Sophos, a global leader in next-generation cybersecurity, today published its latest findings into real world attacks investigated by its Rapid Response team. The article, “Nefilim Ransomware Attack Uses ‘Ghost’ Credentials,” details how a failure to keep close tabs on “ghost” account credentials facilitated two recent cyberattacks, one of which involved Nefilim ransomware.
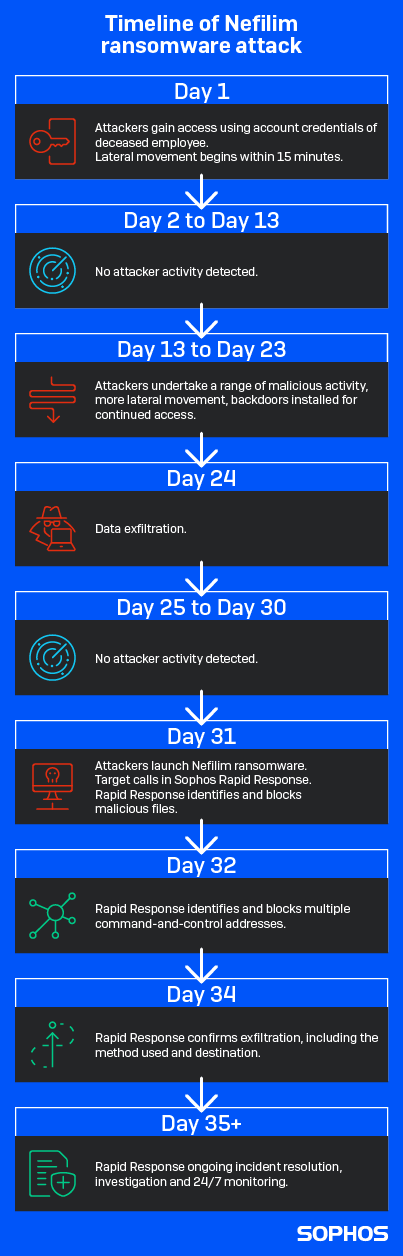
Nefilim, also known as Nemty ransomware, combines data theft with encryption. The target hit by Nefilim had more than 100 systems impacted. Sophos responders traced the initial intrusion to an admin account with high level access that attackers had compromised more than four weeks before they released the ransomware. During this time, the attackers were able to quietly move through the network, steal credentials for a domain admin account, and find and exfiltrate hundreds of GB of data, before unleashing the ransomware that revealed their presence.
The hacked admin account that enabled this belonged to an employee who had sadly passed away around three months previously. The company had kept the account active because it was used for a number of services.
In the second, unrelated attack, Sophos responders found that intruders had created a new user account and added it to the target’s domain admin group in Active Directory. With this new new domain admin account, the attackers were able to delete approximately 150 virtual servers and encrypt the server backups using Microsoft Bitlocker – all without setting off alerts.
“If it wasn’t for the ransomware that flagged the presence of intruders, how long might the attackers have had domain admin access to the network without the company knowing?” said Peter Mackenzie, manager, Sophos Rapid Response. “Staying on top of account credentials is basic, but critical cybersecurity hygiene. We see far too many incidents where accounts have been set up, often with considerable access rights, that are then forgotten about, sometimes for years. Such ‘ghost’ accounts are a prime target for attackers.
“If an organization really needs an account after someone has left the company, they should implement a service account and deny interactive logins to prevent any unwanted activity. Or, if they don’t need the account for anything else, disable it and carry out regular audits of Active Directory.
“The danger is not just keeping outdated and unmonitored accounts active; it is also giving employees greater access rights than they need. Fewer accounts need to be a domain admin than most people think. No account with privileges should be used by default for work that doesn't require that level of access. Users should elevate to using the required accounts when needed and only for that task. Further, alerts should be set so that if the domain admin account is used or if a new admin account is created, someone knows.”
Nefilim ransomware was first reported on in March 2020. Like other ransomware families such as Dharma, Nefilim mainly targets vulnerable Remote Desktop Protocol (RPD) systems as well as exposed Citrix software. It is one of a growing number of ransomware families, alongside DoppelPaymer and others that engages in so-called “secondary extortion,” with attacks that combine encryption with data theft and the threat of public exposure.
Further information on the incidents, including Indicators of Compromise (IoCs) and tactics, techniques and procedures (TTPs) for the Nefilim attack, can be found in “Nefilim Ransomware Attack Uses ‘Ghost’ Credentials.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)
