
Was ist Threat Hunting?
Ein proaktiver Ansatz ist entscheidend, wenn Unternehmen sich effektiv vor Cyberangriffen schützen wollen. Moderne Bedrohungsakteure gehen immer raffinierter vor und nutzen zunehmend evasive, von Spezialisten gesteuerte Techniken für ihre Angriffe. Aus diesem Grund ist Threat Hunting für den Schutz von Unternehmen unerlässlich geworden. Wenn Unternehmen und Organisationen Bedrohungen proaktiv aufspüren und beseitigen, bevor Schaden entsteht, können sie sich besser vor aktiven Angreifern schützen.
Was ist Threat Hunting?
Threat Hunting ist eine Form der Cybersicherheit, bei der Sicherheitsexperten proaktiv Netzwerke, Systeme, Anwendungen oder angeschlossene Geräte auf Anzeichen für potenziell bösartige Aktivitäten eines aktiven Angreifers untersuchen. Beim Threat Hunting kommt in der Regel eine Kombination aus manuellen und automatisierten Sicherheitsmaßnahmen zum Einsatz. Beispiele hierfür sind etwa die Analyse von Protokolldaten auf Anomalien, die Durchführung von Netzwerk-Scans oder die Nutzung von Intelligence Feeds. Beim Threat Hunting geht es insbesondere darum, potenziell bösartiges Verhalten, das durch andere Sicherheitsmechanismen möglicherweise nicht erfasst wird, schnell zu erkennen und zu lokalisieren.
In vielerlei Hinsicht ähneln Threat Hunts einer richtigen Jagd. Anstatt darauf zu warten, dass sich ein Ziel nähert, begeben sich Threat Hunter auf die Suche nach potenziellen Bedrohungsakteuren und bösartigen Aktivitäten. Diese hochqualifizierten Sicherheitsexperten arbeiten oft für einen Managed Security Service Provider (MSSP) oder ein internes Security Operations Center (SOC).
Warum ist Threat Hunting so wichtig?
Fast ein Viertel (23 %) der an unserer unabhängigen Befragung von 3.000 IT-Experten aus 14 Ländern teilnehmenden Unternehmen waren im vergangenen Jahr Opfer eines aktiven Angriffs[1] – schlichtweg besorgniserregende Zahlen.
Diese Angriffe lassen sich nur schwer erkennen, da aktive Angreifer ihre Techniken, Taktiken und Prozesse (TTPs) in Echtzeit an Abwehrmaßnahmen von Sicherheitstechnologien und Bedrohungsexperten anpassen, um unerkannt zu bleiben.
Technologie allein reicht nicht mehr aus, um Bedrohungen zu 100 % zu stoppen. Threat Hunts sind daher unerlässlich, um Bedrohungen, die mit herkömmlichen Methoden nicht nachweisbar sind, aufzuspüren und zu beseitigen.
[1] Ransomware-Report 2023 – Sophos
Was ist der Unterschied zwischen Managed Detection and Response (MDR) und Threat Hunting?
Threat Hunting und Managed Detection and Response (MDR) lassen sich leicht verwechseln. Der Hauptunterschied besteht darin, dass Threat Hunting häufig Teil einer MDR-Strategie ist.
MDR ist breiter angelegt. Es handelt sich dabei um einen vollständig ausgelagerten, ganzheitlichen Cybersecurity-Ansatz, der kontinuierliches Monitoring von Endpoints, Netzwerken, Cloud-Security sowie Benutzeridentitäten eines Unternehmens auf bekannte Bedrohungen und Anomalien umfasst.
MDR-Services nutzen Sicherheitssoftware, die automatisierte Sicherheitswarnungen und -informationen an Sicherheitsexperten weiterleitet. Diese Warnmeldungen beziehen sich auf bekannte Schwachstellen. Anhand einer spezifischen Logik sowie Kriterien, die vom Sicherheitsexperten festgelegt werden, werden hierbei erkannte Bedrohungen eskaliert.
