In late 2025, SophosLabs analysts investigated several WantToCry remote ransomware incidents. In each case, the attackers used virtual machines with autogenerated NetBIOS hostnames derived from Windows templates provisioned by ISPsystem, a legitimate provider of IT infrastructure management platforms. Counter Threat Unit™ (CTU) researchers investigated the potential scale of malicious use of these devices and identified multiple internet-exposed systems associated with cybercriminal activity, including ransomware operations and commodity malware delivery. Further investigation identified multiple additional hostnames derived from ISPsystem-provisioned virtual machine templates, some of which were also used in malicious activity.
Based on CTU™ and third-party observations, the two hostnames used in the WantToCry ransomware activity (WIN-J9D866ESIJ2 and WIN-LIVFRVQFMKO) have been used in multiple incidents. This malicious activity includes cybercriminal attacks involving LockBit, Qilin, and BlackCat (also known as ALPHV) ransomware, and an additional deployment of NetSupport RAT. In late 2021, a user called “Bentley” (later identified as Maksim Galochkin and sanctioned by the U.S. and UK governments) used a device with the hostname WIN-LIVFRVQFMKO to log in to a private Jabber chat involving members of GOLD ULRICK, which operates Conti ransomware, and GOLD BLACKBURN, which operates TrickBot. These chat logs were exposed by an apparent insider in the February 2022 “ContiLeaks” operation. In July 2023, a device with the same hostname was used in a Ursnif campaign targeting organizations in Italy, and in December 2024, Kaspersky reported on its use in the exploitation of a FortiClient EMS vulnerability.
It would be tempting to conclude that each hostname is used by a single threat actor engaging in a range of criminal behavior. However, according to the Shodan search engine, the two hostnames were associated with thousands of internet-facing devices exposing RDP services (TCP port 3389) in December 2025. As of December 19, there were 3,645 live hosts exposing the hostname WIN-J9D866ESIJ2 and 7,937 with hostname WIN-LIVFRVQFMKO. Most of the devices using these hostnames were in Russia, with some in other Commonwealth of Independent States (CIS), Europe, and the U.S. (see Figure 1). A few devices with the hostname WIN-LIVFRVQFMKO were in Iran.
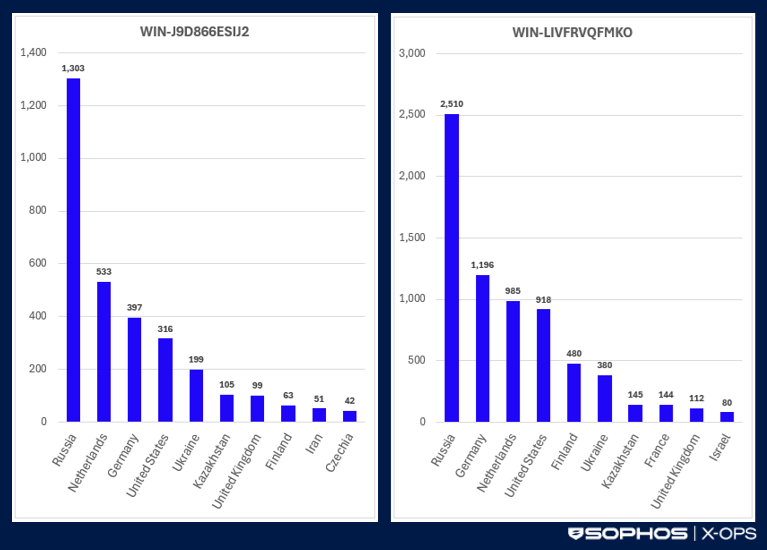
Figure 1: Locations of devices using these hostnames based on associated IP address
Multiple hosting providers were associated with these hostnames, but the most prevalent were Stark Industries Solutions Ltd, Zomro B.V., First Server Limited, Partner Hosting LTD, and JSC IOT (see Tables 1 and 2).
