Driver Information Disclosure Vulnerability |
| CVE-2026-20839 | Windows Client-Side Caching (CSC) Service Information Disclosure Vulnerability |
| CVE-2026-20840 | Windows NTFS Remote Code Execution Vulnerability |
| CVE-2026-20842 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2026-20843 | Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability |
| CVE-2026-20844 | Windows Clipboard Server Elevation of Privilege Vulnerability |
| CVE-2026-20847 | Microsoft Windows File Explorer Spoofing Vulnerability |
| CVE-2026-20848 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20849 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2026-20851 | Capability Access Management Service (camsvc) Information Disclosure Vulnerability |
| CVE-2026-20852 | Windows Hello Tampering Vulnerability |
| CVE-2026-20853 | Windows WalletService Elevation of Privilege Vulnerability |
| CVE-2026-20856 | Windows Server Update Service (WSUS) Remote Code Execution Vulnerability |
| CVE-2026-20857 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2026-20858 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20859 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2026-20860 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2026-20861 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20862 | Windows Management Services Information Disclosure Vulnerability |
| CVE-2026-20863 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20864 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability |
| CVE-2026-20865 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20866 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20867 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20868 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2026-20869 | Windows Local Session Manager (LSM) Elevation of Privilege Vulnerability |
| CVE-2026-20870 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2026-20871 | Desktop Windows Manager Elevation of Privilege Vulnerability |
| CVE-2026-20872 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2026-20873 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20874 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20875 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability |
| CVE-2026-20877 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20918 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20919 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20920 | Win32k Elevation of Privilege Vulnerability |
| CVE-2026-20921 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20922 | Windows NTFS Remote Code Execution Vulnerability |
| CVE-2026-20923 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20924 | Windows Management Services Elevation of Privilege Vulnerability |
| CVE-2026-20925 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2026-20926 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20927 | Windows SMB Server Denial of Service Vulnerability |
| CVE-2026-20929 | Windows HTTP.sys Elevation of Privilege Vulnerability |
| CVE-2026-20931 | Windows Telephony Service Elevation of Privilege Vulnerability |
| CVE-2026-20932 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20934 | Windows SMB Server Elevation of Privilege Vulnerability |
| CVE-2026-20935 | Windows Virtualization-Based Security (VBS) Information Disclosure Vulnerability |
| CVE-2026-20936 | Windows NDIS Information Disclosure Vulnerability |
| CVE-2026-20937 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20938 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
| CVE-2026-20939 | Windows File Explorer Information Disclosure Vulnerability |
| CVE-2026-20940 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2026-20941 | Host Process for Windows Tasks Elevation of Privilege Vulnerability |
| CVE-2026-20962 | Dynamic Root of Trust for Measurement (DRTM) Information Disclosure Vulnerability |
| CVE-2026-21221 | Capability Access Management Service (camsvc) Elevation of Privilege Vulnerability |
| CVE-2026-21265 | Secure Boot Certificate Expiration Security Feature Bypass Vulnerability |
| CVE-2026-0386 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2026-20804 | Windows Hello Tampering Vulnerability |
| CVE-2026-20805 | Desktop Windows Manager Information Disclosure Vulnerability |
Office (11 CVEs)
| Critical severity | |
| CVE-2026-20944 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20952 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20953 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20955 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20957 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2026-20943 | Microsoft Office Click-To-Run Elevation of Privilege Vulnerability |
| CVE-2026-20946 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20948 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20949 | Microsoft Excel Security Feature Bypass Vulnerability |
| CVE-2026-20950 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20956 | Microsoft Excel Remote Code Execution Vulnerability |
365 (10 CVEs)
| Critical severity | |
| CVE-2026-20944 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20952 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20953 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2026-20955 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20957 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2026-20946 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20948 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20949 | Microsoft Excel Security Feature Bypass Vulnerability |
| CVE-2026-20950 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20956 | Microsoft Excel Remote Code Execution Vulnerability |
SharePoint (7 CVEs)
| Important severity | |
| CVE-2026-20943 | Microsoft Office Click-To-Run Elevation of Privilege Vulnerability |
| CVE-2026-20947 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2026-20948 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2026-20951 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2026-20958 | Microsoft SharePoint Information Disclosure Vulnerability |
| CVE-2026-20959 | Microsoft SharePoint Server Spoofing Vulnerability |
| CVE-2026-20963 | Microsoft SharePoint Remote Code Execution Vulnerability |
Excel (3 CVEs)
| Critical severity | |
| CVE-2026-20957 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2026-20946 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2026-20950 | Microsoft Excel Remote Code Execution Vulnerability |
Azure (2 CVEs)
| Important severity | |
| CVE-2026-21224 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2026-21226 | Azure Core shared client library for Python Remote Code Execution Vulnerability |
Power Apps (1 CVE)
| Important severity | |
| CVE-2026-20960 | Microsoft Power Apps Remote Code Execution Vulnerability |
SQL (1 CVE)
| Important severity | |
| CVE-2026-20803 | Microsoft SQL Server Elevation of Privilege Vulnerability |
Windows Admin Center (1 CVE)
| Important severity | |
| CVE-2026-20965 | Windows Admin Center Elevation of Privilege Vulnerability |
