Sophos 在 2024 MITRE ATT&CK® Evaluations 中表现超卓:Enterprise
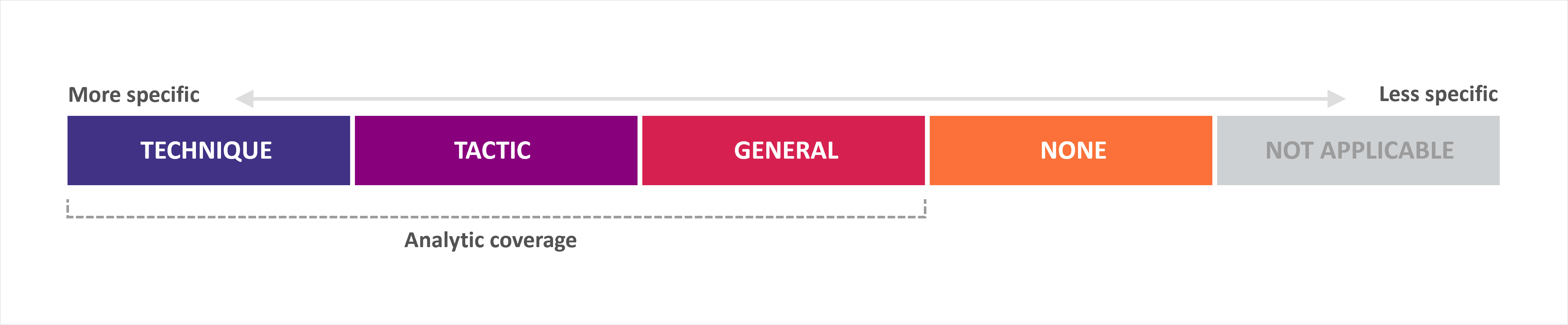
MITRE ATT&CK® Evaluations评估帮助组织更好地了解 EDR 和 XDR 解决方案在防御复杂的多阶段攻击中的有效性。在最新的评估中,Sophos XDR 取得了以下佳绩:
- 在 Windows 和 Linux 勒索软件攻击场景中, 100% 的敌手活动获得了最高(‘Technique’ (技术))评级
- 在所有三个综合场景中, 80 项敌手活动中有 78 项 获得了最高(‘Technique’ (技术))评级
2024 MITRE ATT&CK® Evaluations:Enterprise(第 6 轮)
MITRE ATT&CK® Evaluations 是全球最受推崇的独立安全测试之一。这些评估模拟现实中敌手团体使用的战术、技术和程序 (TTP),并评估参与厂商在侦测、分析和描述威胁方面的能力,评估结果与 MITRE ATT&CK® Framework 框架 的用词和结构相一致。
第 6 轮评估聚焦于受三大已知威胁团体所启发的行为:
- 朝鲜民主主义人民共和国(朝鲜)
评估模拟了朝鲜通过多阶段操作针对 macOS 的行为,包括提升特权和窃取凭证。
- 勒索软件(CL0P 和 LockBit)
评估模拟了使用 CL0P 和 LockBit 勒索软件攻击中常见的行为,包括滥用合法工具和停用关键服务。
评估结果
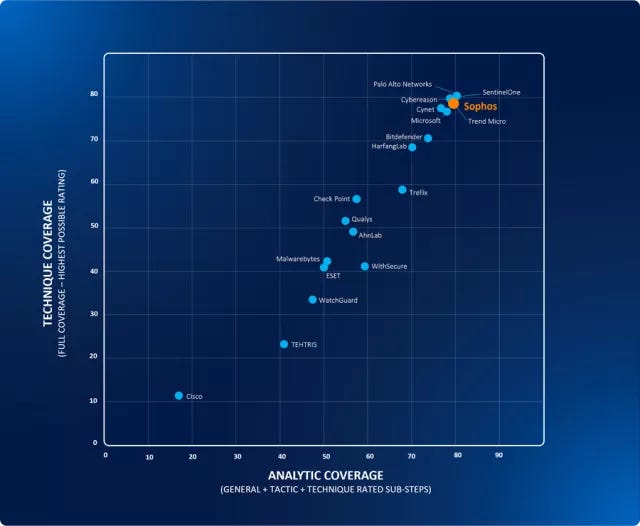
Sophos 在三个综合的攻击场景中,在 80 项敌手活动(子步骤)中的 78 项均达到了完整 ‘technique’ (技术) 等级覆盖——最高 的评级。


