Qu’est-ce que la chasse aux menaces ?
En matière de cybersécurité, les organisations ne peuvent pas se permettre de rester passives. Les acteurs malveillants sont aujourd’hui plus rusés que jamais, déployant de plus en plus de techniques de contournement pilotées manuellement pour mener à bien leurs attaques. C’est pourquoi la pratique de la chasse aux menaces est désormais essentielle pour protéger les organisations. En recherchant et en neutralisant de manière proactive les menaces avant qu’elles ne fassent des dégâts, les organisations ont de meilleures chances de se protéger contre les adversaires actifs.
À propos de la chasse aux menaces
La chasse aux menaces est une forme de cybersécurité dans laquelle les professionnels de la sécurité recherchent de manière proactive sur un réseau, des systèmes, des applications ou des appareils connectés tout signe d’activité potentiellement malveillante menée par un adversaire actif. La chasse aux menaces est généralement effectuée en associant des techniques de sécurité manuelles et automatisées telles que l’analyse des données du journal pour détecter les anomalies, la réalisation d’analyses de réseau ou l’utilisation de flux de renseignements. L’objectif principal de la chasse aux menaces est de détecter rapidement les comportements potentiellement malveillants qui pourraient passer sous les radars d’autres formes d’outils de sécurité.
À bien des égards, la chasse aux menaces informatiques est similaire à la chasse dans le monde réel. Plutôt que d’attendre qu’une cible vienne à eux, les chasseurs recherchent les potentiels acteurs malintentionnés et activités malveillantes. Ces professionnels de la sécurité hautement qualifiés travaillent souvent pour un fournisseur de services de sécurité managé (MSSP) ou un centre d’opérations de sécurité (SOC) interne.
Pourquoi la chasse aux menaces est-elle si importante ?
Dans notre enquête menée auprès de 3 000 professionnels de l’informatique répartis dans 14 pays, près d’un quart (23 %) des entreprises ont été victimes d’une cyberattaque impliquant un adversaire actif au cours de l’année écoulée[1]. Ces résultats sont préoccupants.
Les attaques de cette nature sont notoirement difficiles à détecter, car les acteurs malveillants adaptent leurs techniques, tactiques et procédures (TTP) de manière instantanée en utilisant des actions manuelles et en temps réel en réponse aux actions des technologies de sécurité et des défenseurs, mais aussi comme tactique pour échapper à la détection.
Cela illustre que la technologie seule ne suffit plus à bloquer 100 % des menaces. La chasse aux menaces est donc essentielle pour repérer et neutraliser les menaces non détectables par des moyens traditionnels.
[1] L’état de la cybersécurité en 2023 - Sophos
Quelle est la relation entre les services MDR (Managed Detection and Response) et la chasse aux menaces ?
Si la chasse aux menaces et la stratégie MDR (Managed Detection and Response) semblent identiques, elles n’en demeurent pas moins fondamentalement différentes dans la mesure où la première est bien souvent une composante de la deuxième.
La stratégie MDR a une portée plus large : il s’agit d’une approche globale et entièrement externalisée de la cybersécurité qui implique une surveillance constante des terminaux, du réseau, de la sécurité du Cloud et des identités des utilisateurs d’une entreprise pour détecter les menaces et anomalies connues.
Les services MDR s’appuient sur un logiciel de sécurité qui envoie des alertes et des informations de sécurité automatisées aux professionnels de la sécurité. Le système d’alerte se base sur des failles connues et fait remonter les menaces détectées en fonction de flux logiques et de critères spécifiques définis par le professionnel de la sécurité.
La chasse aux menaces peut quant à elle être externalisée (auprès d’un fournisseur de services MDR ou MSSP) ou menée en interne par le SOC d’une organisation.