Threat Hunting kann dagegen entweder (an einen MDR-Anbieter oder MSSP) ausgelagert oder intern vom SOC eines Unternehmens durchgeführt werden.
Bei Threat Hunts suchen Sicherheitsexperten aktiv nach Bedrohungen in Systemen, anstatt passiv auf Software-Warnmeldungen zu warten. MDR konzentriert sich auf die Überwachung bekannter Bedrohungen mit Hilfe von Software und Automatisierung. Bei Threat Hunting handelt es sich dagegen um eine Kombination aus Tools und von Experten gesteuerten Maßnahmen. Threat Hunter sind hochqualifizierte Sicherheitsexperten. Sie wissen nicht unbedingt immer genau, wonach sie suchen, da ihre Threat Hunts auf bekannten oder unbekannten Schwachstellen, bekannten oder unbekannten verdächtigen Verhaltensweisen oder Indizien beruhen.
Bei einem guten MDR-Service ist Threat Hunting eine zentrale Komponente der Bedrohungserkennung und -reaktion. Bei Sophos MDR suchen unsere Sicherheitsanalysten proaktiv nach Bedrohungen, die Sicherheitslösungen umgehen. Anschließend analysieren sie deren Schweregrad und ergreifen entsprechende Maßnahmen.
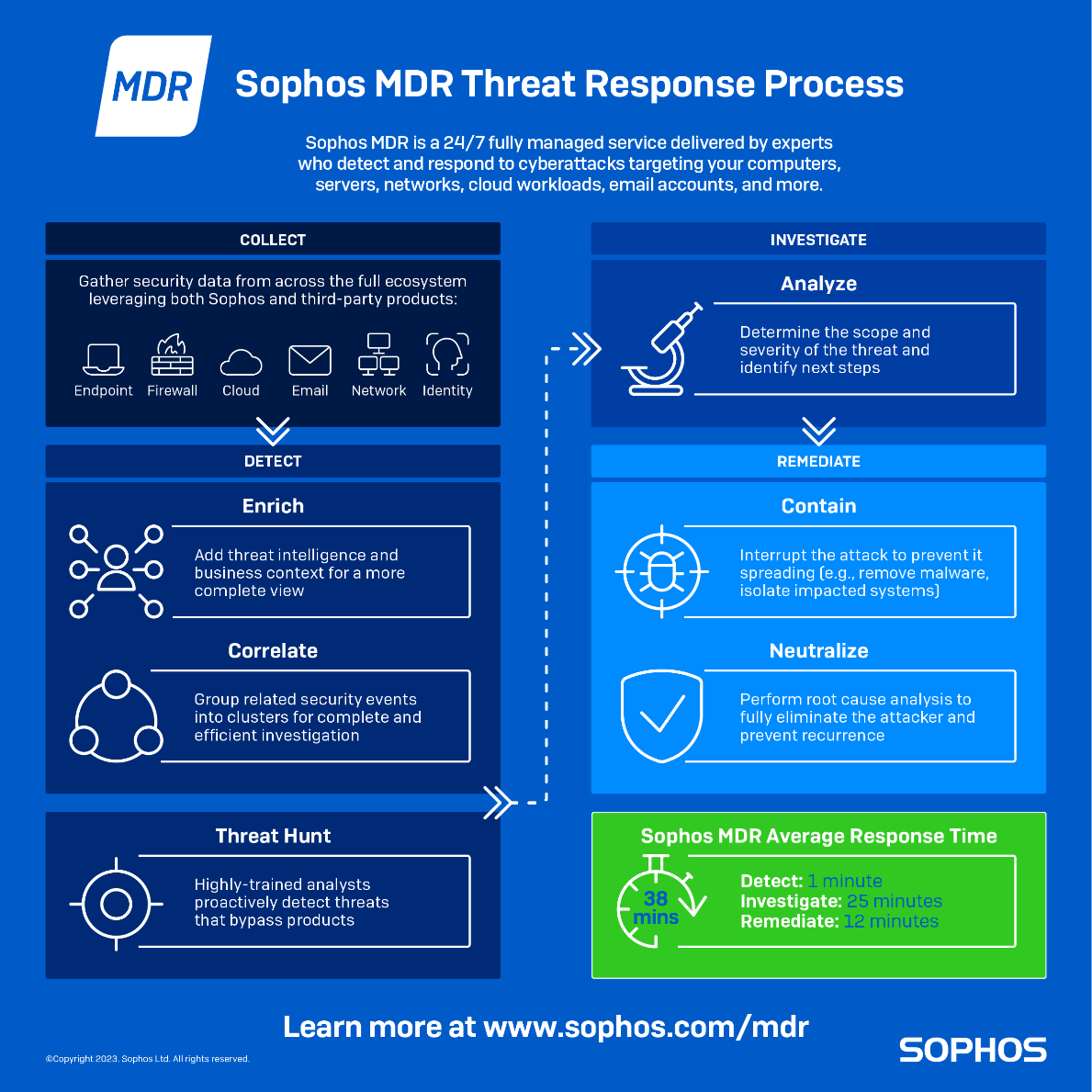
Wie funktioniert Threat Hunting?
Erfahrene Threat Hunter gehen davon aus, dass eine potenzielle Bedrohung die Cyberabwehr eines Unternehmens bereits umgangen hat und versucht, in die Systeme einzudringen. Schlussendlich geht es beim Threat Hunting darum, die Verweildauer eines Angreifers im System zu begrenzen. Indem sie die Bedrohung schneller erkennen, minimieren Threat Hunter den potenziellen Schaden von Angriffen und stoppen diese, bevor sie sich ausbreiten können.
In den meisten Fällen konzentrieren sich Threat Hunter auf zwei Bedrohungskategorien:
