Today Sophos notified partners and customers that a limited number of Sophos Central user passwords were captured in Central logs. This was caused by a change we made to the Central login experience on January 20, 2022, and lasted until identified by Sophos employees on February 5, 2022. We’ve already updated the logic to the login experience to prevent capturing the passwords and the only interaction with the log data was to purge it. Our investigation has determined that there’s been no exposure of these passwords outside of the Sophos logging platform and there is no evidence of misuse. We are sharing this notice with our customers and partners because while there is no exposure, we are recommending a password reset. Sophos believes in transparency as a best security practice, including disclosure about how issues happen, any risks involved, and what, if any, actions customers and partners should take.
What Happened?
On January 20, 2022, the Sophos Central team updated the login experience to support the variety of workflows our customers and partners use, including federated logins. The new Central initial login screen now looks like this:
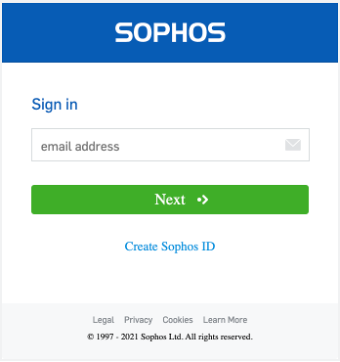
When constructing this screen, the original password field was hidden as the page no longer accepted passwords from users. The password field was not removed as it was part of a template UI provided by our IDP.
When constructing the screen, we leveraged the now unused hidden field to assist with logging of the user-agent value. Unfortunately, the hidden field was still discoverable by password managers. During this period, some password managers auto-filled the password field even though it was hidden. This resulted in plain text passwords being captured in our logging system for these customers.
This scenario only existed for users using password managers set to auto-populate passwords. No passwords were logged for admins who followed the normal manual workflow to enter passwords on subsequent pages, or for federated admins.
Because multi-factor authentication (MFA) is compulsory to log into Sophos Central, passwords alone are not sufficient to create an authenticated session. Sophos has required MFA for all multi-tenant environments for several years and required all single-tenant accounts to enroll in MFA as of September 2021.
How was this identified?
On February 5, 2022, Sophos employees were doing a routine review of log files for unrelated purposes and identified passwords captured in the files. All access to these files is governed by Sophos Active Directory groups and protected by multi-factor authentication, so only a small number of Sophos employees had access. The issue was immediately escalated to Central Engineering leadership and was remediated within the same day.
As part of the remediation, all relevant data was purged from both primary log files as well as backup. This purge was the extent of our handling of the data. The purge was also verified by the Sophos Security Operations Team.
What’s Next?
We have identified all the customers and partners affected by this. As a security best practice, we’ve asked affected customers and partners to refresh their password. We apologize for the inconvenience, but it’s the right way to take the risk to zero.
We’re also updating our test matrix for the login experience. Previous versions of the login experience were indifferent to manual or automated entry of credentials, so we’re also updating our test matrix for the login experience to account for these new scenarios.
If you ever have concerns about any activity on your Sophos account(s), whether it is connected to this issue or unrelated, please visit the Sophos Trust Center.