
Zero Trust Network Access
Securely connect your users to your applications.
The perfect addition to your Sophos Firewall, Endpoint, XDR, and MDR solutions.

Forget about old-school VPN — there’s a better way
Zero Trust Network Access is simpler and more secure than VPN
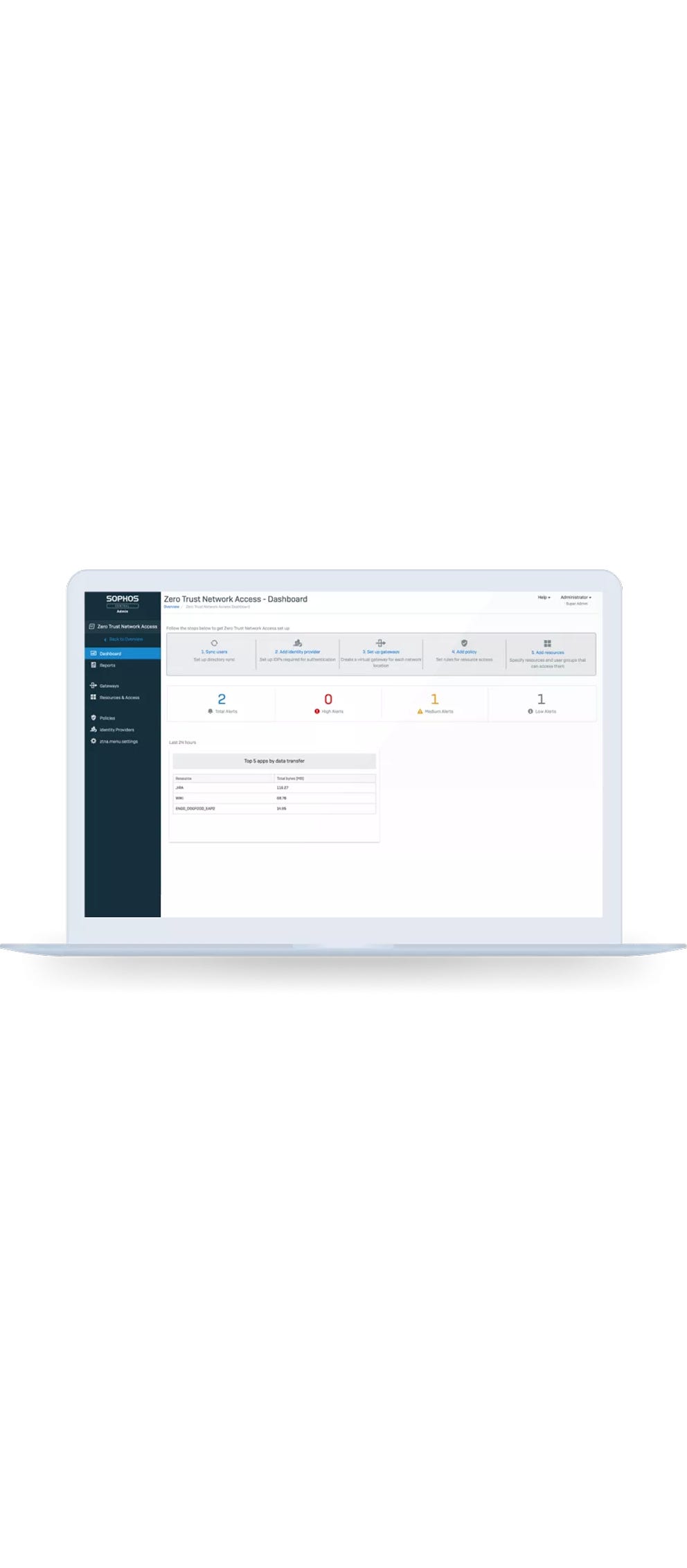
Sophos ZTNA, part of the Sophos Workspace Protection bundle, provides a transparent way to securely connect users to just the applications they need, removing implicit trust, and protecting your applications from unauthorized access, breaches, and attacks. It makes your applications invisible to the outside world, while enabling easy and secure access for your remote or hybrid workers.

Improve your security posture
ZTNA greatly reduces your attack surface, eliminating implicit trust, providing access to only those apps a specific user needs, while adding device posture to access policy to block compromised devices from connecting.

Enable remote and hybrid workers
Replace your legacy remote access VPN with new least-privileged access to your valued business applications, systems, and data, improving your security and making it easier to manage at the same time.

Transparent and easy access
Sophos ZTNA is seamlessly integrated into Sophos Protected Browser with a rich RDP and SSH client providing transparent and easy access to all your important applications and systems.