- Indizienbasierte Threat Hunts: Bei diesen Threat Hunts hat das Verhalten des Angreifers eine Warnmeldung in einem oder mehreren Abwehrmechanismen ausgelöst.
- Indizienlose Threat Hunts: Eine proaktivere Form der Bedrohungssuche, bei der noch keine Warnungen ausgelöst wurden. Diese Form des Threat Huntings kommt insbesondere bei unbekannten oder Zero-Day-Bedrohungen zum Einsatz.
In der Regel ist der Arbeitsaufwand von Threat Huntern bei indizienlosen Threat Hunts nach unbekannten Bedrohungen am größten. Gleichzeitig können diese sich als besonders gefährlich erweisen. Sowohl bei indizienbasierten als auch bei indizienlosen Threat Hunts priorisiert das Sicherheitsteam sämtliche erkannten Bedrohungen, ergreift Reaktionsmaßnahmen und beseitigt die Bedrohungen.
Im Rahmen eines Threat Hunts ermitteln Sicherheitsanalysten die von Bedrohungsakteuren verwendeten Tools, Techniken und Prozesse (TTPs), um die potenzielle Angriffsphase zu bestimmen und ihr Wissen über die Bedrohung zu erweitern. Sobald ihnen diese Erkenntnisse vorliegen, ergreifen sie geeignete Maßnahmen, um die Bedrohung zu beseitigen.
Eine Threat-Hunting-Strategie umfasst fünf Kernkomponenten:
- Prävention. Durch den Einsatz robuster und exakt konfigurierter Abwehrtechnologien (z. B. einer Endpoint-Security-Lösung) können die meisten Angreifer gar nicht erst in Ihr Unternehmensnetzwerk gelangen. Präventions-Tools können die Anzahl der Warnmeldungen reduzieren, die täglich oder sogar stündlich generiert werden. Da weniger Warnmeldungen gesichtet werden müssen, können Threat Hunter besser die Signale erkennen, die die größte Bedrohung darstellen und sich darauf konzentrieren, d. h. evasive, aktiv agierende Angreifer.