Windows SDK (1 CVE)
| Important severity | |
| CVE-2026-21219 | Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability |
Word (1 CVE)
| Important severity | |
| CVE-2026-20948 | Microsoft Word Remote Code Execution Vulnerability |
Appendix D: Advisories and Other Products
There is one Edge-related advisory noted in January’s release:
| CVE-2026-0628 | Chromium: CVE-2026-0628 Insufficient policy enforcement in WebView tag |
There are also the usual Servicing Stack updates, ADV990001.
Apendix E: Affected Windows Server versions
This is a table of the 91 CVEs in the January release affecting Windows Server versions 2008 through 2025. The table differentiates among major versions of the platform but doesn’t go into deeper detail (eg., Server Core). An “x” indicates that the CVE does not apply to that version; in the case of the four client-only patches this month, we’ve italicized the whole row to emphasize that no server version is affected. We have also, for convenience, indicated information on the two Windows-related advisories (CVE-2023-31096, CVE-2024-55414), since both affect all versions of the platform.
Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure, as each reader’s situation, especially as it concerns products out of mainstream support, will vary. For specific Knowledge Base numbers, please consult Microsoft.
| CVE | S-08 | 8r2 | S-12 | 12r2 | S-16 | S-19 | S-22 | 23h2 | S-25 |
|---|---|---|---|---|---|---|---|---|---|
| CVE-2023-31096 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2024-55414 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-0386 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20804 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20805 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20808 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2026-20809 | × | × | × | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20810 | × | × | × | × | × | ■ | × | × | × |
| CVE-2026-20811 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20812 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20814 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20815 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20816 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20817 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20818 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20819 | × | × | × | × | × | × | × | × | × |
| CVE-2026-20820 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20821 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20822 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20823 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20824 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20825 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20826 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20827 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20828 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20829 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20830 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20831 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20832 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20833 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20834 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20835 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2026-20836 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20837 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20838 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20839 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20840 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20842 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20843 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20844 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20847 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20848 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20849 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20851 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20852 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20853 | × | × | × | × | × | × | × | × | × |
| CVE-2026-20854 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20856 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20857 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20858 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20859 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20860 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20861 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20862 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20863 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20864 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20865 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20866 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20867 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20868 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20869 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20870 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20871 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2026-20872 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20873 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20874 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20875 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20876 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2026-20877 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20918 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20919 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20920 | × | × | × | × | × | × | ■ | ■ | × |
| CVE-2026-20921 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20922 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20923 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20924 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-20925 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20926 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20927 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20929 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | × |
| CVE-2026-20931 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20932 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20934 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20935 | × | × | × | × | × | × | × | × | × |
| CVE-2026-20936 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20937 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20938 | × | × | × | × | × | × | × | × | × |
| CVE-2026-20939 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2026-20940 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | × | × |
| CVE-2026-20941 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-20962 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2026-21221 | × | × | × | × | × | × | × | × | ■ |
| CVE-2026-21265 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