Top Six Advantages of ZTNA
Cloud-Delivered and Cloud-Managed
Begin your SASE journey with Sophos ZTNA – Our first of many Security Service Edge (SSE) solutions.
ZTNA-as-a-Service
Sophos has been a leader in leveraging the cloud to deliver innovative cybersecurity solutions, and we continue to do as we transition into the future. Sophos ZTNA is the first of many SSE solutions to come, providing security services hosted in the cloud to meet the needs of a modern distributed workforce.
Managed by Us or Managed by You
Sophos is unique in providing the ultimate cloud-based management solution for all your cybersecurity requirements with Sophos Central, as well as giving you the choice to have us manage it for you with our fully managed 24/7 threat hunting, detection, and response service.
Pragmatic SASE for Everyone
Like you, we’re adopting a practical approach to cloud-hosted security services. We are implementing SASE services in a manner that will immediately add value to your hybrid networks, resolving your key issues with a distributed workforce and limited resources, all while operating in an exceptionally hostile threat landscape. At Sophos, integration, simplicity, and value are part of our DNA, so you won’t be surprised that they are part of our SASE strategy as well.

Sophos ZTNA: Single Agent, Single Console, Single Vendor
Sophos ZTNA is the only zero trust network access solution that is tightly integrated with next-generation endpoint, XDR, and MDR.
Unified Endpoint Security: ZTNA, Endpoint, XDR, and MDR
With Sophos ZTNA, you can secure your application access and protect your endpoints and networks from ransomware and other advanced threats, while also enabling advanced cross-product detection and response. You receive holistic end-to-end protection, detection, and response that's effective and easy to use.
Single Agent
Sophos is unique in delivering an innovative integrated single agent solution for both endpoint and ZTNA – that deploys with just a single click. You might not even need an agent, since some web browser-based apps don't require one.
Single Console and Single Supplier
Sophos ZTNA is a component of the world's most trusted cybersecurity ecosystem, managed from a single cloud console – Sophos Central. You deploy, manage, and report on your entire cybersecurity estate from a single pane of glass. No other vendor offers this kind of integration and simplicity.
Automated threat response
Sophos ZTNA takes full advantage of our unique Synchronized Security and Active Threat Response capability by sharing health information between Sophos products to automatically limit compromised devices from accessing networked applications. If a user’s device becomes compromised, it won’t be able to spread beyond that device.

Synchronized Security
Shares device health between Sophos products such as Sophos Endpoint, Sophos Firewall, ZTNA, and more, so these products can automatically respond to an active threat on the network.

Active Threat Response
Any device identified as having an active threat is automatically isolated and contained by other Sophos products until it is cleaned up, preventing lateral movement of ransomware and other attacks.

Sophos XDR and MDR integration
Sophos ZTNA integrates with Sophos XDR and MDR and enables security teams to investigate and analyze user and application access activity, such as denied access attempts and more.
Sophos Protected Browser — Part of Workspace Protection
Sophos Workspace Protection makes protecting your apps, data, and remote and hybrid workers easy and affordable. It includes everything you need to provide transparent secure access for those who need it — everywhere they go — while protecting it from those who don’t.
Cybersecurity for all your needs
Sophos Managed Detection and Response
For organizations that are looking to augment their security operations capabilities, Sophos Managed Detection and Response (MDR) reduces risk, simplifies security, maximizes your tech investments, and strengthens your defenses.
- A global team of cybersecurity experts monitors your environment 24/7.
- Industry-leading threat researchers constantly discover new threat groups and attack techniques.
- Proactive threat hunting to find stealthy threats that elude detection by security tools.
- Full-scale incident response to fully eliminate adversaries. No caps or extra fees.
- Choose from a range of service tiers and threat response modes to meet your needs.
Sophos Endpoint
Included and natively integrated with Taegis XDR. Sophos Endpoint delivers a comprehensive defense-in-depth approach to stop the broadest range of threats before they impact your systems.
- Prevention first approach to block more threats upfront to minimize risk and reduce investigation and response workloads.
- Adaptive defenses that stop active adversaries with dynamic protection that automatically adapts as an attack evolves.
- Detection and response to neutralize sophisticated multi-stage attacks that can’t be stopped by technology alone.
- Streamlined management interface to focus on the threat, not administration.
Sophos Next-Gen Firewall
Sophos Next-Gen Firewall consolidates your network protection with our integrated and extensible platform to secure your hybrid networked world.
- Expose hidden risks with superior visibility into risky activity, suspicious traffic, and advanced threats.
- Stop unknown threats with protection technologies like deep learning and intrusion prevention that help keep your organization secure.
- Automatic threat response instantly identifies and isolates compromised systems to stop threats from spreading.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)