| WIN-J9D866ESIJ2 hosting providers | # of hosts |
|---|---|
| First Server Limited | 592 |
| Stark Industries Solutions Ltd | 576 |
| Zomro B.V. | 308 |
| Global Connectivity Solutions LLP | 189 |
| Kontel LLC | 148 |
Table 1: Top 5 providers hosting WIN-J9D866ESIJ2 virtual machines
| WIN-LIVFRVQFMKO hosting providers | # of hosts |
| Stark Industries Solutions Ltd | 634 |
| Zomro B.V. | 455 |
| First Server Limited | 414 |
| Partner Hosting LTD | 356 |
| JSC IOT | 355 |
Table 2: Top 5 providers hosting WIN-LIVFRVQFMKO virtual machines
While there is likely to be some legitimate activity originating from virtual machines with these hostnames from these hosting providers, there is additional data that links the top two providers (Stark Industries Solutions Ltd and First Server Limited) to cybercriminal and Russian state-sponsored operations. CTU and third-party researchers have observed multiple state-sponsored and cybercriminal threat groups use Stark Industries Solutions Ltd infrastructure since its founding in February 2022, just before Russia’s invasion of Ukraine. In May 2025, the European Council issued “restrictive measures” against Stark Industries Solutions Ltd and its operators for enabling “various Russian state-sponsored and affiliated actors to conduct destabilizing activities.” Meanwhile, third-party research suggests that First Server Limited is closely connected to Doppelganger, a Russian disinformation campaign whose operators and associated entities were sanctioned by the UK government in October 2024. The concentration of these hostnames among a relatively small number of hosting providers and geographic regions appears to be consistent with large-scale deployment of preconfigured virtual machine templates, rather than independent infrastructure build-out by individual threat actors.
Further investigation revealed that these hostnames originate from widely reused Windows Server images distributed through the control panel of the legitimate ISPsystem VMmanager virtualization management platform. CTU researchers hypothesized that deployment of an image would assign the same hostname and self-signed certificate subject, which could create the appearance of shared infrastructure across otherwise unrelated threat actors. To validate this hypothesis, CTU researchers procured a virtual server from play2go.cloud, a hosting provider observed to use ISPsystem VMmanager, and deployed a Windows virtual machine under standard customer conditions. The resulting system automatically generated the hostname WIN-J9D866ESIJ2, consistent with the pattern observed across internet-exposed infrastructure.
CTU researchers independently deployed a controlled test environment using a trial installation of VMmanager, enabling direct deployment of Windows virtual machines. Systems provisioned from VMmanager’s default Windows templates consistently generated the same static hostnames. This testing led CTU researchers to identify and analyze a publicly accessible repository of prebuilt operating system images used by VMmanager for template-based virtual machine deployment.
This repository includes multiple Windows Server templates spanning Windows Server 2012 R2 through Windows Server 2025, as well as Windows 10 and Windows 11 desktop variants. Analysis of these images and their associated deployment scripts confirmed that the hostname and related system identifiers are embedded within each template and are not randomized during provisioning. CTU researchers used Shodan to investigate the prevalence of these hostnames on the internet (see Table 3).