评估攻击场景
本次评估包括三个攻击场景,共计 80 个敌手活动(子步骤)。
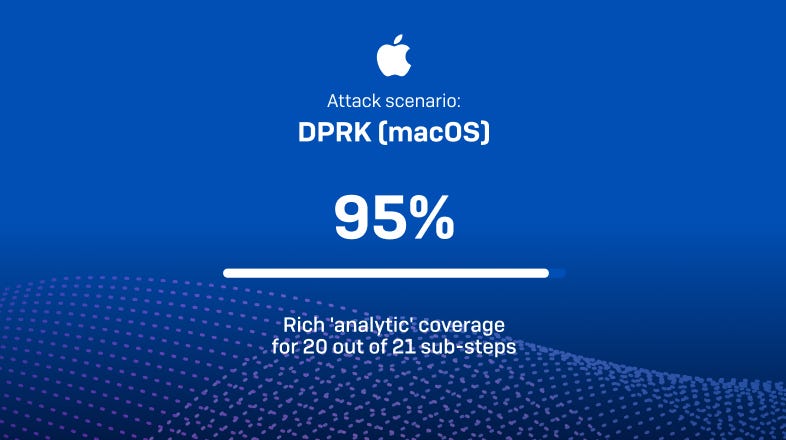
攻击场景 1:朝鲜 (macOS)
朝鲜已成为全球的强大网络威胁,通过将攻击目标扩展到 macOS,能够渗透更多高价值的系统。在该攻击场景中,MITRE 团队使用来自供应链攻击的后门,随后进行持久化、发现和凭据访问,最终收集并泄露系统信息和 macOS 钥匙串文件。
- 4 个步骤 | 21 个子步骤 | 仅限 macOS
- Sophos XDR 在该场景中成功侦测并提供了 20 个子步骤(在 21 个中)的丰富 ’analytic’ 覆盖(占比 95%)
- 其中 19 个子步骤获得了 ‘Technique’ 级别分类 —— 最高评级
攻击场景 2:CL0P 勒索软件 (Windows)
CL0P自 2019 年起活跃的勒索软件家族,隶属于 TA505 网络犯罪集团(又名 Snakefly),普遍认为由俄语系团体操控。在该攻击场景中,MITRE 团队使用了规避技术、持久性手段以及内存中的有效负载,进行发现和渗透,最后实施勒索软件攻击。
- 4 个步骤 | 19 个子步骤 | 仅限 Windows
- Sophos XDR 成功侦测并对 100% 的子步骤提供了完整 ‘Technique’ 级别的覆盖
攻击场景 3:LockBit 勒索软件
(Windows 和 Linux)
LockBit 是一种臭名昭著的勒索软件变种,采用勒索软件即服务 (RaaS) 模式运营,以其复杂的工具、勒索方式及高强度的攻击而闻名。在该攻击场景中,MITRE 团队通过窃取的凭证获得访问权限,接着部署渗透工具和勒索软件,来停止虚拟机并执行文件渗透和加密。
- 8 个步骤 | 40 个子步骤 | Windows 和 Linux
- Sophos XDR 成功侦测并对 100% 的子步骤提供了完整 ‘Technique’ 级别的覆盖
- Sophos XDR 为评估中的所有 80 个敌手活动(子步骤)生成了警报,并在 80 个子步骤中获得了 79 个 ‘analytic coverage’ 评级。
然而,在朝鲜 (macOS) 攻击场景中的一个子步骤中所生成的警报未达到 MITRE 侦测类别定义中的 ‘analytic coverage’ 侦测标准。
为什么我们参与 MITRE ATT&CK® Evaluations
MITRE ATT&CK® Evaluations 是全球最受推崇的独立安全测试之一。Sophos 致力于与业内最优秀的安全厂商一同参与这些评估。作为一个共同体,我们齐心协力,共同应对网络威胁。这些评估不仅帮助我们精益求精,不论个别和整体地,也为了确保我们所保护的组织的利益。
这次评估共有 19 家 EDR/XDR 安全厂商参与:

其他 MITRE ATT&CK® Evaluations
Sophos 积极参与针对企业解决方案和托管服务的 ATT&CK® Evaluations,始终取得骄人成绩,验证了我们在网络安全厂商的领导地位。

.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)