Lors d’une chasse aux menaces, le professionnel de la sécurité passe activement au crible les systèmes à la recherche de menaces, au lieu de recevoir passivement des alertes du logiciel. Alors que la stratégie MDR se concentre sur l’utilisation de logiciels et de flux automatisé pour surveiller les menaces connues, la chasse aux menaces combine outils informatiques et intervention humaine. Le chasseur ne sait pas forcément toujours ce qu’il cherche. Les recherches de menaces peuvent être basées sur des vulnérabilités connues ou inconnues, des comportements suspects connus ou inconnus, ou des indices, et sont menées par des professionnels de la sécurité hautement qualifiés.
Un bon service MDR intégrera la chasse aux menaces comme partie intégrante du processus de détection et de réponse. Dans le cas de Sophos MDR, nos analystes de sécurité recherchent de manière proactive les menaces qui contournent les produits de sécurité avant d’en déterminer la gravité et de prendre les mesures appropriées.
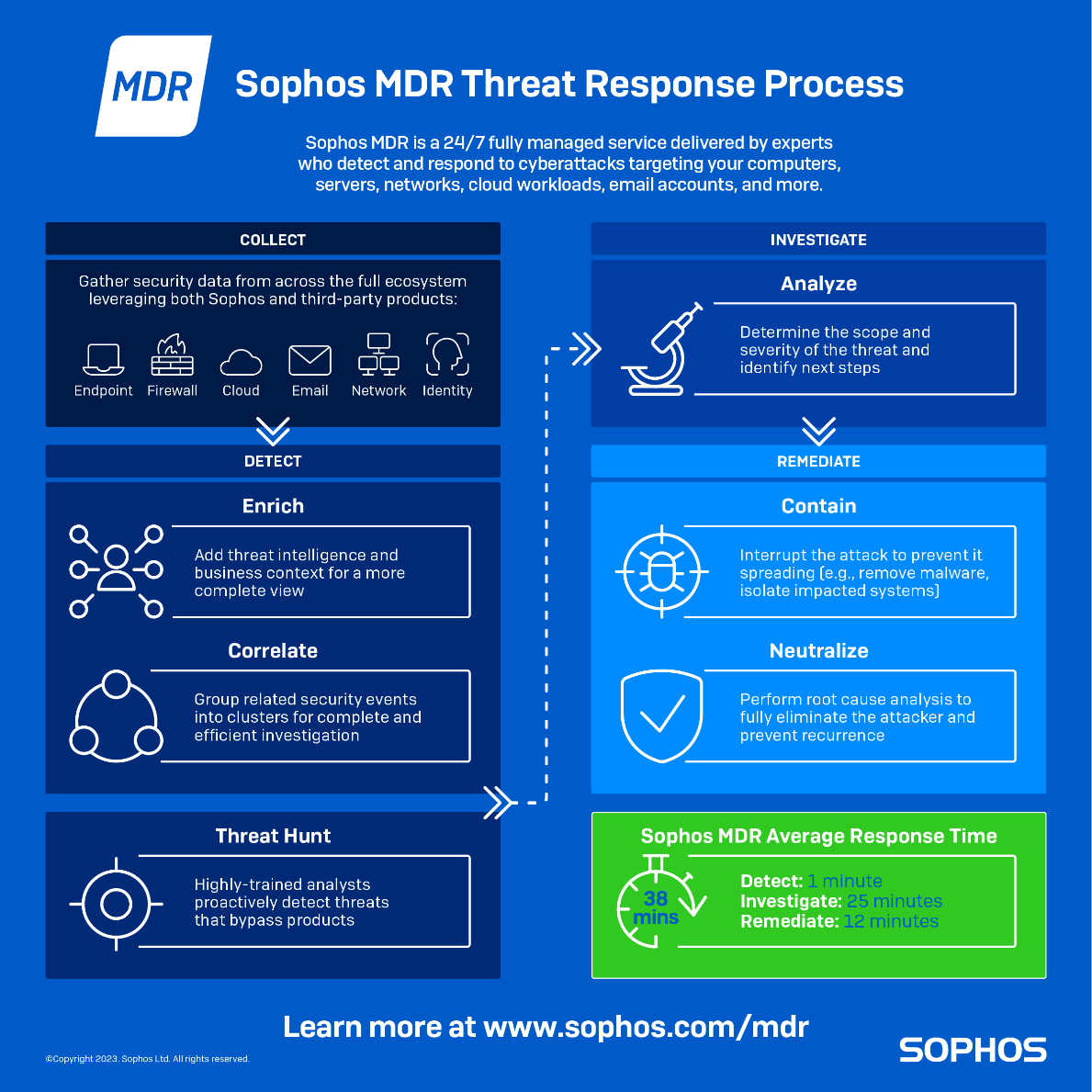
Comment sont menées les chasses aux menaces ?