| Hostname | OS version | Total hosts | Top country | Top hosting provider |
|---|---|---|---|---|
| WIN-LIVFRVQFMKO | Windows Server 2019 (KMS) | 7,937 | Russia | Stark Industries Solutions Ltd |
| WIN-BS656MOF35Q | Windows Server 2022 (KMS) | 7,825 | Germany | Stark Industries Solutions Ltd |
| WIN-344VU98D3RU | Windows Server 2012 R2 | 7,437 | Netherlands | Zomro B.V. |
| WIN-J9D866ESIJ2 | Windows Server 2016 | 3,645 | Russia | First Server Limited |
| WIN-9C3K8L5M5Q7 | Windows Server 2022 (GPT) | 541 | Russia | Stark Industries Solutions Ltd |
| DESKTOP-7VBH2AA | Windows 11 (Dec 2025) | 177 | U.S. | Stark Industries Solutions Ltd |
| WIN-E9VUEDVSAHR | Windows Server 2019 (Russian GPT) | 170 | Russia | JSC IOT |
| WIN-3R1Q4OEL7SH | Windows Server 2019 Datacenter | 152 | Russia | Stark Industries Solutions Ltd |
| WIN-EGR0637MAEG | Windows Server 2019 (GPT) | 100 | U.S. | Stark Industries Solutions Ltd |
| WIN-5BIER8OOA6N | Windows Server 2025 | 66 | Czechia | SmartApe OU |
| WIN-67KRP38M7IH | Windows Server Core 2019 | 4 | Netherlands | Stark Industries Solutions Ltd |
| WIN-98FDM29KPEE | Windows 10 | 0 | N/A | N/A |
| WIN-QLUI838SCU0 | Windows 10 (Russian) | 0 | N/A | N/A |
| WIN-P7Q737OF0AM | Windows 11 (Aug 2024) | 0 | N/A | N/A |
Table 3: ISPsystem virtual machine hostnames and their prevalence on the internet as of December 19, 2025
The four most prevalent hostnames account for over 95% of the total number of internet-facing ISPsystem virtual machines. It is unsurprising that the two most popular images (WIN-LIVFRVQFMKO and WIN-BS656MOF35Q) are Key Management Service (KMS)-enabled variants, allowing the Windows OS to operate for free during a 180-day grace period without individual licensing.
CTU researchers investigated all the hostnames for evidence of malicious activity. The analysis revealed that these four most prevalent hostnames, which include the two SophosLabs analysts observed in WantToCry attacks, were used in cybercriminal activity (see Table 4). All were observed in Sophos customer detection data or telemetry in some capacity.
| Hostnames | OS Version | Observed malicious activity |
|---|---|---|
| WIN-LIVFRVQFMKO | Windows Server 2019 | LockBit Conti Qilin WantToCry BlackCat (ALPHV) Conti chat logs (referenced by "Bentley" on Jabber) FortiClient EMS vulnerability exploitation Ursnif |
| WIN-BS656MOF35Q | Windows Server 2022 | ClickFix, PureRAT, and Lumma stealer campaign Cerberus Team malware campaigns |
| WIN-344VU98D3RU | Windows Server 2012 R2 | RedLine infostealer Lampion infostealer |
| WIN-J9D866ESIJ2 | Windows Server 2016 | WantToCry NetSupport RAT |
Table 4: Hostnames and connections to malicious activity
CTU researchers searched for these hostnames on underground forums and communication platforms such as Telegram and discovered advertisements for bulletproof hosting (BPH) providers. The operators of BPH services knowingly permit the hosting of illicit content while maintaining infrastructure that threat actors can rely on to remain operational in the face of abuse reports, takedown requests, and law enforcement action. The infrastructure commonly supports ransomware command and control (C2) servers, malware distribution, phishing campaigns, botnet management, and data exfiltration staging.
CTU researchers identified extensive references to a provider named MasterRDP in datasets associated with systems exposing ISPsystem-derived hostnames. Underground forum posts and public Telegram activity advertise BPH, virtual private server (VPS) access, and RDP services under this branding.
It is highly likely that MasterRDP is one of many BPH providers within the cybercriminal ecosystem that lease ISPsystem virtual machines hosted on abuse-tolerant infrastructure to customers with malicious intentions, including those engaged in ransomware operations and malware delivery. ISPsystem VMmanager is a legitimate commercial virtualization management platform widely used across the hosting industry, and the software itself is not malicious. However, its low cost, low barrier to entry, and turnkey deployment capabilities make it attractive to cybercriminals while its widespread legitimate use provides operational cover among thousands of compliant deployments.
2026-02-09 update: Erroneous references suggesting a business relationship between MasterRDP and rdp.monster have been removed. Thanks to rdp.monster for bringing this error to our attention.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