- Datenerfassung. Für erfolgreiches Threat Hunting müssen Sicherheitsanalysten auf umfangreiche Sicherheitsdaten aus Ihrer Umgebung zugreifen können. Hierzu benötigen Unternehmen Threat-Monitoring- und Sicherheitssysteme, die kontinuierlich Daten über die Umgebung erfassen. Die Datenerfassung liefert den Threat Huntern wertvolle Anhaltspunkte. So können sie eine Baseline festlegen und anschließend normale und verdächtige Verhaltensweisen innerhalb der Umgebung vergleichen und gegenüberstellen. Threat Hunter können potenzielle Angriffsindikatoren nur dann zuverlässig erkennen, wenn ihnen die richtigen Datentypen, das geeignete Datenvolumen und Daten in der erforderlichen Qualität vorliegen. Daten ohne Kontext erschweren Analysten jedoch die Entscheidung, ob von einer Erkennung eine Gefahr ausgeht. Ohne aussagekräftige Metadaten, die mit einem Signal verknüpft sind, kann der Threat Hunter nicht feststellen, ob es sich um schädliche oder harmlose Signale handelt.
- Priorisierung. Threat Hunter entschlüsseln relevante Signale mit Hilfe von kontextgestützten Daten und treffen dann Entscheidungen. Um zu vermeiden, von Daten überflutet zu werden und wichtige Elemente zu übersehen, die genauer analysiert werden sollten, müssen Threat Hunter in der Lage sein, relevante Warnmeldungen herauszufiltern. Die besten Ergebnisse erzielen Sie, wenn Sie relevante Signale von irrelevanten Daten trennen, indem Sie Kontextinformationen, die nur Ereignisverursacher liefern können, mit automatisierter und künstlicher Intelligenz kombinieren. Selbst mit Automatisierung gestaltet sich dieser Vorgang alles andere als einfach.
- Analyse. Sobald ein Threat Hunter die Schlüsselsignale isoliert hat, muss er weitere Erkenntnisse einfließen lassen und die Erkennung mit branchenspezifischen Frameworks und Modellen abgleichen, wie etwa dem MITRE ATT&CK Framework. Ziel ist es , zuverlässig zu ermitteln, ob schädliches oder harmloses Verhalten vorliegt.
- Maßnahme. Stellt ein Threat Hunter fest, dass das Signal auf eine echte Bedrohung hinweist, unternimmt er die beiden folgenden Schritte: Der erste Schritt besteht darin, das unmittelbare Problem zu beseitigen. Im zweiten Schritt muss der Threat Hunter der Ursache auf den Grund gehen, um alle Spuren restlos zu beseitigen. Manchmal reicht es aus, einen Computer zu isolieren oder vom Netzwerk zu trennen. In anderen Fällen muss das Sicherheitsteam tief in die Weiten des Netzwerks eintauchen, um alle Spuren des Angreifers beseitigen zu können und sicherzustellen, dass sich der Angriff nicht wiederholen kann. Nur weil Sie beispielsweise Malware erfolgreich blockiert und von Ihrem System entfernt haben und Ihnen keine Warnmeldung mehr angezeigt wird, bedeutet das noch lange nicht, dass der Angreifer auch vollständig aus Ihrer Umgebung beseitigt wurde.
Professionelle Threat Hunter, die bereits mit Tausenden von Angriffen zu tun hatten, wissen, wann und wo sie genauer hinschauen müssen. Sie suchen nach allen nur erdenklichen Hinweisen, die Angreifer im Netzwerk hinterlassen und ergreifen anschließend entsprechende Gegenmaßnahmen.
Sollte ich Threat Hunting auslagern oder intern verwalten?
Bei Threat Hunts dreht sich alles um das Security Operations Center (SOC) – unabhängig davon, ob die Bedrohungssuche intern selbst verwaltet oder an einen Sicherheitsanbieter ausgelagert wird.