Les chasseurs de menaces expérimentés partent du principe qu’une menace potentielle a déjà échappé aux défenses d’une organisation et qu’elle est à présent en passe de s’infiltrer dans les systèmes. L’objectif ultime de la chasse aux menaces est de limiter le temps de séjour d’un attaquant au sein du système. En réduisant le temps de détection, les chasseurs de menaces peuvent limiter les dommages causés par une attaque, voire l’arrêter avant qu’elle ne produise ses effets.
Dans la plupart des cas, les chasseurs de menaces se concentrent sur deux catégories de menaces :
- La chasse aux menaces à partir d’indices : situation dans laquelle le comportement de l’attaquant a déclenché une alerte dans une ou plusieurs couches de défense.
- La chasse aux menaces sans indices de départ : forme plus proactive de chasse aux menaces dans laquelle aucune alerte n’a été déclenchée. Il s’agit d’une chasse aux menaces courantes pour les menaces inconnues ou de type Zero-Day.
En général, les interventions de ce type nécessitent le plus d’efforts humains et sont les plus délicates, en raison des risques soulevés par ce genre de menaces. Dans les deux cas, les menaces détectées sont triées, traitées et neutralisées par l’équipe de chasseurs de menaces.
Au cours d’une chasse, les analystes de sécurité étudient les tactiques, techniques et procédures (TTP) utilisées par les acteurs malveillants pour déterminer le stade potentiel de l’attaque et obtenir des informations. Une fois cette étape réalisée, les équipes prendront une mesure appropriée pour neutraliser la menace si nécessaire.
Une stratégie de chasse aux menaces comporte cinq composantes principales :
- Prévention. Disposer de technologies de prévention des violations de données robustes et correctement configurées (telles que la sécurité Endpoint) peut empêcher la plupart des attaquants de s’infiltrer dans le réseau de votre entreprise. Ces outils permettent aussi de réduire le nombre d’alertes de sécurité générées au quotidien. Avec moins d’alertes à traiter, le chasseur de menaces peut se concentrer sur les signaux les plus importants, qui trahissent la présence des acteurs les plus dangereux : les adversaires évasifs pilotant manuellement leurs attaques.
- Collecte. Pour mener à bien une chasse aux menaces, les analystes de sécurité ont besoin d’accéder à des données de sécurité riches provenant de l’environnement à protéger. Pour ce faire, les entreprises ont besoin de systèmes de surveillance des menaces et de sécurité qui collectent constamment des données sur l’environnement. La collecte de données fournit des indices précieux aux chasseurs de menaces. Elle leur permet de définir une base de références, puis de comparer et de mettre en contraste les comportements normaux et suspects au sein de l’environnement. Sans le bon type, le bon volume et la bonne qualité de données, il est difficile pour les chasseurs de menaces d’identifier avec précision les indicateurs d’attaque potentielle. Les données sans contexte compliquent la prise de décision des analystes. Sans métadonnées significatives associées au signal, l’équipe aura du mal à déterminer s’il s’agit de signaux malveillants ou bénins.
- Priorisation. Le chasseur de menaces utilise les données, avec le contexte, pour déchiffrer les signaux qui comptent puis prendre les décisions qui s’imposent. Pour éviter d’être submergés par les données et de manquer les éléments qui méritent d’être examinés, ces experts de la chasse aux menaces doivent être capables d’identifier les alertes qui comptent. Plus on parvient à améliorer les ratios signal/bruit en utilisant une combinaison de contextes que seuls les producteurs d’événements peuvent fournir avec l’intelligence artificielle automatisée, mieux ce sera. Même avec l’automatisation, le processus n’est pas simple.
