A finales de 2025, los analistas de SophosLabs investigaron varios incidentes de ransomware WantToCry. En todos los casos, los atacantes utilizaron máquinas virtuales con nombres de host NetBIOS autogenerados derivados de plantillas de Windows proporcionadas por ISPsystem, un proveedor legítimo de plataformas de gestión de infraestructura de TI. Los investigadores de Counter Threat Unit™ (CTU) investigaron la posible magnitud del uso malicioso de estos dispositivos e identificaron múltiples sistemas expuestos a Internet asociados con actividades ciberdelictivas, incluidas operaciones de ransomware y distribución de malware común. Investigaciones posteriores identificaron múltiples nombres de host adicionales derivados de plantillas de máquinas virtuales proporcionadas por ISPsystem, algunos de los cuales también se utilizaron en actividades maliciosas.
Según las observaciones de CTU™ y de terceros, los dos nombres de host utilizados en la actividad del ransomware WantToCry (WIN-J9D866ESIJ2 y WIN-LIVFRVQFMKO) se han utilizado en múltiples incidentes. Esta actividad maliciosa incluye ataques ciberdelictivos con el ransomware LockBit, Qilin y BlackCat (también conocido como ALPHV), y una implementación adicional de NetSupport RAT. A finales de 2021, un usuario llamado «Bentley» (posteriormente identificado como Maksim Galochkin y sancionado por los gobiernos de Estados Unidos y Reino Unido) utilizó un dispositivo con el nombre de host WIN-LIVFRVQFMKO para iniciar sesión en un chat privado de Jabber en el que participaban miembros de GOLD ULRICK, que opera el ransomware Conti, y GOLD BLACKBURN, que opera TrickBot. Estos registros de chat fueron revelados por un supuesto infiltrado en la operación «ContiLeaks» de febrero de 2022. En julio de 2023, un dispositivo con el mismo nombre de host fue utilizado en una campaña de Ursnif dirigida a organizaciones en Italia y en diciembre de 2024, Kaspersky informó sobre su uso en la explotación de una vulnerabilidad de FortiClient EMS.
Sería tentador concluir que cada nombre de host es utilizado por un único actor malicioso que se dedica a una serie de actividades delictivas. Sin embargo, según el motor de búsqueda Shodan, los dos nombres de host estaban asociados a miles de dispositivos conectados a Internet que exponían servicios RDP (puerto TCP 3389) en diciembre de 2025. A fecha de 19 de diciembre, había 3645 hosts activos que exponían el nombre de host WIN-J9D866ESIJ2 y 7937 con el nombre de host WIN-LIVFRVQFMKO. La mayoría de los dispositivos que utilizaban estos nombres de host se encontraban en Rusia y algunos en otros países de la Comunidad de Estados Independientes (CEI), Europa y Estados Unidos (véase la figura 1). Algunos dispositivos con el nombre de host WIN-LIVFRVQFMKO se encontraban en Irán.
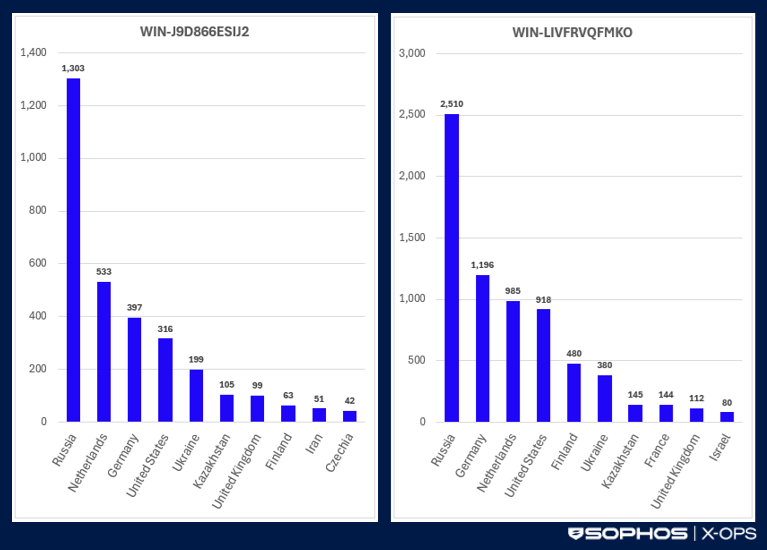
Figura 1: ubicaciones de los dispositivos que utilizan estos nombres de host según la dirección IP asociada
Varios proveedores de alojamiento estaban asociados a estos nombres de host, pero los más frecuentes eran Stark Industries Solutions Ltd, Zomro B.V., First Server Limited, Partner Hosting LTD y JSC IOT (véanse las tablas 1 y 2).