Wenn sich Ihr Unternehmen dafür entscheidet, Threat Hunts selbst zu verwalten, benötigen Sie auf jeden Fall ein eigenes SOC. Ein SOC ist eine zentrale interne Geschäftsfunktion, die sich auf Monitoring, Erkennung, Analyse und Bekämpfung von Cyberbedrohungen konzentriert und gleichzeitig den übergreifenden Sicherheitsstatus Ihrer Organisation optimiert. Bei potenziellen Bedrohungen und allen Fragen zum Thema Cybersicherheit sind die Sicherheitsanalysten in Ihrem SOC Ihre zentrale Anlaufstelle.
Vom Unternehmen selbst verwaltetes Threat Hunting birgt sowohl Vor- als auch Nachteile. Wenn Sie Ihr eigenes Threat Hunting unternehmensintern verwalten, steht Ihrem Unternehmen ein eigenes Team zur Verfügung, das sich voll und ganz auf die lückenlose Sicherheit Ihrer Umgebung konzentriert. In Unternehmen, die bereits über ein SOC verfügen, kann ein Threat-Hunting-Team bestehende Aufgaben und Abläufe erweitern und ergänzen. Ein unternehmensinternes Team kennt die Umgebung Ihres Unternehmens besser als jeder andere. Auf diese Weise werden Bedrohungen häufig schneller erkannt und Reaktionszeiten verkürzt.
Unternehmen ohne internes SOC müssen mehrere Hürden meistern. Eine der größten Herausforderungen bei der Umsetzung unternehmensinterner Threat Hunts besteht darin, Sicherheitsexperten mit der erforderlichen Expertise und Erfahrung zu finden. Auch das richtige Gleichgewicht zwischen den Kompetenzen der Analysten und dem Funktionsumfang der unterstützenden Cybersecurity-Tools zu finden, ist keine leichte Aufgabe.
Unternehmen, die sich für die Auslagerung ihrer Threat Hunts entscheiden, profitieren von einem bestehenden Security Operations Center (SOC). Wenn Sie mit einem Cybersecurity-as-a-Service-Anbieter zusammenarbeiten, steht Ihnen ein größeres Team erfahrener Sicherheitsanalysten zur Verfügung. Die Experten verfügen über umfassende Erfahrung im Umgang mit unterschiedlichsten Angriffen. Sie sind außerdem in der Lage, die bei einem Angriff auf ein Unternehmen gewonnenen Erkenntnisse auf alle anderen Kunden anzuwenden. Ein weiterer Vorteil ist die Skalierbarkeit: Ein ausgelagertes SOC-Team kann größeren Unternehmen mit mehreren Standorten und externen Mitarbeitern rund um die Uhr Unterstützung bieten.
Welche gängigen Cybersecurity-Tools nutzen Threat Hunter?
Transparenz spielt für Threat Hunter eine entscheidende Rolle. Um eine komplexe Cyberbedrohung zu stoppen, bevor größerer Schaden entsteht, müssen Analysten in der Lage sein, Angriffsversuche, unbefugte Netzwerkzugriffe und andere verdächtige Verhaltensweisen in Echtzeit zu erkennen. Dabei können Threat Hunter auch auf Cybersecurity-Technologie zurückgreifen, die mögliche Angriffe erkennen und melden kann und die Sicherheitsstrategie so untermauert. Diese Tools unterstützen Threat Hunter dabei, Systeme oder Netzwerke genauer zu untersuchen, um mehr Belege für einen Sicherheitsvorfall zu finden.
Technologielösungen wie Next-Gen-Endpoint-Security und Firewalls sind wichtige Schutzebenen. Sie helfen dabei, komplexe, manuell gesteuerte Angriffe zu stoppen.
Die meisten Unternehmen nutzen diese Tools bereits und erfassen viele der Telemetrie-Rohdaten, mit denen Threat Hunter Risiken bewerten und bei Bedarf umfassendere Analysen vornehmen.