- Investigation. Une fois que les signaux clés sont isolés, le chasseur de menaces va les comparer aux cadres et modèles de l’industrie, tels que le cadre MITRE ATT&CK. Le but est de construire un seuil de confiance pour décider si le signal pointe vers un comportement malveillant ou bénin.
- Action. Si le chasseur de menaces établit que le signal pointe vers une menace réelle, l’équipe doit accomplir deux actions. Dans un premier temps, elle s’attache à atténuer le problème immédiat. Ensuite, elle traquera et neutralisera la cause première de la menace. Parfois, il suffira de mettre une machine en quarantaine ou de la déconnecter du réseau. D’autres fois, le chasseur de menaces devra intervenir en profondeur dans un réseau pour en extraire l’attaquant et s’assurer qu’il ne peut pas recommencer. En effet, ce n’est pas parce que l’on a réussi à bloquer et à supprimer les malwares d’un système et que l’on ne voit plus l’alerte que l’attaquant a été totalement éliminé de l’environnement.
Les chasseurs de menaces professionnels, qui voient des milliers d’attaques, savent quand et où il faut approfondir. Ils analysent tout ce que les attaquants font, ont fait ou prévoient de faire sur le réseau, puis veillent à le neutraliser.
Est-il préférable d’externaliser la chasse aux menaces ou de la gérer en interne ?
Qu’elle soit gérée en interne ou confiée à un fournisseur de solutions de sécurité, la chasse aux menaces repose sur le centre d’opérations de sécurité ou SOC.
Si votre entreprise choisit de mettre en œuvre et de gérer elle-même la chasse aux menaces, il est essentiel qu’elle se dote de son propre SOC dédié. Un SOC est une fonction interne centralisée qui se concentre sur la surveillance, la détection, l’investigation et la réponse aux cybermenaces tout en améliorant la posture de sécurité globale de votre organisation. Les analystes de sécurité de votre SOC servent d’équipe de référence pour tout ce qui concerne la cybersécurité et les menaces de sécurité potentielles.
Gérer votre initiative de chasse aux menaces en interne présente des atouts et des inconvénients. En choisissant de créer votre propre équipe interne de chasse aux menaces, votre entreprise disposera d’une ressource dédiée entièrement axée sur la sécurité continue de votre environnement. Pour les organisations qui se sont déjà dotées d’un SOC, une équipe de chasseurs de menaces peut permettre d’étendre la portée des activités déjà menées. Une équipe interne connaît mieux que quiconque l’environnement de votre entreprise, ce qui peut souvent se traduire par des temps de réponse et de détection des menaces plus rapides.
Pour les organisations qui ne disposent pas déjà d’un SOC interne, la constitution d’une équipe interne n’est pas sans poser quelques difficultés. L’un des principaux défis est celui consistant à recruter des professionnels de la sécurité possédant les compétences et l’expérience requises. Sans compter qu’il est aussi très difficile de trouver le bon équilibre entre les compétences humaines et les outils de cybersécurité qui les sous-tendent.
Les organisations qui optent pour l’externalisation de la chasse aux menaces bénéficient en outre d’un centre d’opérations de sécurité (SOC) préexistant. Lorsque vous travaillez avec un fournisseur de Cybersécurité as a Service, vous aurez à votre disposition une plus grande équipe d’analystes de sécurité chevronnés. Ces experts auront déjà passé des milliers d’heures à lutter contre tout ce que les adversaires peuvent leur opposer. Ils pourront également tirer des leçons des attaques subies par une organisation dans le SOC et transférer ce qu’ils ont appris à l’ensemble de leurs clients. Un autre avantage est l’évolutivité : une équipe SOC externalisée peut fournir un support 24/7 aux grandes entreprises disposant de plusieurs sites et même aux travailleurs distants.
Quels sont les outils de cybersécurité couramment utilisés par les chasseurs de menaces ?