| Proveedores de alojamiento WIN-J9D866ESIJ2 | Número de hosts |
| First Server Limited | 592 |
| Stark Industries Solutions Ltd | 576 |
| Zomro B.V. | 308 |
| Global Connectivity Solutions LLP | 189 |
| Kontel LLC | 148 |
Tabla 1: los 5 principales proveedores que alojan máquinas virtuales WIN-J9D866ESIJ2
| Proveedores de alojamiento WIN-LIVFRVQFMKO | Número de hosts |
| Stark Industries Solutions Ltd | 634 |
| Zomro B.V. | 455 |
| First Server Limited | 414 |
| Partner Hosting LTD | 356 |
| JSC IOT | 355 |
Tabla 2: los 5 principales proveedores que alojan máquinas virtuales WIN-LIVFRVQFMKO
Aunque es probable que haya alguna actividad legítima que se origine en máquinas virtuales con estos nombres de host de estos proveedores de alojamiento, hay datos adicionales que vinculan a los dos principales proveedores (Stark Industries Solutions Ltd y First Server Limited) con operaciones ciberdelictivas y patrocinadas por el Estado ruso. Los investigadores de la CTU y de terceros han observado que múltiples grupos de amenazas patrocinados por el Estado y ciberdelincuentes utilizan la infraestructura de Stark Industries Solutions Ltd desde su fundación en febrero de 2022, justo antes de la invasión de Ucrania por parte de Rusia. En mayo de 2025, el Consejo Europeo emitió «medidas restrictivas» contra Stark Industries Solutions Ltd y sus operadores por permitir que «varios actores patrocinados y afiliados al Estado ruso llevaran a cabo actividades desestabilizadoras».
Mientras tanto, investigaciones de terceros sugieren que First Server Limited está estrechamente relacionada con Doppelganger, una campaña de desinformación rusa cuyos operadores y entidades asociadas fueron sancionados por el Gobierno del Reino Unido en octubre de 2024. La concentración de estos nombres de host entre un número relativamente pequeño de proveedores de alojamiento y regiones geográficas parece coincidir con el despliegue a gran escala de plantillas de máquinas virtuales preconfiguradas, en lugar de la construcción de infraestructuras independientes por parte de actores maliciosos individuales.
Una investigación más detallada reveló que estos nombres de host proceden de imágenes de Windows Server ampliamente reutilizadas y distribuidas a través del panel de control de la plataforma legítima de gestión de virtualización ISPsystem VMmanager. Los investigadores de la CTU plantearon la hipótesis de que el despliegue de una imagen asignaría el mismo nombre de host y el mismo sujeto de certificado autofirmado, lo que podría crear la apariencia de una infraestructura compartida entre actores maliciosos que, por lo demás, no estarían relacionados entre sí. Para validar esta hipótesis, los investigadores de la CTU adquirieron un servidor virtual de play2go.cloud, un proveedor de alojamiento que utiliza ISPsystem VMmanager, e implementaron una máquina virtual Windows en condiciones estándar para los clientes. El sistema resultante generó automáticamente el nombre de host WIN-J9D866ESIJ2, en consonancia con el patrón observado en la infraestructura expuesta a Internet.
Los investigadores de la CTU implementaron de forma independiente un entorno de prueba controlado utilizando una instalación de prueba de VMmanager, lo que permitió la implementación directa de máquinas virtuales Windows. Los sistemas aprovisionados a partir de las plantillas predeterminadas de Windows de VMmanager generaron de forma sistemática los mismos nombres de host estáticos. Esta prueba llevó a los investigadores de la CTU a identificar y analizar un repositorio de acceso público de imágenes de sistemas operativos preconstruidas utilizadas por VMmanager para la implementación de máquinas virtuales basadas en plantillas.
Este repositorio incluye múltiples plantillas de Windows Server que abarcan desde Windows Server 2012 R2 hasta Windows Server 2025, así como variantes de escritorio de Windows 10 y Windows 11. El análisis de estas imágenes y sus scripts de implementación asociados confirmó que el nombre de host y los identificadores de sistema relacionados están incrustados en cada plantilla y no se aleatorizan durante el aprovisionamiento. Los investigadores de CTU utilizaron Shodan para analizar la prevalencia de estos nombres de host en Internet (véase la tabla 3).