Endpoint-, Firewall-, Identity-, E-Mail-, Cloud- und Netzwerksicherheitslösungen bieten wertvolle Einblicke, mit denen Threat Hunter komplexe Angriffe erkennen und darauf reagieren können.
Wenn sich die Threat Hunter einen Überblick verschafft haben, gewinnen sie aus Sicherheitstelemetriedaten wertvolle Erkenntnisse. Dies erfordert besonderes Fachwissen. Threat Hunter nutzen Telemetriedaten, um schnellere und fundiertere Entscheidungen über das weitere Vorgehen zu treffen. Viele Technologien generieren durchaus Sicherheitswarnungen und -einblicke, die für erfahrene Analysten sehr hilfreich sind. Die Nutzung dieser Daten ist jedoch hochgradig komplex. Hier kommen hochqualifizierte Threat Hunter ins Spiel.
Threat Hunter durchforsten riesige Datenmengen mit Hilfe von Telemetrie-Tools und automatisierter Sicherheitssoftware. Sie nutzen die von MDR-Plattformen (Managed Detection and Response), SIEM-Lösungen (Security Information and Event Management) und Sicherheitsanalyse-Tools erfassten Daten als Grundlage für ihre Suche.
Außerdem greifen sie auf EDR- (Endpoint Detection and Response) und XDR-Lösungen (Extended Detection and Response) zurück. Diese Lösungen ermöglichen es den Threat Huntern, verdächtiges Verhalten schnell zu erkennen und eingehend zu analysieren. EDR-Software liefert Daten von allen Endpoints in der Umgebung. XDR dagegen konsolidiert Signale aus der gesamten IT-Umgebung, einschließlich Firewall-, Mobil-, E-Mail- und Cloud-Sicherheitslösungen.
Wer sind Threat Hunter und über welche Kompetenzen verfügen sie?
Threat Hunting ist ein hochkomplexer Vorgang. Dementsprechend verfügen professionelle Threat Hunter über spezielle Fähigkeiten und Fertigkeiten.
Erfolgreiche Threat Hunter müssen unter anderem folgende Eigenschaften mitbringen:
- Intellektuelle Neugierde: Bedrohungssuchen gleichen nicht selten der sprichwörtlichen Suche nach einer Nadel im Heuhaufen. Threat Hunter verbringen oft Tage damit, nach Bedrohungen zu suchen, und wenden dabei zahlreiche Methoden an. Sie müssen von Natur aus neugierig und kreativ sein, um den Überblick zu behalten und Probleme zu lösen.
- Umfassende Cybersecurity-Erfahrung: Threat Hunting ist eine der komplexesten Aufgaben im Bereich Cybersicherheit. Threat Hunter müssen über Erfahrung im Bereich Cybersecurity sowie grundlegende Kenntnisse der gängigsten Angriffsvektoren verfügen.
- Kenntnis der Bedrohungslandschaft: Threat Hunter halten sich über die neuesten Bedrohungstrends auf dem Laufenden, da diese sich ständig weiterentwickeln.
- Die Denkweise eines Hackers: Eine der wichtigsten Stärken eines erfolgreichen Threat Hunters ist die Fähigkeit, wie ein Hacker zu denken.
- Kompetenz im Bereich Technischer Kommunikation: Threat Hunter müssen alle Ergebnisse im Rahmen des Analyseprozesses protokollieren. Sie müssen komplexe Inhalte Stakeholdern mit und ohne fundierten technischen Kenntnissen nahebringen können.
- Know-how im Bereich Betriebssysteme und Netzwerke: Neben der Cybersecurity-Expertise sind fortgeschrittene Kenntnisse der gängigen Betriebssysteme und Netzwerk-Tools unerlässlich.
- Programmier-/Skripterfahrung: Diese ist erforderlich, damit Threat Hunter Programme erstellen, Aufgaben automatisieren, Protokolle analysieren und Datenanalysen durchführen können, die sie bei ihren Untersuchungen unterstützen und voranbringen.