La visibilité est cruciale pour les chasseurs de menaces. Afin de stopper une cybermenace avancée avant qu’elle ne cause des dommages majeurs, les analystes doivent être en mesure de voir les tentatives d’intrusion, les entrées non autorisées sur le réseau et d’autres comportements suspects à mesure qu’ils se produisent. C’est là que les technologies de cybersécurité — qui agissent en quelque sorte comme les yeux et les oreilles de la stratégie de sécurité — viennent épauler le chasseur de menaces. Le chasseur de menaces peut ainsi décider d’approfondir l’analyse d’un système ou d’un réseau afin de trouver des preuves d’un incident de sécurité.
Les solutions technologiques telles que la sécurité Endpoint Next-Gen et les pare-feux constituent des couches de défense critiques. Ils permettent de stopper les attaques avancées menées manuellement.
La plupart des entreprises ont déjà déployé ces outils et les utilisent pour rassembler une grande partie des données télémétriques brutes dont les chasseurs de menaces se servent pour évaluer les risques et, le cas échéant, approfondir leurs connaissances.
Les solutions de sécurité Endpoint, pare-feu, d’identité, de messagerie, Cloud et réseau génèrent toutes des informations précieuses qui permettent aux chasseurs de menaces de détecter et d’identifier les attaques sophistiquées et d’y répondre.
Une fois que les chasseurs de menaces disposent de la visibilité nécessaire, ils peuvent exploiter les données télémétriques de sécurité pour en tirer des informations exploitables. Ceci est considéré comme une compétence spécialisée. Le chasseur de menaces utilise les données télémétriques pour agir plus rapidement et prendre des décisions plus éclairées. Alors que de nombreuses technologies génèrent des alertes de sécurité et des informations utiles pour des analystes hautement qualifiés, l’exploitation à proprement parler des informations est une tout autre histoire. Et c’est là que les chasseurs de menaces hautement qualifiés entrent en jeu.
Les chasseurs de menaces utilisent des outils de télémétrie et des logiciels de sécurité automatisés pour parcourir d’énormes masses de données. Pour mener à bien leur recherche, ils s’appuient sur les données collectées à partir de plateformes MDR (Managed Detection and Response), de solutions de gestion des événements et des informations de sécurité (SIEM) et d’outils d’analyse de la sécurité.
Les chasseurs de menaces exploitent aussi les solutions EDR (Endpoint Detection and Response) et XDR (Extended Detection and Response), pour repérer rapidement les comportements suspects et les investiguer en profondeur. Le logiciel EDR fournit des entrées à partir de tous les terminaux de l’environnement. En revanche, le XDR corrèle les signaux provenant de l’environnement informatique au sens large, notamment des solutions de pare-feu, de sécurité mobile, de messagerie et sécurité du Cloud.
Qui sont les chasseurs de menaces et quelles compétences possèdent-ils ?
La chasse aux menaces est une opération très complexe. En toute logique, les personnes qui travaillent comme chasseurs de menaces doivent posséder un ensemble de compétences spécifiques.
Les caractéristiques typiques d’un bon chasseur de menaces sont les suivantes :
- Curiosité intellectuelle : traquer les menaces revient souvent à chercher une aiguille dans une botte de foin. Les chasseurs de menaces peuvent souvent passer des jours à chercher des menaces, en utilisant de nombreuses méthodes pour les dénicher. Le chasseur doit être d’un naturel curieux et créatif pour ne pas perdre le fil et parvenir à résoudre les problèmes.
- Vaste expérience en cybersécurité : la chasse aux menaces est l’une des opérations les plus avancées en matière de cybersécurité. Il est essentiel pour les chasseurs de menaces d’avoir une expérience préalable dans le domaine de la cybersécurité et une connaissance fondamentale des vecteurs d’attaque les plus courants.
- Connaissance du paysage des menaces : tout chasseur de menaces qui se respecte s’informe sur les dernières tendances en matière de menaces, car elles évoluent constamment.
- Aptitude à penser comme un hacker : L’un des attributs clés d’un chasseur de menaces est la capacité à penser comme un pirate informatique.