| Hostname | OS version | Total hosts | Top country | Top hosting provider |
| WIN-LIVFRVQFMKO | Windows Server 2019 (KMS) | 7937 | Rusia | Stark Industries Solutions Ltd |
| WIN-BS656MOF35Q | Windows Server 2022 (KMS) | 7825 | Alemania | Stark Industries Solutions Ltd |
| WIN-344VU98D3RU | Windows Server 2012 R2 | 7437 | Países Bajos | Zomro B.V. |
| WIN-J9D866ESIJ2 | Windows Server 2016 | 3645 | Rusia | First Server Limited |
| WIN-9C3K8L5M5Q7 | Windows Server 2022 (GPT) | 541 | Rusia | Stark Industries Solutions Ltd |
| DESKTOP-7VBH2AA | Windows 11 (Dec 2025) | 177 | EE. UU. | Stark Industries Solutions Ltd |
| WIN-E9VUEDVSAHR | Windows Server 2019 (Russian GPT) | 170 | Rusia | JSC IOT |
| WIN-3R1Q4OEL7SH | Windows Server 2019 Datacenter | 152 | Rusia | Stark Industries Solutions Ltd |
| WIN-EGR0637MAEG | Windows Server 2019 (GPT) | 100 | EE. UU. | Stark Industries Solutions Ltd |
| WIN-5BIER8OOA6N | Windows Server 2025 | 66 | Chequia | SmartApe OU |
| WIN-67KRP38M7IH | Windows Server Core 2019 | 4 | Países Bajos | Stark Industries Solutions Ltd |
| WIN-98FDM29KPEE | Windows 10 | 0 | N/A | N/A |
| WIN-QLUI838SCU0 | Windows 10 (Ruso) | 0 | N/A | N/A |
| WIN-P7Q737OF0AM | Windows 11 (Agosto 2024) | 0 | N/A | N/A |
Tabla 3: nombres de host de máquinas virtuales ISPsystem y su prevalencia en Internet a 19 de diciembre de 2025
Los cuatro nombres de host más prevalentes representan más del 95 % del número total de máquinas virtuales ISPsystem conectadas a Internet. No es de extrañar que las dos imágenes más populares (WIN-LIVFRVQFMKO y WIN-BS656MOF35Q) sean variantes habilitadas para el Servicio de administración de claves (KMS), lo que permite que el sistema operativo Windows funcione de forma gratuita durante un período de gracia de 180 días sin necesidad de licencias individuales.
Los investigadores de la CTU investigaron todos los nombres de host en busca de pruebas de actividad maliciosa. El análisis reveló que estos cuatro nombres de host más frecuentes, que incluyen los dos observados por los analistas de SophosLabs en los ataques WantToCry, se utilizaron en actividades ciberdelictivas (véase la tabla 4). Todos ellos se observaron en los datos de detección de clientes de Sophos o en la telemetría de alguna forma.
| Nombres de host | Versión del sistema operativo | Actividad maliciosa observada |
| WIN-LIVFRVQFMKO | Windows Server 2019 | LockBit Conti Qilin WantToCry BlackCat (ALPHV) Registros de chat de Conti (referenciados por «Bentley» en Jabber) Explotación de la vulnerabilidad de FortiClient EMS Ursnif |
| WIN-BS656MOF35Q | Windows Server 2022 | Campañas de ClickFix, PureRAT y Lumma stealer Campañas de Cerberus Team malware |
| WIN-344VU98D3RU | Windows Server 2012 R2 | RedLine infostealer Lampion infostealer |
| WIN-J9D866ESIJ2 | Windows Server 2016 | WantToCry NetSupport RAT |
Tabla 4: nombres de host y conexiones a actividades maliciosas
Los investigadores de la CTU buscaron estos nombres de host en foros clandestinos y plataformas de comunicación como Telegram y descubrieron anuncios de proveedores de alojamiento a prueba de balas (BPH). Los operadores de los servicios BPH permiten a sabiendas el alojamiento de contenido ilícito, al tiempo que mantienen una infraestructura en la que los actores maliciosos pueden confiar para seguir operando ante las denuncias de abuso, las solicitudes de retirada y las medidas policiales.
La infraestructura suele dar soporte a servidores de comando y control (C2) de ransomware, distribución de malware, campañas de phishing, gestión de botnets y preparación de la exfiltración de datos.
Los investigadores de CTU identificaron numerosas referencias a un proveedor llamado MasterRDP en conjuntos de datos asociados a sistemas que exponían nombres de host derivados de ISPsystem. Las publicaciones en foros clandestinos y la actividad pública en Telegram anuncian BPH, acceso a servidores privados virtuales (VPS) y servicios RDP bajo esta marca.
Es muy probable que MasterRDP sea uno de los muchos proveedores de BPH dentro del ecosistema ciberdelictivo que alquilan máquinas virtuales de ISPsystem alojadas en una infraestructura tolerante al abuso a clientes con intenciones maliciosas, incluidos los que se dedican a operaciones de ransomware y distribución de malware. ISPsystem VMmanager es una plataforma de gestión de virtualización comercial legítima muy utilizada en el sector del alojamiento web, y el software en sí no es malicioso. Sin embargo, su bajo coste, su fácil acceso y sus capacidades de implementación llave en mano lo hacen atractivo para los ciberdelincuentes, mientras que su uso legítimo generalizado proporciona cobertura operativa entre miles de implementaciones que cumplen con la normativa.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


