
The Ultimate Security Package
Proven protection for your network – simpler, faster, better.
Deep Learning Protection
Sophos UTM drives threat prevention to unmatched levels. The artificial intelligence built into Sophos Sandstorm is a deep learning neural network, an advanced form of machine learning, that detects both known and unknown malware without relying on signatures.
Sophos UTM 9.4 is one of the first Sophos products to offer our advanced next-gen cloud sandboxing technology.
Sandstorm provides a whole new level of ransomware and targeted attack protection, visibility, and analysis. It can quickly and accurately identify evasive threats before they enter your network. Sandstorm is:
And, it’s tremendous value: it’s enterprise-grade protection without the enterprise-grade price-tag or complexity.
Sophos UTM 9.4 is one of the first Sophos products to offer our advanced next-gen cloud sandboxing technology.
Sandstorm provides a whole new level of ransomware and targeted attack protection, visibility, and analysis. It can quickly and accurately identify evasive threats before they enter your network. Sandstorm is:
- Easy to try, deploy, and manage
- Effective at blocking evasive threats
- Simple and powerful cloud-based protection
And, it’s tremendous value: it’s enterprise-grade protection without the enterprise-grade price-tag or complexity.
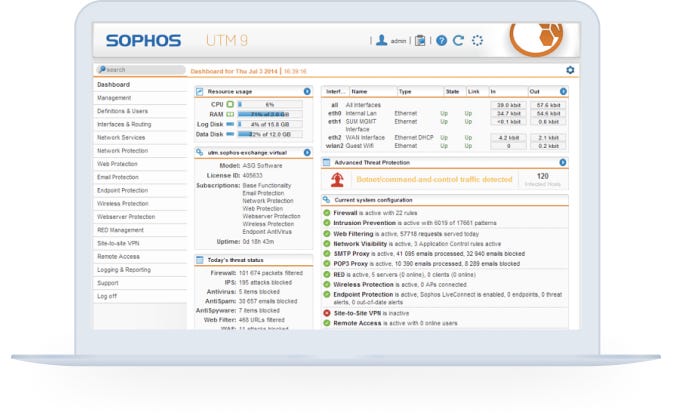
We keep it simple
Sophos UTM's simple, intuitive user interface (UI) is designed for you. It lets you quickly protect your network and users. And it makes day-to-day management tasks easy.
All-in-One Protection
We offer the latest next-gen firewall protection you need, plus features you can't get anywhere else – including mobile, web, endpoint email encryption, and DLP.
No extra hardware. No extra cost. Simply choose what you want to deploy.
Logging & Reporting
Our built-in reporting means you'll know exactly what's happening with your users. Fix problems fast and shape your policies, keeping your users secure while boosting network performance. And, you get detailed reports as standard, stored locally with no separate tools required.
Need More Reporting?
Although you can have all your logging and reporting built in to your box, sometimes you may need a little more. For that, you can add Sophos iView.
- At-a-glance flow graphs show usage trends and web activity
- Our daily summary executive report keeps you informed
- Report anonymization can hide user names where needed
- Built-in Syslog support and automated log backup options
Need More Reporting?
Although you can have all your logging and reporting built in to your box, sometimes you may need a little more. For that, you can add Sophos iView.

.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)








.png?width=61&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)