- Capacité de rédaction technique : les chasseurs de menaces sont tenus de consigner (logs) toutes leurs découvertes dans le cadre du processus d’investigation. Ils doivent être capables de faire passer des informations complexes à des parties prenantes qui ne sont pas forcément très au fait de la technique.
- Expertise en systèmes d’exploitation et en réseau : en dehors de l’expérience en cybersécurité, une connaissance pratique avancée des systèmes d’exploitation et des outils réseau courants est essentielle.
- Expérience en codage/scripting : incontournable pour aider les chasseurs de menaces à créer des programmes, à automatiser des tâches, à analyser les journaux (logs) et à effectuer des tâches d’analyse de données pour faciliter et faire progresser leurs investigations.
Malheureusement, les professionnels de la sécurité disposant de ces compétences spécifiques font cruellement défaut. Sans compter que le recrutement de chasseurs de menaces chevronnés est loin d’être donné. Aussi, de nombreuses entreprises font appel à des fournisseurs de services MDR ou MSSP, car ces derniers sont plus susceptibles de disposer d’un personnel doté de l’expertise requise à un coût plus abordable.
Quelles sont les mesures nécessaires à la mise en place d’un programme de chasse aux menaces ?
La préparation est la clé du succès de toute initiative de cybersécurité, et la chasse aux menaces ne fait pas exception. Qu’il s’agisse de lancer un programme interne de chasse aux menaces ou de passer par un prestataire, l’environnement de votre entreprise doit être adapté à la tâche. Il est important de s’appuyer sur des bases solides avant de commencer à traquer les menaces.
Voici cinq étapes pour garantir la réussite du programme de chasse aux menaces de votre organisation :
- Identifier la maturité de vos opérations de cybersécurité actuelles. Le mapping de vos processus avec un modèle de maturité de la cybersécurité (tel que le CMMC, Cybersecurity Maturity Model Certification) est un excellent moyen d’établir dans quelle mesure vous êtes bien équipé (ou non) pour commencer la chasse aux menaces. Il est également judicieux d’auditer votre posture de sécurité afin de déterminer votre niveau de vulnérabilités aux menaces.
- Déterminer comment vous voulez mener votre chasse aux menaces Une fois que vous avez établi votre maturité cybernétique, il est temps de décider si les activités de chasse aux menaces seront réalisées en interne, entièrement externalisées, ou si elles combineront les deux.
- Identifier les failles technologiques. Passez en revue vos outils existants et identifiez ce dont vous avez besoin pour effectuer une chasse aux menaces efficace. Quelle est l’efficacité de votre technologie de prévention ? Possède-t-il ou prend-il en charge des capacités de chasse aux menaces ?
- Identifier les lacunes en matière de compétences La chasse aux menaces exige des compétences spécialisées. Si vous ne disposez pas de l’expérience nécessaire en interne, envisagez de suivre des formations pour vous aider à développer les compétences requises. Envisagez également de travailler avec un prestataire externe pour compléter votre équipe.
- Élaborer et mettre en œuvre un plan de réponse aux incidents Il est essentiel de mettre en place un plan de réponse aux incidents complet, afin de garantir que toute réponse soit mesurée et contrôlée. Un plan de réponse bien préparé et bien compris, que toutes les parties clés peuvent immédiatement mettre en œuvre, réduira considérablement l’impact d’une attaque sur votre organisation.
À propos de la chasse aux menaces de Sophos
Sophos Managed Detection and Response (MDR) offre de nombreux avantages par rapport à un programme interne de chasse aux menaces. Le plus grand avantage de ces fournisseurs est l’expérience.
L’équipe Sophos MDR a des milliers d’heures d’expérience à son actif. Elle peut fournir une assistance 24/7 partout dans le monde. Pour discuter de la manière dont Sophos peut soutenir l’initiative de chasse aux menaces de votre organisation.
Contactez-nous dès aujourd’hui
Sujet connexe : Quels sont les différents types d’acteurs malveillants ?
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)