Leider sind Sicherheitsexperten mit diesem komplexen Skill-Set rar gesät. Zudem ist das Gehaltsniveau bei erfahrenen Threat Huntern sehr hoch. Viele Unternehmen lassen sich beim Threat Hunting von MDRs oder MSSPs unterstützen, da diese Anbieter mit größerer Wahrscheinlichkeit über Mitarbeiter mit den erforderlichen Fachkenntnissen verfügen, allerdings zu geringeren Kosten.
Wie kann ich mich auf ein Threat-Hunting-Programm vorbereiten?
Eine solide Vorbereitung ist der Schlüssel zum Erfolg bei jeder Cybersecurity-Maßnahme. Threat Hunts sind da keine Ausnahme. Egal, ob Sie Ihre Threat Hunts unternehmensintern selbst verwalten oder auslagern – Ihr Unternehmen muss für diese Aufgabe gerüstet sein. Es ist wichtig, die richtigen Grundlagen zu schaffen, bevor Sie mit dem Threat Hunting beginnen.
Die folgenden fünf Schritte verhelfen Ihrem Unternehmen zu erfolgreichem Threat Hunting:
- Reifegrad Ihrer aktuellen Cybersecurity Operations ermitteln. Durch die Zuordnung Ihrer Prozesse zu einem Cybersecurity-Reifegradmodell (z. B. CMMC) können Sie einfach feststellen, wie gut Sie für das Threat Hunting gerüstet sind (oder nicht). Darüber hinaus sollten Sie Ihren Sicherheitsstatus überprüfen, um Ihre Anfälligkeit für Bedrohungen einzuschätzen.
- Entscheiden, wie Sie das Thema Threat Hunting angehen möchten. Sobald Sie Ihre Cyber-Reife ermittelt haben, können Sie entscheiden, ob Sie Ihr Threat Hunting intern leisten, komplett auslagern oder eine Kombination aus internen und externen Ressourcen nutzen möchten.
- Technologielücken erkennen. Überprüfen Sie Ihre bestehenden Tools und ermitteln Sie, was Sie sonst noch für effektives Threat Hunting benötigen. Wie effektiv ist Ihre Abwehrtechnologie? Umfasst oder unterstützt sie Threat-Hunting-Funktionen?
- Qualifikationslücken erkennen. Threat Hunting erfordert Spezialkenntnisse. Wenn Sie intern nicht über die einschlägige Expertise verfügen, sollten Sie Schulungen in Erwägung ziehen, um sich die erforderlichen Kenntnisse anzueignen. Ziehen Sie außerdem die Zusammenarbeit mit einem externen Anbieter in Betracht, der Kompetenzen in Ihrem Team ergänzen kann.
- Incident-Response-Plan aufstellen und implementieren. Ein detaillierter Incident-Response-Plan, in dessen Rahmen jede Reaktion erfasst und kontrolliert wird, ist unerlässlich. Ein gut vorbereiteter und durchdachter Reaktionsplan, den alle betroffenen Parteien sofort umsetzen können, kann die Folgen eines Angriffs auf Ihr Unternehmen erheblich abmildern.
Sophos zu Threat Hunting
MDR-Anbieter wie Sophos Managed Detection and Response (MDR) bieten zahlreiche Vorteilen gegenüber einem internen Threat-Hunting-Operations-Programm. Der wichtigste Vorteil ist in den meisten Fällen die umfangreiche Expertise.
Das Sophos-MDR-Team verfügt über tausende Stunden Erfahrung im Umgang mit Cyberangriffen. Es bietet 24/7-Support weltweit. Sie möchten mehr darüber erfahren, wie Sophos die Threat-Hunting-Projekte Ihres Unternehmens unterstützen kann?
Nehmen Sie noch heute Kontakt zu Sophos auf
Verwandtes Sicherheitsthema: Welche Arten von Cyber-Bedrohungsakteuren gibt es?
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)



